Intel SGX Under Threat New Attack Steals Encryption Keys Via Memory Sniffing
Researchers have uncovered a new vulnerability that allows attackers to silently extract encryption keys from Intel's Software Guard Extensions (SGX) technology. By eavesdropping on the DDR4 memory bus, the team from Georgia Tech and Purdue University demonstrated how to bypass SGX's security protections and potentially expose sensitive data.

Researchers at Georgia Institute of Technology and Purdue University have uncovered a concerning vulnerability. They've demonstrated that Intel's Software Guard eXtensions (SGX), a security feature meant to protect sensitive data, can be bypassed on DDR4 systems. This bypass allows attackers to passively decrypt data that should be secure.
So, what exactly is SGX? It's a hardware feature in Intel server processors. It's designed to create a Trusted Execution Environment (TEE) for applications. Think of it as a secure vault within your computer. It isolates trusted code and resources within these "enclaves," supposedly preventing attackers from snooping on memory or CPU activity.
The idea is that even if the operating system itself is compromised, the data within the SGX enclave remains confidential. But this new research shows that SGX isn't as impenetrable as we thought.
"We show how one can build a device to physically inspect all memory traffic inside a computer cheaply and easily, in environments with only basic electrical tools, and using equipment easily purchased on the internet," the researchers said. "Using our interposer device against SGX's attestation mechanism, we are able to extract an SGX secret attestation key from a machine in fully trusted status, thereby breaching SGX's security."
This new method, dubbed "WireTap," is similar to the Battering RAM attack revealed recently. WireTap uses a device that sits between the CPU and the memory module, observing the data flowing between them. An attacker could install this device through a supply chain attack or by physically accessing the machine.
Essentially, the attack takes advantage of Intel's use of deterministic encryption. This allows the researchers to perform a full key recovery against Intel SGX's Quoting Enclave (QE). This effectively makes it possible to extract a critical ECDSA signing key that can then be used to sign any SGX enclave reports.
In simpler terms, attackers can exploit the predictable nature of the memory encryption to create a tool to break the security of constant-time cryptographic code.
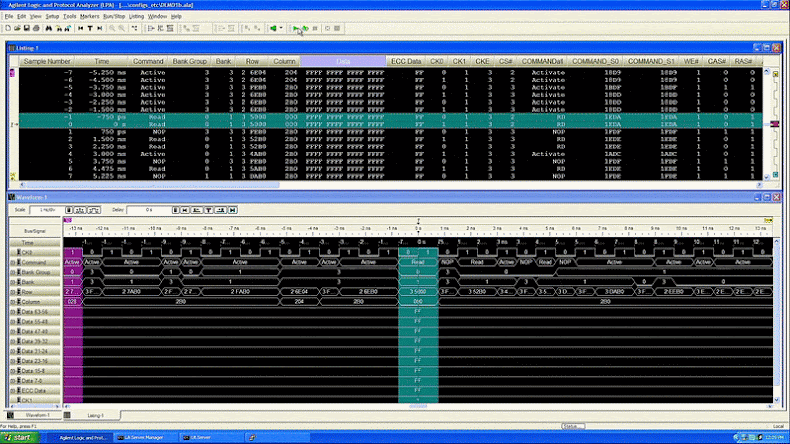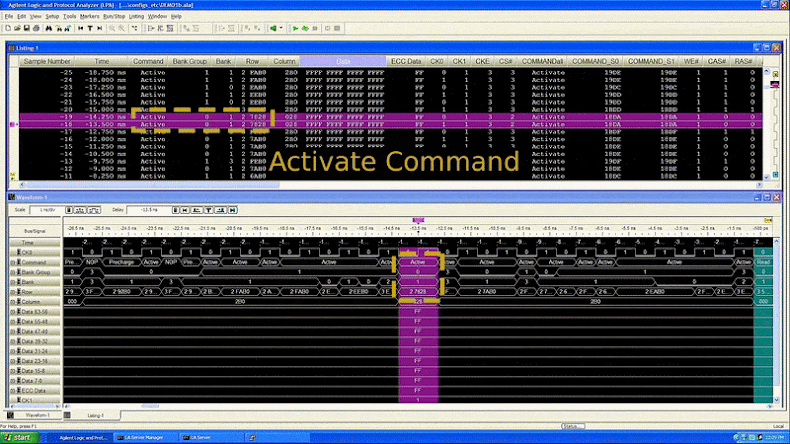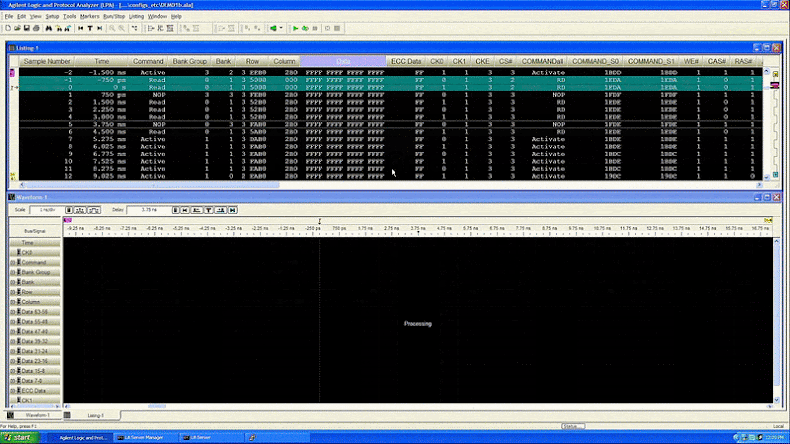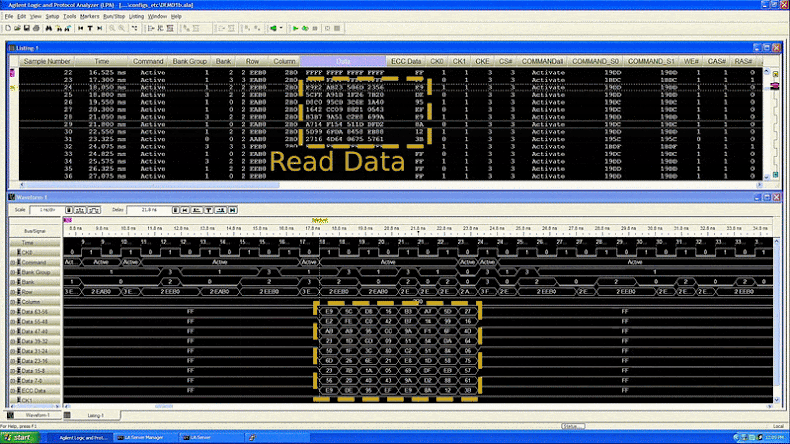
"We have successfully extracted attestation keys, which are the primary mechanism used to determine whether code is running under SGX," the researchers explained. "This allows any hacker to masquerade as genuine SGX hardware, while in fact running code in an exposed manner and peeking into your data."
The researchers added, "Like two sides of the same coin, WireTap and Battering RAM look at complementary properties of deterministic encryption. While WireTap focuses mainly on breaching confidentiality, BatteringRAM focuses mostly on integrity...both SGX and SEV are easy to break using memory interposition."
While Battering RAM can be executed with less than $50 of equipment, WireTap requires a logic analyzer, bringing the total cost to around $1,000.
The study highlights a potential attack scenario targeting SGX-backed blockchain deployments like Phala Network and Secret Network. WireTap could be used to compromise confidentiality and integrity, allowing attackers to expose confidential transactions or illegitimately gain rewards.
Intel's response? They consider this exploit outside their threat model, as it assumes an attacker with physical access to the hardware. They recommend running servers in secure physical environments or using cloud providers with strong physical security. They also stated they don't plan to issue a CVE (Common Vulnerabilities and Exposures) because the attack is outside the protection offered by the memory encryption.


