Chinese Hackers Target Critical Systems Worldwide Using SAP Flaw
Multiple Chinese government-linked hacking groups are actively exploiting a recently discovered vulnerability in SAP NetWeaver, putting critical infrastructure networks at risk. The flaw, identified as CVE-2025-31324, has already been used to compromise hundreds of systems globally.

A critical security vulnerability in SAP NetWeaver is under active exploitation, and multiple Chinese state-sponsored hacking groups are believed to be behind it. They're going after some pretty important targets, too.
Security researchers at EclecticIQ discovered that these actors are exploiting CVE-2025-31324, a serious flaw that allows attackers to upload files without needing to authenticate. That means they can remotely execute code on vulnerable systems. Arda Büyükkaya, an EclecticIQ researcher, explained it all in their recent analysis.
So, who's in the crosshairs? We're talking natural gas suppliers in the UK, water and waste management facilities, medical device manufacturers in the US, oil and gas companies, and even government ministries in Saudi Arabia.
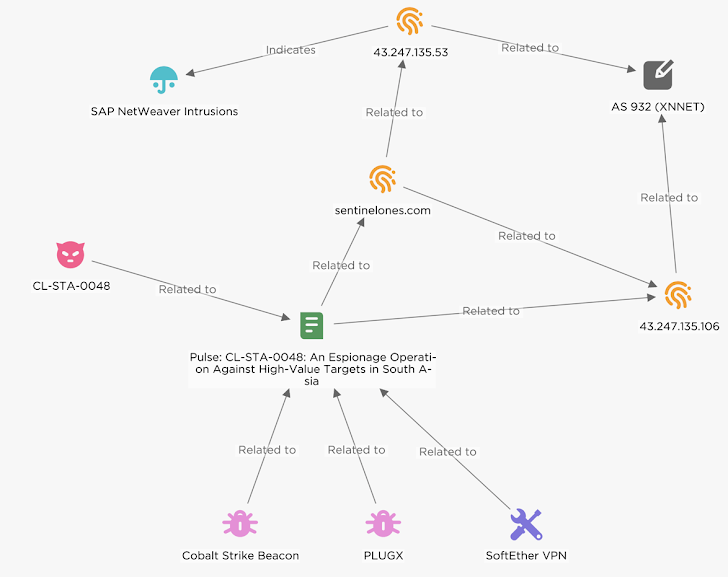
The evidence comes from a publicly accessible directory found on a server controlled by the attackers (15.204.56[.]106). This directory contained logs that revealed the attackers' activities across numerous compromised systems.
EclecticIQ points the finger at several Chinese hacking groups, including UNC5221, UNC5174, and CL-STA-0048. CL-STA-0048, in particular, has a history of targeting South Asia by exploiting vulnerabilities in web servers to install backdoors.
The researchers also uncovered a broader scanning and exploitation campaign by another, as-yet-unnamed, Chinese group targeting SAP NetWeaver. The server at 15.204.56[.]106 contained files like:
CVE-2025-31324-results.txt: Listing 581 backdoored SAP NetWeaver instances.服务数据_20250427_212229.txt: Listing 800 domains running SAP NetWeaver, likely future targets.
Büyükkaya sums it up: "The exposed open-dir infrastructure reveals confirmed breaches and highlights the group's planned targets, offering clear insight into both past and future operations."
After exploiting CVE-2025-31324, the attackers deploy web shells to maintain access and run commands.
Here's a breakdown of how the different Chinese groups are using the vulnerability:
- CL-STA-0048: Trying to establish a reverse shell to
43.247.135[.]53, an IP address they've used before. - UNC5221: Using a web shell to deploy KrustyLoader, malware that can deliver other payloads like Sliver.
- UNC5174: Using a web shell to download SNOWLIGHT, a loader that fetches a remote access trojan called VShell and a backdoor named GOREVERSE.
The bottom line? "China-linked APTs are highly likely to continue targeting internet-exposed enterprise applications and edge devices to establish long-term strategic and persistence access to critical infrastructure networks globally," warns Büyükkaya.
Why SAP NetWeaver? "Their focus on widely used platforms like SAP NetWeaver is a strategic move, as these systems are deeply integrated into enterprise environments and often host unpatched vulnerabilities."
SAP Patched Another NetWeaver Flaw in May 2025
Just days before this report, another Chinese hacking group, dubbed Chaya_004, was linked to exploiting CVE-2025-31324 to deploy SuperShell, a Go-based reverse shell.
SAP security firm Onapsis notes "seeing significant activity from attackers who are using public information to trigger exploitation and abuse web shells placed by the original attackers, who have currently gone dark."
Digging deeper, researchers uncovered another critical vulnerability in NetWeaver's Visual Composer Metadata Uploader component. CVE-2025-42999 (CVSS score: 9.1) is a deserialization vulnerability that could be exploited by a privileged user to upload malicious content.
The Recommendation? If you're running SAP NetWeaver, update to the latest version ASAP. Given the active exploitation, you don't want to wait on this one.