Golden Chickens Malware Upgrade Targets Crypto Wallets, Browser Data
The cybercrime group Golden Chickens is back with an evolved malware strain, TerraStealerV2, designed to pilfer browser credentials and cryptocurrency wallet data. This, along with the discovery of a related tool called TerraLogger, indicates the group is actively refining its malicious toolkit.

The notorious hacking group known as Golden Chickens seems to be upping their game. They've been linked to two brand-new malware families: TerraStealerV2 and TerraLogger. It looks like they're busy tweaking their tools and expanding their reach.
According to Recorded Future Insikt Group, "TerraStealerV2 is designed to collect browser credentials, cryptocurrency wallet data, and browser extension information." Think of it as a digital pickpocket, grabbing everything valuable it can find in your browser.
"TerraLogger, by contrast, is a standalone keylogger," they said. "It uses a common low-level keyboard hook to record keystrokes and writes the logs to local files." So, it's silently recording everything you type.
But who are the Golden Chickens? Also called Venom Spider, they're a financially motivated group tied to the infamous More_eggs malware family. They've been around since at least 2018, offering their malicious wares as a service – a kind of "malware-as-a-service" (MaaS) model.
By 2023, the group was linked to an online persona called badbullzvenom, thought to be run by folks in Canada and Romania. They've got a whole toolbox of nasty stuff, including More_eggs lite, VenomLNK, TerraLoader, and TerraCrypt.
Remember last year? Zscaler ThreatLabz uncovered new Golden Chickens activity, including a backdoor called RevC2 and a loader known as Venom Loader. These were delivered through VenomLNK.
Now, Recorded Future's research shows they're still at it, updating their stealer malware to grab even more data from browsers, crypto wallets, and browser extensions.
TerraStealerV2 is being spread in various forms – executable files, DLLs, Windows Installer packages, even shortcut files.
In all cases, the actual malicious code arrives as an OCX file (an old Microsoft thing) downloaded from a server on the internet.
"While it targets the Chrome 'Login Data' database to steal credentials, it does not bypass Application Bound Encryption (ABE) protections introduced in Chrome updates after July 2024, indicating the malware code is outdated or still under development," the researchers noted. So, it might not be the most cutting-edge, but it's still a threat.
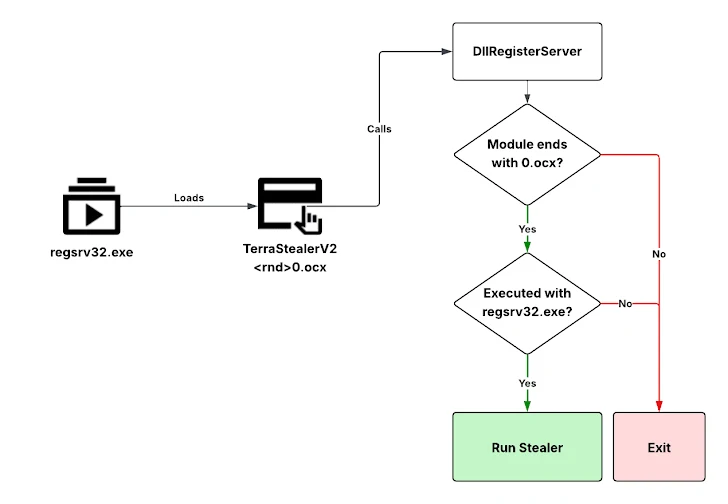
TerraStealerV2 sends stolen data to both Telegram and a website. It also uses legitimate Windows tools to try and hide its tracks.
TerraLogger, also disguised as an OCX file, is designed to record everything you type. But it can't send the data anywhere or receive commands, suggesting it's still being developed or meant to work with other malware.
"The current state of TerraStealerV2 and TerraLogger suggests that both tools remain under active development and do not yet exhibit the level of stealth typically associated with mature Golden Chickens tooling," Recorded Future pointed out.
"Given Golden Chickens' history of developing malware for credential theft and access operations, these capabilities will likely continue to evolve." So, expect them to keep refining their techniques.
This news comes as other new info-stealing malware pops up, like Hannibal Stealer, Gremlin Stealer, and Nullpoint Stealer. These are all designed to steal sensitive information.
We're also seeing updates to older malware. For example, there's a new version of StealC with better communication and encryption.
"The malware's payload delivery options have been expanded to include Microsoft Software Installer (MSI) packages and PowerShell scripts," Zscaler ThreatLabz explained.
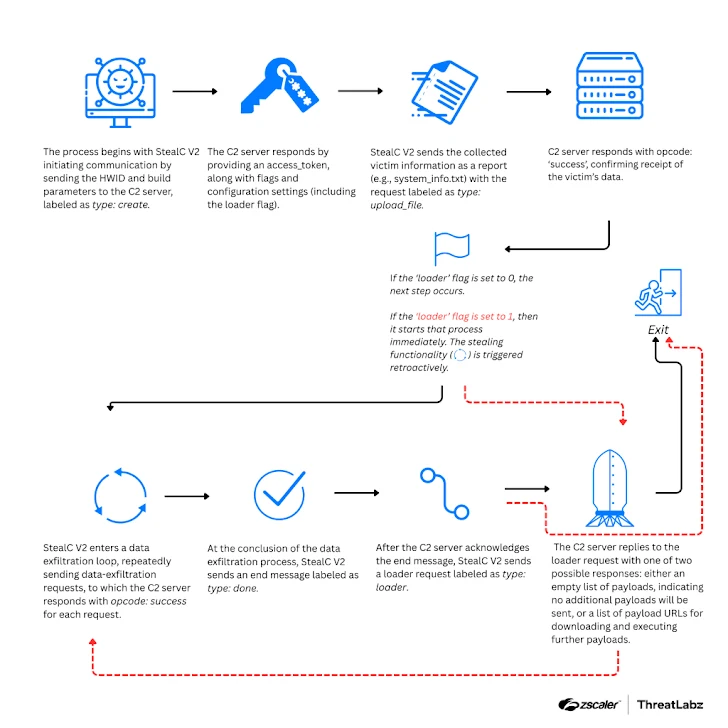
"A redesigned control panel provides an integrated builder that enables threat actors to customize payload delivery rules based on geolocation, hardware IDs (HWID), and installed software. Additional features include multi-monitor screenshot capture, a unified file grabber, and server-side brute-forcing for credentials."
StealC V2, launched in March 2025, is now spread using another malware loader called Amadey. Its control panel can even send notifications via Telegram bots and customize the message format.
"StealC V2 introduces improvements, such as enhanced payload delivery, a streamlined communications protocol with encryption, and a redesigned control panel that provides more targeted information collection," Zscaler concluded.
And it's not just StealC. Researchers have found a reworked Lumma Stealer, written in C++, being spread through social engineering – tricking users who search for cracked software, movies, or music.
"LUMMAC.V2 is an infostealer malware that targets a wide range of applications, including browsers, crypto wallets, password managers, remote desktop applications, email clients, and instant messaging applications," Google Security Operations warned.
"It steals information such as credentials, logins, emails, personal and system details, screenshots, and cookies, subsequently sending this data over HTTP in a ZIP archive." So, keep your guard up!