GoldFactory Banking Trojan Spreads Across Southeast Asia Infecting Thousands
A surge in mobile malware is hitting Indonesia, Thailand, and Vietnam as the GoldFactory cybercrime group pushes out fake government apps laden with banking Trojans. Security researchers report over 11,000 infections linked to this financially driven campaign.

A cybercrime group known as GoldFactory is at it again, this time targeting mobile users in Indonesia, Thailand, and Vietnam. They're cleverly impersonating government services to trick people into downloading malicious banking apps.
According to a new report from Group-IB, these attacks have been ongoing since October 2024. The hackers distribute modified banking applications that sneakily install Android malware onto your device.
GoldFactory, active since June 2023, first popped up on the radar last year. They're known for using custom malware like GoldPickaxe, GoldDigger, and GoldDiggerPlus, targeting both Android and iOS users.
Investigators believe GoldFactory is a well-organized, Chinese-speaking group with ties to Gigabud, another Android malware strain discovered in mid-2023. Even though their codebases differ significantly, GoldDigger and Gigabud share similar targets and landing pages.
The first wave of these attacks hit Thailand. By late 2024 and early 2025, Vietnam was targeted, and Indonesia has been under attack since mid-2025.
Group-IB has found over 300 unique modified banking apps, leading to almost 2,200 infections in Indonesia alone. Further digging uncovered over 3,000 related items, resulting in at least 11,000 infections. A whopping 63% of these fake banking apps are designed to fool Indonesian users.
How the Scam Works
The hackers impersonate government agencies and trusted local brands. They contact potential victims by phone, tricking them into installing malware via links sent through messaging apps like Zalo.
In one instance, the fraudsters pretended to be from Vietnam's power company, EVN. They told victims they had overdue bills and threatened immediate service suspension if they didn't pay. They then asked victims to add them on Zalo to receive a download link for a malicious app.
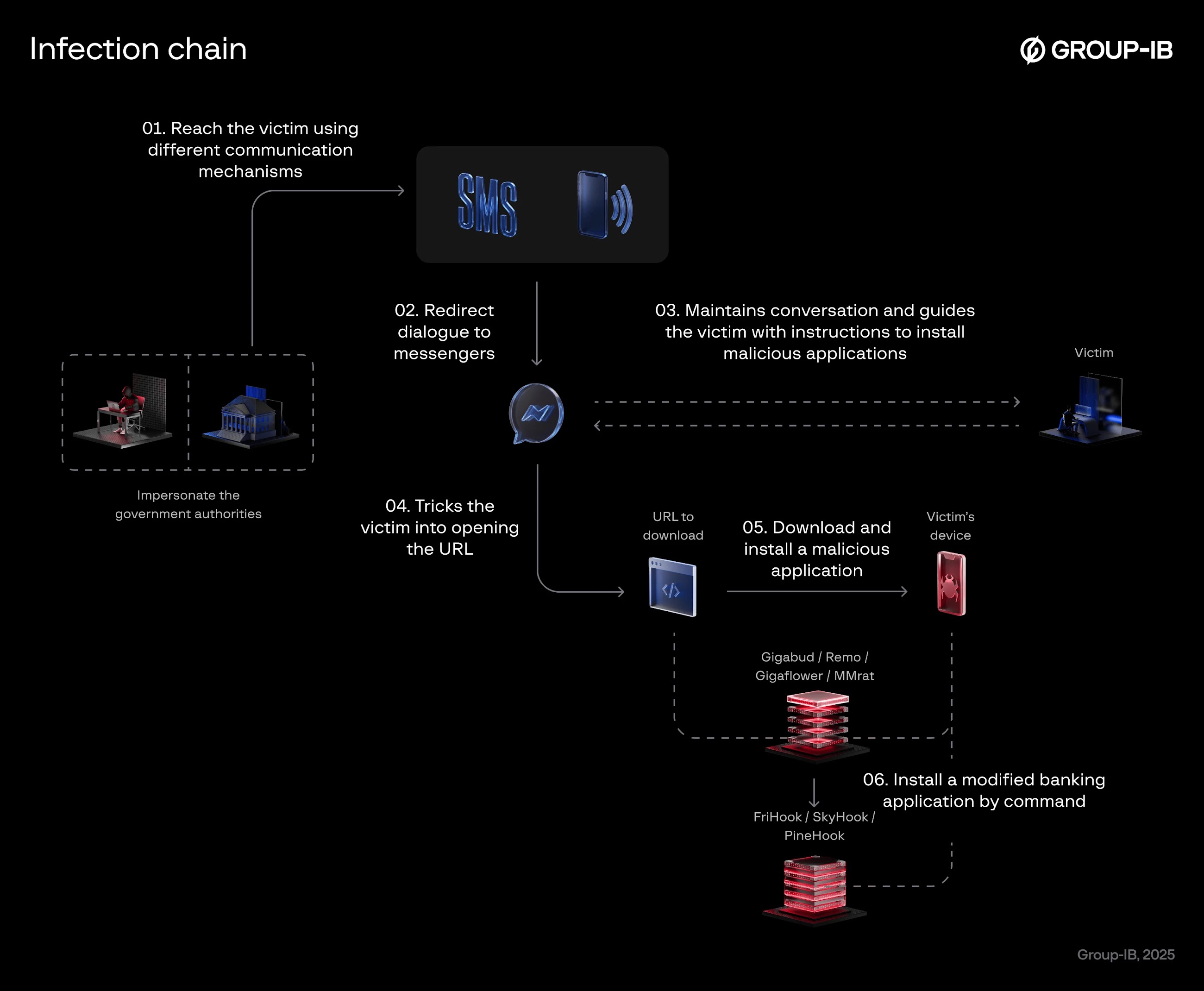
These links send victims to fake landing pages disguised as Google Play Store app listings. This leads to the installation of remote access trojans (RATs) like Gigabud, MMRat, or Remo. These RATs, which surfaced earlier this year using similar tactics, then pave the way for the main malware payload, abusing Android's accessibility services for remote control.
"The malware [...] is based on the original mobile banking applications," explained researchers Andrey Polovinkin, Sharmine Low, Ha Thi Thu Nguyen, and Pavel Naumov. "It operates by injecting malicious code into only a portion of the application, allowing the original application to retain its normal functionality. The functionality of injected malicious modules can differ from one target to another, but mainly it bypasses the original application's security features."
Essentially, the malware hooks into the app's logic to execute its malicious code. Three different malware families have been identified, each using different frameworks for runtime hooking: FriHook, SkyHook, and PineHook. Despite these differences, their functionalities overlap, allowing them to:
- Hide the list of apps with accessibility services enabled
- Prevent screencast detection
- Spoof Android app signatures
- Hide the installation source
- Implement custom integrity token providers
- Obtain victims' account balances
While SkyHook leverages the open-source Dobby framework, FriHook uses a Frida gadget injected into the banking app. PineHook, as the name suggests, utilizes a Java-based hooking framework called Pine.
A New Threat: Gigaflower
Group-IB's analysis of the malicious infrastructure used by GoldFactory also revealed a pre-release version of a new Android malware variant called Gigaflower, likely a successor to Gigabud.
Gigaflower supports around 48 commands, enabling real-time screen and device activity streaming via WebRTC. It can also weaponize accessibility services for keylogging, read user interface content, and perform gestures. It can display fake screens mimicking system updates, PIN prompts, and account registration to steal personal information. Plus, it can extract data from ID card images using a built-in text recognition algorithm.
Currently in development is a QR code scanner designed to read QR codes on Vietnamese ID cards, streamlining the data capture process.
Interestingly, GoldFactory seems to have abandoned its custom iOS trojan. Instead, they now instruct victims to borrow an Android device from a family member to continue the attack. The reason for this shift is unclear, but it's likely due to stricter security measures and app store moderation on iOS.
"While earlier campaigns focused on exploiting KYC processes, recent activity shows direct patching of legitimate banking applications to commit fraud," the researchers noted. "The use of legitimate frameworks such as Frida, Dobby, and Pine to modify trusted banking applications demonstrates a sophisticated yet low-cost approach that allows cybercriminals to bypass traditional detection and rapidly scale their operation."