ViciousTrap Turns Thousands of Cisco Devices into Global Honeypot
A threat actor dubbed ViciousTrap has built a massive, globally distributed honeypot by exploiting a vulnerability in Cisco network devices. Researchers have uncovered a network of nearly 5,300 compromised devices spanning 84 countries, all seemingly repurposed to lure and study malicious activity.

ViciousTrap: Hackers Turn Thousands of Routers into Global Honeypot Network
Cybersecurity researchers have uncovered a sneaky operation: a threat actor, going by the name ViciousTrap, has reportedly compromised nearly 5,300 network edge devices spread across 84 countries. Their goal? To create a massive, worldwide honeypot-like network.
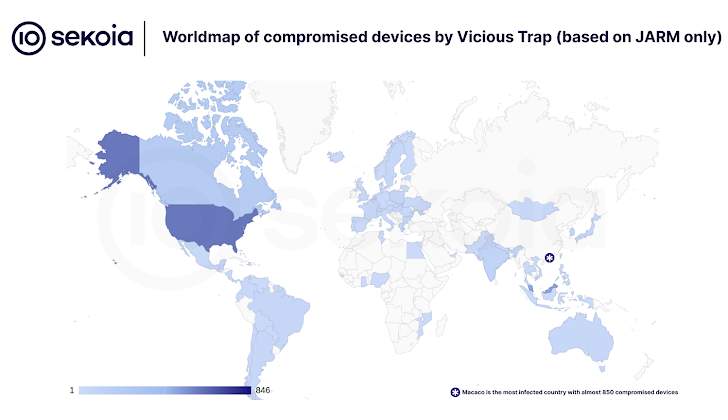
So, how are they doing it? It seems ViciousTrap is exploiting a serious security vulnerability (CVE-2023-20118) in a range of Cisco Small Business routers, including the RV016, RV042, RV042G, RV082, RV320, and RV325 models. By taking advantage of this flaw, they're essentially turning these routers into unwitting participants in their honeypot scheme. The majority of compromised devices appear to be located in Macau, with around 850 infections.
Sekoia, a cybersecurity firm, explains that the attack involves a shell script they've dubbed "NetGhost." This script redirects traffic from specific ports on the compromised router to infrastructure controlled by the attackers, allowing them to snoop on network activity. Think of it as a digital wiretap on a massive scale.
Interestingly, the exploitation of this Cisco vulnerability (CVE-2023-20118) was previously linked to another botnet called PolarEdge. French cybersecurity researchers made that connection.
While it's not yet clear if ViciousTrap and PolarEdge are related, there's a strong suspicion that ViciousTrap is setting up its honeypot infrastructure by targeting a wide array of internet-facing devices. This includes not just SOHO routers, but also SSL VPNs, DVRs, and BMC controllers from over 50 brands like Araknis Networks, ASUS, D-Link, Linksys, and QNAP.
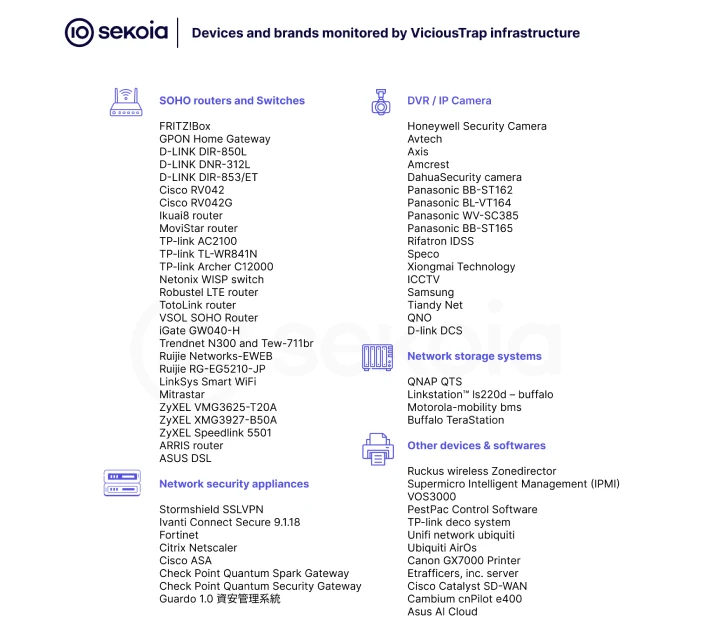
The idea, according to Sekoia, is that "This setup would allow the actor to observe exploitation attempts across multiple environments and potentially collect non-public or zero-day exploits, and reuse access obtained by other threat actors." In other words, they're building a system to learn about new vulnerabilities and potentially exploit them themselves.
The attack chain is pretty clever. First, they exploit CVE-2023-20118 to download and execute a bash script using ftpget. This script then reaches out to an external server to grab the wget binary. Next, they exploit the Cisco flaw *again*, this time to execute a second script retrieved using that wget.
This second-stage script, "NetGhost," redirects network traffic from the compromised device to the attacker's infrastructure, enabling what's known as adversary-in-the-middle (AitM) attacks. It also tries to cover its tracks by removing itself from the infected host.
Sekoia notes that all exploitation attempts seem to originate from a single IP address ("101.99.91[.]151"), with activity dating back to March 2025. In a curious twist, ViciousTrap apparently repurposed an undocumented web shell previously used in the PolarEdge botnet attacks for their own purposes.
Security researchers Felix Aimé and Jeremy Scion suggest, "This assumption aligns with the attacker's use of NetGhost. The redirection mechanism effectively positions the attacker as a silent observer, capable of collecting exploitation attempts and, potentially, web shell accesses in transit."
More recently, ASUS routers have also been targeted, but from a different IP address ("101.99.91[.]239"). However, in these cases, the attackers haven't been observed creating honeypots on the infected devices. All the IP addresses used in this campaign are located in Malaysia and belong to a hosting provider called Shinjiru.
Based on some clues, like overlaps with the GobRAT infrastructure and the redirection of traffic to assets in Taiwan and the United States, the actor is believed to be of Chinese-speaking origin.
Sekoia concludes that "The final objective of ViciousTrap remains unclear even [though] we assess with high confidence that it's a honeypot-style network." The mystery of what they ultimately plan to do with this massive network remains unsolved.




