Massive Browser Extension Spy Ring Uncovered Affecting Millions
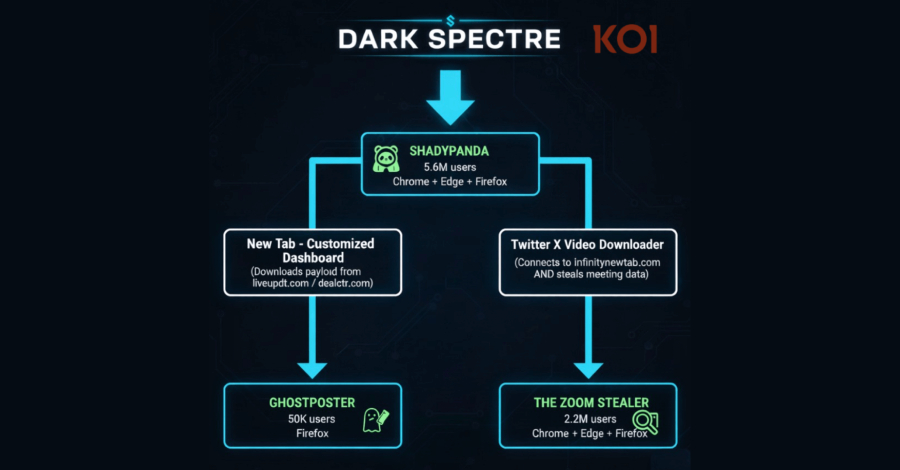
A sophisticated network of malicious browser extensions, dubbed DarkSpectre, has been exposed after infecting over two million users across Chrome, Edge, and Firefox. Security researchers have linked DarkSpectre to previous campaigns known as ShadyPanda and GhostPoster, revealing a persistent and widespread threat targeting unsuspecting web users.
A Chinese threat actor, dubbed DarkSpectre by researchers at Koi Security, is behind a series of malicious browser extension campaigns that have impacted a staggering 2.2 million users. These extensions, targeting Chrome, Edge, and Firefox, are linked to previous campaigns known as ShadyPanda and GhostPoster. In total, these campaigns have ensnared over 8.8 million unsuspecting users over the past seven years – a truly massive scale.
According to Koi Security's analysis, DarkSpectre's operations are far-reaching and cleverly disguised.
ShadyPanda: Data Theft and Affiliate Fraud
ShadyPanda, uncovered earlier this month, targeted users across all three major browsers. The goal? Data theft, search query hijacking, and affiliate fraud. It’s estimated that ShadyPanda affected 5.6 million users. And get this: researchers identified 1.3 million *new* victims tied to over 100 extensions related to this campaign.
One particularly sneaky tactic involved an Edge add-on called "New Tab - Customized Dashboard." This extension included a logic bomb, a malicious payload that lay dormant for three days before activating. This delay likely aimed to bypass initial security reviews.
What's even more alarming is that nine of these extensions are currently active, while 85 others are "dormant sleepers." These seemingly harmless extensions are designed to build a user base before being weaponized through malicious updates – some after lying low for over five years, according to Koi.
GhostPoster: Targeting Firefox with Deceptive Utilities
GhostPoster mainly sets its sights on Firefox users. This campaign utilizes what appear to be harmless utilities and VPN tools. Underneath the surface, however, lurks malicious JavaScript code designed to hijack affiliate links, inject tracking code, and commit click and ad fraud. The investigation uncovered even more compromised add-ons, including a Google Translate extension for Opera (developed by "charliesmithbons") boasting nearly one million installs.
The Zoom Stealer: Corporate Espionage in Disguise
Perhaps the most concerning of DarkSpectre's campaigns is The Zoom Stealer. This operation involves 18 extensions across Chrome, Edge, and Firefox specifically designed for corporate meeting intelligence. These extensions stealthily collect sensitive data from online meetings, including URLs with embedded passwords, meeting IDs, topics, descriptions, scheduled times, and registration status.
The list of identified extensions and their corresponding IDs is below:
Google Chrome:
- Chrome Audio Capture (kfokdmfpdnokpmpbjhjbcabgligoelgp)
- ZED: Zoom Easy Downloader (pdadlkbckhinonakkfkdaadceojbekep)
- X (Twitter) Video Downloader (akmdionenlnfcipmdhbhcnkighafmdha)
- Google Meet Auto Admit (pabkjoplheapcclldpknfpcepheldbga)
- Zoom.us Always Show "Join From Web" (aedgpiecagcpmehhelbibfbgpfiafdkm)
- Timer for Google Meet (dpdgjbnanmmlikideilnpfjjdbmneanf)
- CVR: Chrome Video Recorder (kabbfhmcaaodobkfbnnehopcghicgffo)
- GoToWebinar & GoToMeeting Download Recordings (cphibdhgbdoekmkkcbbaoogedpfibeme)
- Meet auto admit (ceofheakaalaecnecdkdanhejojkpeai)
- Google Meet Tweak (Emojis, Text, Cam Effects) (dakebdbeofhmlnmjlmhjdmmjmfohiicn)
- Mute All on Meet (adjoknoacleghaejlggocbakidkoifle)
- Google Meet Push-To-Talk (pgpidfocdapogajplhjofamgeboonmmj)
- Photo Downloader for Facebook, Instagram, + (ifklcpoenaammhnoddgedlapnodfcjpn)
- Zoomcoder Extension (ebhomdageggjbmomenipfbhcjamfkmbl)
- Auto-join for Google Meet (ajfokipknlmjhcioemgnofkpmdnbaldi)
Microsoft Edge:
- Edge Audio Capture (mhjdjckeljinofckdibjiojbdpapoecj)
Mozilla Firefox:
- Twiter X Video Downloader ({7536027f-96fb-4762-9e02-fdfaedd3bfb5}, published by "invaliddejavu")
- x-video-downloader ([email protected], published by "invaliddejavu")
Many of these extensions masquerade as tools for popular video conferencing applications like Google Meet, Zoom, and GoTo Webinar. They discreetly siphon meeting links, credentials, and participant lists via a WebSocket connection in real-time.
Furthermore, these malicious add-ons can harvest details about webinar speakers and hosts, including their names, titles, bios, profile photos, company affiliations, logos, promotional graphics, and session metadata – all collected whenever a user visits a webinar registration page with one of these extensions installed.
These add-ons request access to over 28 video conferencing platforms – including Cisco WebEx, Google Meet, GoTo Webinar, Microsoft Teams, and Zoom – regardless of whether such access is actually required.
"This isn't consumer fraud - this is corporate espionage infrastructure," researchers Tuval Admoni and Gal Hachamov stated. "The Zoom Stealer represents something more targeted: systematic collection of corporate meeting intelligence. Users got what was advertised. The extensions earned trust and positive reviews. Meanwhile, surveillance ran silently in the background."
Koi Security warns that the collected information could be sold to other malicious actors, fueling corporate espionage, social engineering attacks, and large-scale impersonation schemes.
Chinese Connections: Unveiling the Culprits
The attribution to Chinese actors is based on several key indicators: consistent use of command-and-control (C2) servers hosted on Alibaba Cloud, Internet Content Provider (ICP) registrations tied to Chinese provinces, code artifacts containing Chinese-language strings and comments, and fraud schemes specifically targeting Chinese e-commerce platforms like JD.com and Taobao.
"DarkSpectre likely has more infrastructure in place right now - extensions that look completely legitimate because they are legitimate, for now," Koi warned. "They're still in the trust-building phase, accumulating users, earning badges, waiting."