DanaBot Malware Network Smashed, 16 Face Charges in $50M Cybercrime Ring
Federal authorities have dismantled the infrastructure supporting the DanaBot malware, a sophisticated threat allegedly controlled by a Russian cybercrime syndicate. The Justice Department also unsealed indictments against 16 individuals accused of developing and distributing the malware, which is linked to cybercrimes causing over $50 million in damages worldwide.
DanaBot Botnet Disrupted: Feds Charge 16 in Global Malware Scheme
Big news from the U.S. Department of Justice (DoJ) this week: they've taken down the online infrastructure linked to DanaBot, a nasty piece of malware also known as DanaTools. They've also unsealed charges against 16 individuals allegedly involved in creating and spreading the malware. According to the DoJ, this whole operation was run by a cybercrime group based in Russia.
The DoJ estimates that DanaBot infected over 300,000 computers worldwide, causing at least $50 million in damages through fraud and ransomware attacks. Two of the accused, Aleksandr Stepanov (aka JimmBee), 39, and Artem Aleksandrovich Kalinkin (aka Onix), 34, both from Novosibirsk, Russia, are still on the run.
Stepanov is facing a laundry list of charges, including conspiracy, wire fraud, bank fraud, identity theft, and unauthorized computer access. Kalinkin is charged with conspiracy related to unauthorized computer access and impairment.
Here's a twist: the criminal complaint reveals that several of the defendants, including Kalinkin, accidentally infected their *own* computers with DanaBot! Oops.
As the complaint [PDF] puts it: "In some cases, such self-infections appeared to be deliberately done in order to test, analyze, or improve the malware." But sometimes, it seems, they just messed up. A hazard of the trade, perhaps?
And the irony doesn't stop there. The accidental infections often led to sensitive data being stolen *from the criminals themselves* and stored on DanaBot's servers. Talk about a security fail!
If convicted, Kalinkin could face a whopping 72 years in prison, while Stepanov could get five. This takedown was part of Operation Endgame, which also involved seizing DanaBot's command-and-control (C2) servers, including virtual servers hosted in the U.S.
The DoJ explained that DanaBot spread through spam emails with malicious attachments or links. Infected computers became part of a botnet, allowing the criminals to remotely control them in a coordinated fashion.
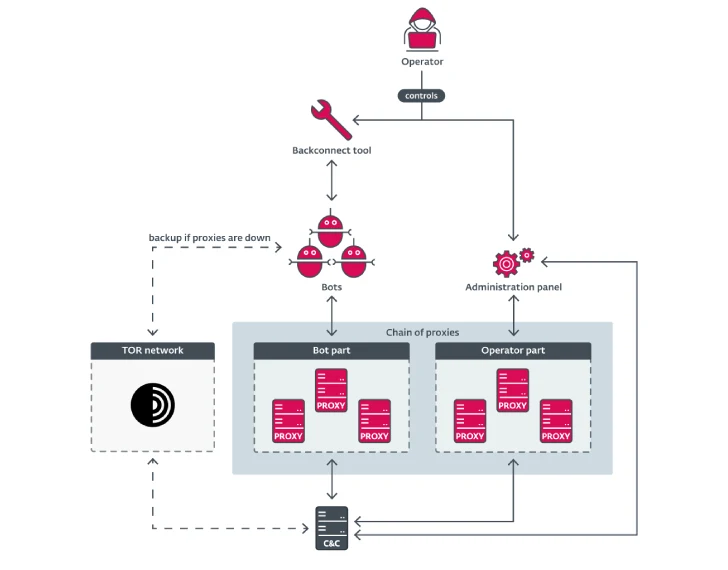
Example of typical Danabot infrastructure
DanaBot: Malware-as-a-Service
Like the recently dismantled Lumma Stealer malware, DanaBot operated on a malware-as-a-service (MaaS) model. This means the administrators leased out access to the malware for a monthly fee, ranging from $500 to several thousand dollars. Tracked as Scully Spider and Storm-1044, it's a versatile tool similar to Emotet, TrickBot, QakBot, and IcedID, capable of stealing data and delivering other malicious payloads, like ransomware.
This Delphi-based malware can steal data, hijack banking sessions, grab device info, browsing history, credentials, and even cryptocurrency wallet info. It also offers remote access, keystroke logging, and video capture. It first appeared in May 2018 as a banking trojan.
CrowdStrike noted that DanaBot initially targeted victims in Ukraine, Poland, Italy, Germany, Austria, and Australia before expanding to the U.S. and Canada in late 2018. Its popularity grew thanks to its modular design and capabilities like web injects, info stealing, keylogging, screen recording, and hidden virtual network computing (HVNC).
A Tiered Infrastructure
According to Black Lotus Labs and Team Cymru, DanaBot used a multi-layered communication system. Traffic between victims and the botnet controllers was routed through two or three server tiers. They observed five to six active tier-2 servers at any given time, with most victims located in Brazil, Mexico, and the United States.
"The operators have shown their commitment to their craft, adapted to detection and changes in enterprise defense, and with later iterations, insulating the C2s in tiers to obfuscate tracking," the companies said. "Throughout this time, they have made the bot more user-friendly with structured pricing and customer support." (Yes, even cybercriminals apparently value customer service!)
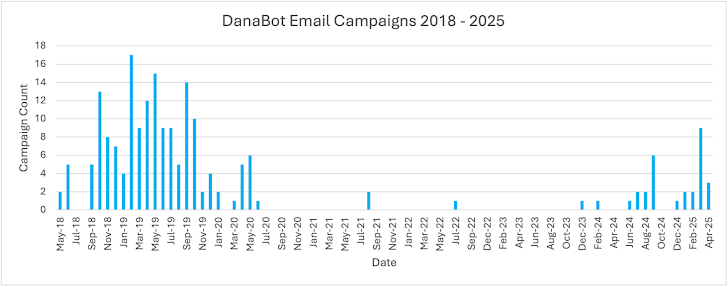
Number of DanaBot campaigns observed in Proofpoint email threat data from May 2018 to April 2025
Data gathered by Proofpoint indicates that DanaBot was largely absent from email threats between July 2020 and June 2024. This suggests the criminals switched to other distribution methods, like SEO poisoning and malvertising.
The DoJ also revealed that DanaBot's operators ran a second version specifically designed to target military, diplomatic, government, and related organizations in North America and Europe. This variant, which surfaced in January 2021, could record all activity on an infected device and send the data to a separate server.
This takedown is a good reminder that malware like DanaBot can cause serious harm to hundreds of thousands of individuals and organizations.




