Qilin Ransomware Dominates April Data Leak Landscape
The Qilin ransomware group surged to the top spot in April, responsible for a staggering 45 publicly disclosed data leaks. Security researchers have also uncovered details of a recent Qilin campaign, dating back to November 2024, that utilized the SmokeLoader malware alongside a newly identified .NET loader dubbed NETXLOADER.
The cybercrime world never sleeps, and the folks behind the Qilin ransomware are proving it. Security researchers have spotted them using a new piece of malware called NETXLOADER in their attacks, alongside the well-known SmokeLoader.
According to a report from Trend Micro, this NETXLOADER is a sneaky .NET-based tool that plays a "critical role" in these cyberattacks. In fact, Jacob Santos, Raymart Yambot, John Rainier Navato, Sarah Pearl Camiling, and Neljorn Nathaniel Aguas, the Trend Micro researchers who discovered the malware, said NETXLOADER hides in the shadows, secretly dropping nasty payloads like the Agenda ransomware and SmokeLoader.
What makes NETXLOADER particularly nasty? It's protected by .NET Reactor 6, making it a real headache to analyze.
Qilin's Rise to the Top
Qilin, which is also known as Agenda, has been causing trouble since July 2022. You might remember hearing about Qilin.B, an upgraded version discovered last year by Halcyon. This ransomware family has been steadily evolving and becoming a bigger threat.
And it seems they're doing a good job. Group-IB recently reported that the number of victims posted on Qilin's data leak site has more than doubled since February 2025. This surge has propelled Qilin to the top spot among ransomware groups in April, surpassing the likes of Akira, Play, and Lynx.
"Between July 2024 and January 2025, Qilin's crew was leaking data from no more than 23 companies each month," Group-IB explained. "But since February 2025, that number has jumped dramatically, with 48 in February, 44 in March, and 45 in just the first few weeks of April."
Some believe Qilin has also benefited from the recent shutdown of RansomHub, which was the second-most active ransomware group in 2024, according to Flashpoint. RansomHub reportedly claimed 38 victims in the financial sector alone between April 2024 and April 2025. When one door closes...
Who's Getting Hit?
Trend Micro's data shows that Agenda ransomware is primarily targeting healthcare, technology, financial services, and telecommunications sectors in the U.S., the Netherlands, Brazil, India, and the Philippines.
How NETXLOADER Works
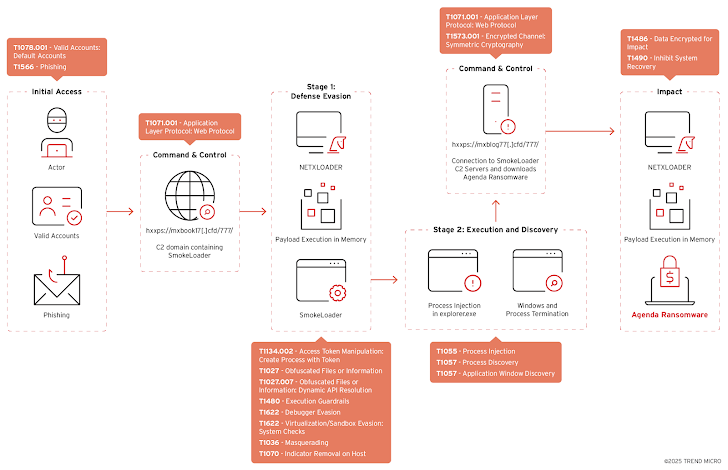
So, what's the deal with NETXLOADER? Trend Micro explains that it's a heavily disguised loader designed to grab further malicious software from external servers (like "bloglake7[.]cfd"). These downloaded tools are then used to deploy SmokeLoader and the dreaded Agenda ransomware.
To avoid detection and make analysis difficult, NETXLOADER uses a bunch of tricks: .NET Reactor version 6 protection, just-in-time (JIT) hooking techniques, nonsensical method names, and control flow obfuscation.
"The operators' use of NETXLOADER is a major leap forward in how malware is delivered," Trend Micro warns. "It uses a heavily obfuscated loader that hides the actual payload, meaning you can't know what it truly is without executing the code and analyzing it in memory. Even string-based analysis won't help because the obfuscation scrambles the clues that would normally reveal the payload's identity."
The Attack Chain
Here's how a typical attack unfolds: The attackers use stolen credentials or phishing emails to deliver NETXLOADER. This loader then drops SmokeLoader onto the victim's machine. SmokeLoader then tries to detect virtual machines and sandboxes, and also terminates a list of running processes. Finally, SmokeLoader connects to a command-and-control (C2) server to download NETXLOADER, which ultimately launches the Agenda ransomware using a technique called reflective DLL loading.
"The Agenda ransomware group is continually evolving by adding new features designed to cause disruption," the researchers concluded. "Its diverse targets include domain networks, mounted devices, storage systems, and VCenter ESXi."




