IoT Botnet Shuttered US and Dutch Authorities Take Down 7000 Device Proxy Network
Thousands of compromised Internet of Things gadgets and unsupported, end-of-life systems were silently fueling a criminal proxy network, until a joint U.S. and Dutch law enforcement operation shut it down. The botnet, composed of over 7,000 devices, masked the online activity of malicious actors, providing them with anonymity before authorities intervened.
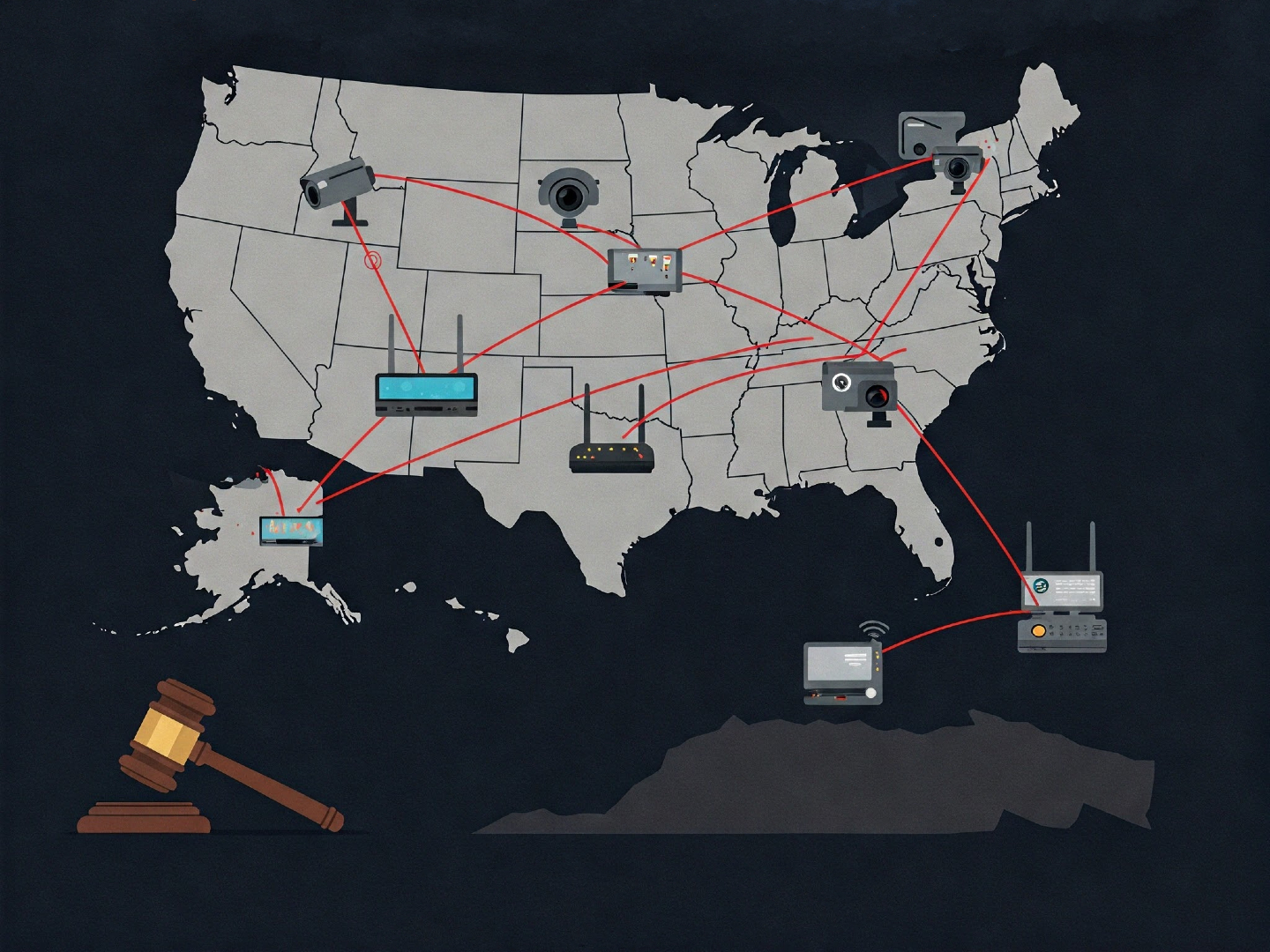
Authorities in the Netherlands and the U.S. have teamed up to take down a massive criminal proxy network. This network was powered by thousands of compromised Internet of Things (IoT) devices, including many that were already at their end-of-life (EoL). These devices were turned into a botnet, essentially a robot army, used to mask the identities of cybercriminals.
And that's not all – the U.S. Department of Justice (DoJ) has charged several individuals for allegedly running the proxy services. The accused are Russian nationals Alexey Viktorovich Chertkov, Kirill Vladimirovich Morozov, Aleksandr Aleksandrovich Shishkin, and Dmitriy Rubtsov, along with a Kazakhstani national. They're accused of operating, maintaining, and profiting from this illegal enterprise.
Here's the kicker: users paid a monthly fee, from $9.95 to a whopping $110, to access the infected routers. The DoJ estimates the threat actors raked in over $46 million by selling access to this botnet. This service is believed to have been running since 2004!
The FBI even discovered hacked routers in Oklahoma homes and businesses. Malware was secretly installed on these devices, without the owners even knowing.
Lumen Technologies' Black Lotus Labs tracked the botnet's activity. They found an average of 1,000 unique bots contacting the command-and-control (C2) infrastructure, which was located in Turkey. In a report shared with The Hacker News, they noted that over half of the victims were in the United States, followed by Canada and Ecuador.
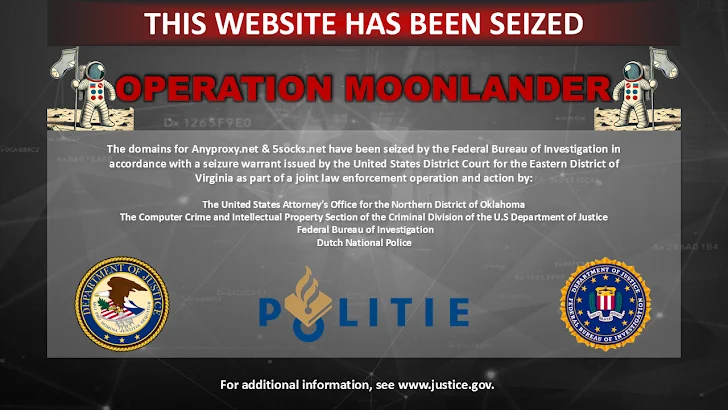
The services involved, anyproxy.net and 5socks.net, have been disrupted as part of "Operation Moonlander." According to Lumen, both platforms were essentially selling access to the same botnet, just under different names.
Internet Archive snapshots reveal that 5socks.net advertised "more than 7,000 online proxies daily" across various countries and U.S. states. This allowed cybercriminals to anonymously conduct all sorts of illegal activities in exchange for cryptocurrency.
So, how did they do it? Lumen says the compromised devices were infected with a malware strain called TheMoon. This malware has also been linked to another criminal proxy service called Faceless. Lumen has taken action by blocking traffic to and from the known control points of the botnet.
According to Lumen, the two services (Anyproxy and 5socks) shared the same pool of proxies and command-and-control servers. They exploited vulnerabilities common in end-of-life devices. However, Lumen clarifies that these proxy services are separate from Faceless.
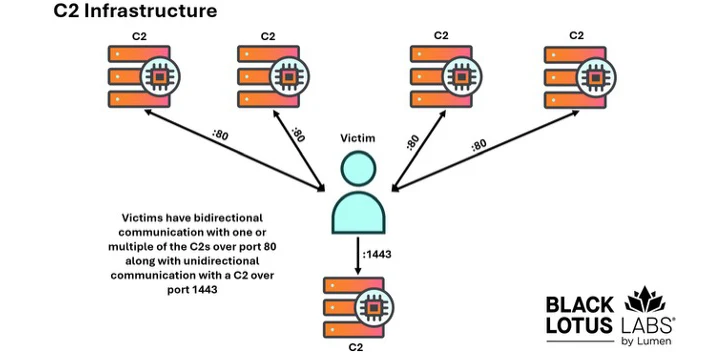
The suspicion is that the botnet operators used known exploits to infiltrate these older devices and add them to their proxy network. New bots were found to connect to a C2 infrastructure in Turkey, consisting of five servers. Four of these servers communicated with the infected devices on port 80.
One of these five servers used UDP on port 1443 to receive traffic from the victims, but didn't send anything back. The cybersecurity company believes this server was used to store information gathered from the infected devices.
The FBI issued an advisory, stating that the botnet operators exploited known security flaws in internet-exposed routers to install malware, giving them persistent remote access.
The FBI also highlighted that end-of-life routers were compromised with a variant of TheMoon malware. This allowed the criminals to install proxy software and conduct cybercrimes anonymously. The SANS Technology Institute first documented TheMoon back in 2014, when it was targeting Linksys routers.
The FBI explained that TheMoon doesn't need a password to infect routers. It scans for open ports and sends a command to a vulnerable script. The malware then contacts the C2 server, which responds with instructions. These instructions might include telling the infected machine to scan for other vulnerable routers, spreading the infection and expanding the network.
When someone buys a proxy, they get an IP and port combination to connect. Similar to the NSOCKS botnet, this service lacked any extra security measures after activation, making it vulnerable to abuse. It turns out, 5socks.net was used for ad fraud, DDoS attacks, brute-force attempts, and data theft.
So, what can you do? To protect yourself from these kinds of botnets, regularly reboot your router, install security updates, change the default password, and upgrade to a newer model when your current one reaches its end-of-life.
Lumen warns that "proxy services have and will continue to present a direct threat to internet security as they allow malicious actors to hide behind unsuspecting residential IPs, complicating detection by network monitoring tools."
And with so many outdated devices still in use, and the growing number of IoT devices, there will continue to be a huge number of potential targets for cybercriminals.