TikTok Users Targeted in Malware Attack Exploiting 'ClickFix' Trick
Cybercriminals are now using TikTok videos to spread dangerous malware like Vidar and StealC, leveraging a social engineering tactic called 'ClickFix' to trick unsuspecting users into downloading malicious software. This latest campaign highlights the growing trend of threat actors exploiting popular social media platforms for malware distribution.

Latrodectus Malware Uses ClickFix Technique to Spread
The malware Latrodectus is the latest to jump on the ClickFix bandwagon. This social engineering trick is now a popular way to spread malicious software.
Expel researchers explain that "ClickFix is extra dangerous because it lets the malware run directly in your computer's memory, instead of saving files to your hard drive." In their report, shared with The Hacker News, they added, "This makes it harder for your browser or security tools to catch it."
So, what is Latrodectus? Think of it as the successor to IcedID. It's basically a downloader for other nasty stuff, like ransomware. Proofpoint and Team Cymru were the first to spot it back in April 2024.
Interestingly, Latrodectus got hit during Operation Endgame. This Europol takedown seized hundreds of servers and domains linked to various malware, including Bumblebee, QakBot, and TrickBot.
But it's back. Expel noticed new Latrodectus attacks in May 2025. Users are tricked into copying and pasting a PowerShell command from a dodgy website. It's a common way to spread malware these days.
Expel says, "When you run these commands, they try to install a file from a remote website using MSIExec, and then run it in memory. This way, the attacker doesn't have to save the file to your computer, avoiding detection by your browser or antivirus software."
The MSI installer actually contains a legitimate NVIDIA application. This is used to sneak in a malicious DLL file, which then downloads the real payload using curl.
What can you do? Experts suggest disabling the Windows Run program through Group Policy Objects (GPOs), or disabling the "Windows + R" hotkey via a Registry tweak.
From ClickFix to TikTok
Meanwhile, Trend Micro uncovered a new social engineering campaign. This one ditches the fake CAPTCHA pages and uses TikTok videos. These videos, likely made with AI, push the Vidar and StealC info-stealers. They tell users to run malicious commands to activate Windows, Office, CapCut, and Spotify.
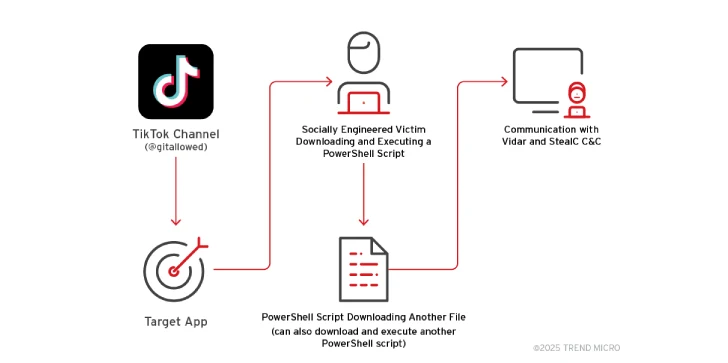
These videos were posted from accounts like @gitallowed and @digitaldreams771, but they're gone now. One video, promising to "boost your Spotify experience instantly," racked up almost half a million views!
This is a new level of ClickFix. People searching for ways to activate pirated apps are shown how to open the Windows Run dialog (Windows + R), launch PowerShell, and run the dangerous command in the video.
Security researcher Junestherry Dela Cruz warns, "Threat actors are now using TikTok videos that are potentially generated using AI-powered tools to socially engineer users into executing PowerShell commands under the guise of guiding them to activate legitimate software or unlock premium features."
"This campaign highlights how attackers are ready to weaponize whichever social media platforms are currently popular to distribute malware."
Fake Ledger Apps Used to Steal Mac Users' Seed Phrases
There's more! Researchers have found four separate malware campaigns using fake Ledger Live apps to steal seed phrases and drain cryptocurrency wallets. This has been happening since August 2024.
The attacks use malicious DMG files. When opened, they run AppleScript to steal passwords and Apple Notes data, and then download a fake version of Ledger Live. This fake app tells users there's an account problem and asks for their seed phrase for recovery. Of course, the seed phrase goes straight to the attacker.
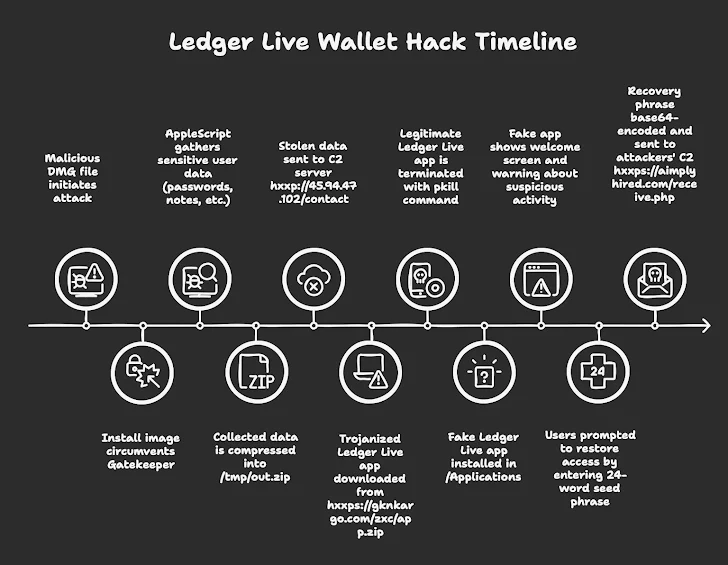
Moonlock Lab, who discovered the campaign, says the fake apps use macOS stealer malware like Atomic macOS Stealer (AMOS) and Odyssey. Odyssey introduced this seed phrase phishing scheme in March 2025. This is linked to a macOS info-stealer campaign targeting Ledger Live users through PyInstaller-packed binaries, as reported by Jamf earlier this month.
MacPaw's cybersecurity division notes, "On dark web forums, chatter around anti-Ledger schemes is growing. The next wave is already taking shape. Hackers will continue to exploit the trust crypto owners place in Ledger Live."