GoAnywhere MFT Zero-Day Exploited Before Patch, Researchers Say
A critical vulnerability in Fortra's GoAnywhere Managed File Transfer (MFT) software, carrying the highest severity score, was actively exploited as a zero-day a week before its public disclosure, according to cybersecurity firm watchTowr Labs. The researchers report having "credible evidence" suggesting malicious actors targeted the flaw, which has a CVSS score of 10, starting around September 10, 2025.

Cybersecurity firm watchTowr Labs is reporting that the recently revealed security vulnerability in Fortra GoAnywhere Managed File Transfer (MFT) software was being actively exploited as far back as September 10, 2025 – a full week *before* the public knew anything about it.
According to watchTowr CEO Benjamin Harris, this isn't just another high-severity (CVSS 10.0) flaw in a system already popular with APT groups and ransomware gangs. "This is not 'just' a CVSS 10.0 flaw in a solution long favored by APT groups and ransomware operators – it is a vulnerability that has been actively exploited in the wild since at least September 10, 2025," Harris told The Hacker News.
The vulnerability in question? It's CVE-2025-10035, a deserialization flaw in the License Servlet. This could allow attackers to inject commands without needing authentication. Fortra rolled out GoAnywhere version 7.8.4 (or Sustain Release 7.6.3) last week to patch things up.
watchTowr's analysis explains that the issue stems from sending a specific HTTP GET request to "/goanywhere/license/Unlicensed.xhtml/". This lets you directly interact with the License Servlet ("com.linoma.ga.ui.admin.servlet.LicenseResponseServlet"), which is exposed at "/goanywhere/lic/accept/<GUID>" using a GUID from the initial response.
With this authentication bypassed, attackers can exploit weak deserialization protections in the License Servlet, leading to command injection. How *exactly* this happens is still a bit of a puzzle, researchers Sonny Macdonald and Piotr Bazydlo pointed out.
Rapid7, another cybersecurity vendor, also analyzed CVE-2025-10035. They suggest it's not just one deserialization vulnerability, but a chain of three separate problems:
- An access control bypass, known since 2023.
- The unsafe deserialization vulnerability CVE-2025-10035 itself.
- An unknown issue about how attackers figure out a specific private key.
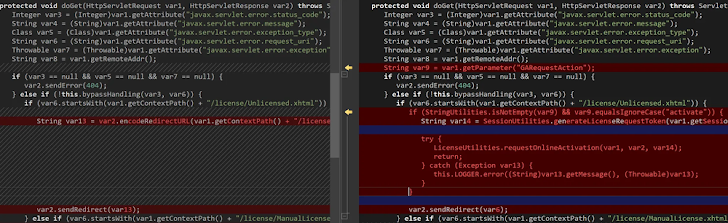
In a follow-up report published on Thursday, watchTowr shared evidence of actual exploitation, including a stack trace showing how to create a backdoor account. Here's the sequence:
- Trigger the vulnerability to get remote code execution (RCE).
- Use RCE to create a GoAnywhere user named "admin-go".
- Create a web user using the new account.
- Use the web user to upload and run more code, including SimpleHelp and an unknown implant ("zato_be.exe").
The company also noted that the malicious activity originated from IP address 155.2.190[.]197. VirusTotal reports this IP was flagged for brute-force attacks against Fortinet FortiGate SSL VPNs in early August 2025. However, watchTowr hasn't seen that kind of activity from the IP address on their own honeypots.
Bottom line: Given that this flaw is being actively exploited, it's *crucial* to apply the patch if you haven't already. We've reached out to Fortra for their take and will update this story if we get a response.