React and Next.js Patches Needed to Fix Remote Code Execution Risk
Developers using React Server Components in React and Next.js should update their applications immediately. A newly discovered, critical vulnerability could allow attackers to execute arbitrary code on affected servers without needing to authenticate, potentially leading to full system compromise.

A serious security vulnerability has been discovered in React Server Components (RSC). If exploited, it could allow attackers to remotely run code on your server.
This flaw, tracked as CVE-2025-55182, has been given the highest severity score possible – a whopping 10.0. Some are calling it React2shell.
According to the React Team, the vulnerability allows for "unauthenticated remote code execution" because of a weakness in how React decodes data sent to React Server Function endpoints. Check out their official alert for more details.
Here's the kicker: even if you aren't actively using React Server Function endpoints, you might still be vulnerable if your application supports React Server Components.
Wiz, a cloud security firm, explains that the issue boils down to unsafe deserialization. In other words, React isn't properly sanitizing the data it receives, allowing attackers to inject malicious code via specially crafted HTTP requests to Server Function endpoints. When React processes this tainted data, it inadvertently executes the attacker's code on the server.
Aikido, a software supply chain security company, puts it this way: "The issue stems from unsafe handling of serialized payloads in the React Flight protocol. Malformed or adversarial payloads can influence server-side execution in unintended ways." Thankfully, patched versions of React include stricter validation and improved deserialization techniques.
Which Versions Are Affected?
This vulnerability impacts these versions of the following npm packages:
- react-server-dom-webpack (versions 19.0, 19.1.0, 19.1.1, and 19.2.0)
- react-server-dom-parcel (versions 19.0, 19.1.0, 19.1.1, and 19.2.0)
- react-server-dom-turbopack (versions 19.0, 19.1.0, 19.1.1, and 19.2.0)
The good news is that fixes are available in versions 19.0.1, 19.1.2, and 19.2.1.
Kudos to Lachlan Davidson, a security researcher from New Zealand, for discovering and reporting the flaw to Meta. Meta, the original creator of React, handed over control to the React Foundation recently.
Notably, this vulnerability also affects Next.js when using the App Router. While initially assigned CVE-2025-66478, it was later rejected as a duplicate. It impacts versions >=14.3.0-canary.77, >=15, and >=16. Patched versions are 16.0.7, 15.5.7, 15.4.8, 15.3.6, 15.2.6, 15.1.9, and 15.0.5.
Keep in mind that any library bundling RSC is likely to be affected, including Vite RSC plugin, Parcel RSC plugin, React Router RSC preview, RedwoodJS, and Waku.
Security firms like Endor Labs, Miggo Security, and VulnCheck emphasize that this flaw is easily exploitable, even without requiring a login or using HTTPS.
As Endor Labs points out, "An attacker needs only network access to send a crafted HTTP request to any Server Function endpoint. The vulnerability affects default framework configurations, meaning standard deployments are immediately exploitable without special conditions."
What Can You Do?
Until you can apply the patches, here are some recommendations:
- Deploy Web Application Firewall (WAF) rules (if available).
- Monitor HTTP traffic to Server Function endpoints for suspicious requests.
- Consider temporarily restricting network access to affected applications.
Cloudflare has already deployed a WAF rule to protect its customers. Similarly, Akamai, AWS, Fastly, and Google Cloud have implemented similar safeguards.
Wiz reports that a significant percentage (39%) of cloud environments contain instances vulnerable to this issue. Don't wait – apply those patches ASAP!
Justin Moore from Palo Alto Networks Unit 42 warns that there are over 968,000 servers running React and Next.js, making this a prime target for attackers.
Moore highlights the insidious nature of this vulnerability: "This newly discovered flaw is a critical threat because it is a master key exploit, succeeding not by crashing the system, but by abusing its trust in incoming data structures. The system executes the malicious payload with the same reliability as legitimate code because it operates exactly as intended, but on malicious input."
Digging Deeper into CVE-2025-55182
OX Security explains that the root cause is the unsafe deserialization of React Flight reply payloads, leading to unauthenticated remote code execution. Searchlight Cyber has even created an HTTP request you can use to test if your system is vulnerable.
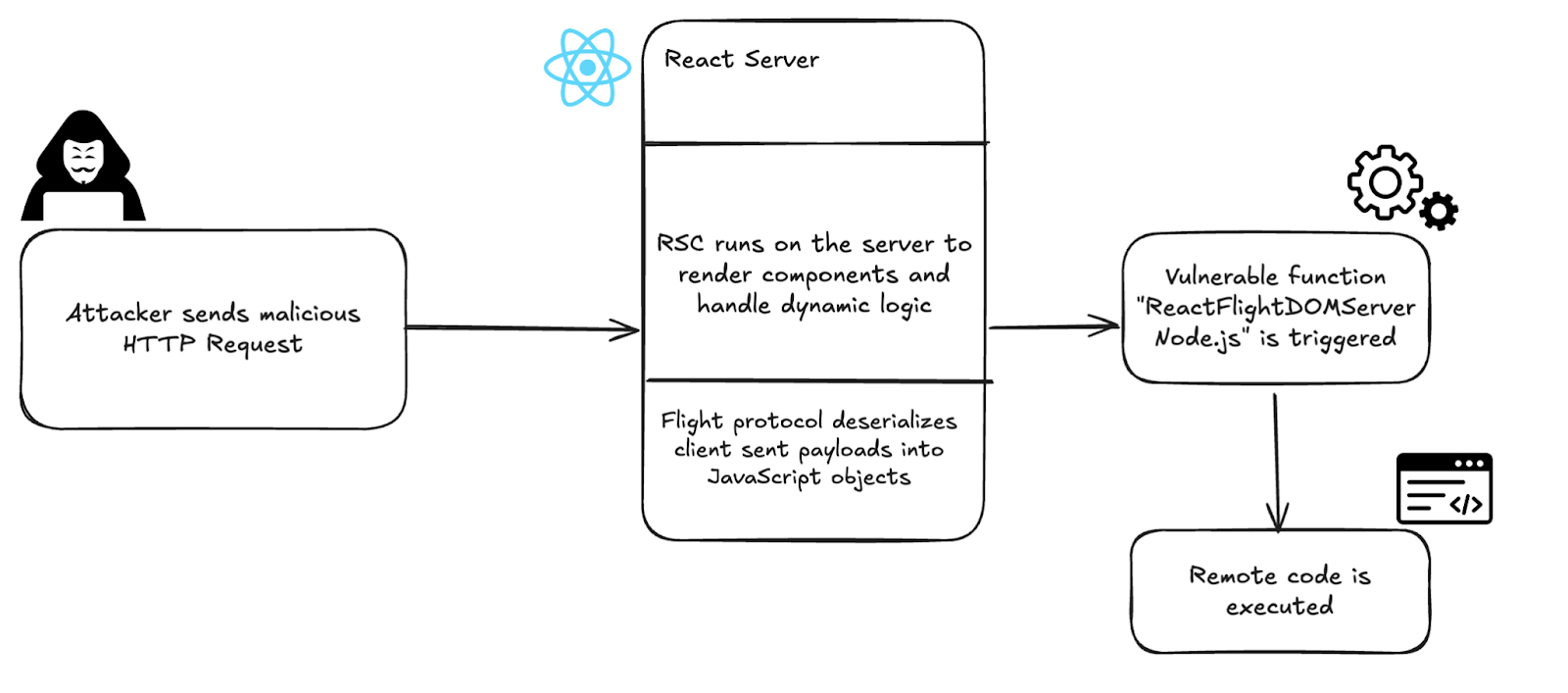
Avital Harel and Guy Gilad from Upwind point to the requireModule function within the react-server-dom-webpack package as the culprit. This function is responsible for loading functions that a client wants to call on the server.
An attacker can send a specially crafted HTTP POST request to trigger a "Server Action" using "vm.runInThisContext," tricking React into executing their malicious code. This results in code execution on the server with the same permissions as the Node.js process.
Upwind also notes that while React doesn't directly expose the vulnerable React Flight reply server endpoint, Next.js *does*, transforming a theoretical vulnerability into a "real, remotely reachable attack surface."
"These endpoints accept structured Flight payloads directly from the browser," they add. "That means anyone on the internet can send a request, attach their own Flight stream, and rely on Next.js to forward it into React's deserializer. Once that happens, the vulnerable code path handles the payload exactly as if it came from a trusted client."
(This story was updated after initial publication with additional details.)