React2Shell Vulnerability Exploited In the Wild Prompts CISA Warning
A critical security vulnerability dubbed React2Shell, affecting React Server Components, is now under active attack, prompting the U.S. Cybersecurity and Infrastructure Security Agency (CISA) to add it to its list of Known Exploited Vulnerabilities. Organizations are urged to patch immediately.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has just added a serious security vulnerability affecting React Server Components (RSC) to its list of Known Exploited Vulnerabilities (KEV). This move comes after reports surfaced of the flaw being actively exploited in the wild. You can check out the official CISA alert here and the KEV catalog here.
What's the Big Deal?
This vulnerability, dubbed CVE-2025-55182 (and also known as React2Shell), is a big one, scoring a perfect 10.0 on the CVSS scale. What does that mean? It's a remote code execution (RCE) flaw, meaning an attacker could potentially run malicious code on your server without needing any credentials or special setup.
CISA's advisory spells it out: "Meta React Server Components contains a remote code execution vulnerability that could allow unauthenticated remote code execution by exploiting a flaw in how React decodes payloads sent to React Server Function endpoints."
The Root Cause: Insecure Deserialization
The problem lies in the insecure way React's Flight protocol handles deserialization – basically, turning data back into usable objects. This protocol is how React communicates between the server and the client. A Rapid7 blog post explains it well.
As Martin Zugec from Bitdefender put it, "The process of converting text into objects is widely considered one of the most dangerous classes of software vulnerabilities... The React2Shell vulnerability resides in the react-server package, specifically in how it parses object references during deserialization."
Affected Libraries and Frameworks
The vulnerability has been patched in these versions:
- react-server-dom-webpack (19.0.1+)
- react-server-dom-parcel (19.1.2+)
- react-server-dom-turbopack (19.2.1+)
But it's not just React directly. Several popular frameworks that rely on React are also affected, including Next.js, React Router, Waku, Parcel, Vite, and RedwoodSDK.
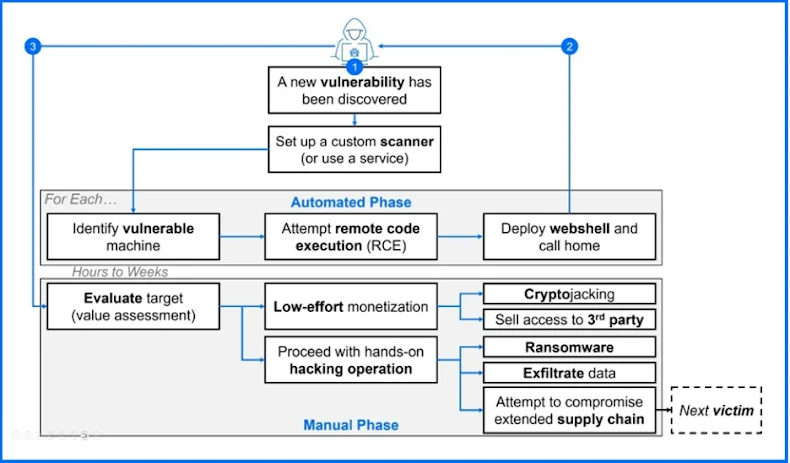
Exploitation in the Wild
Amazon reported seeing attack attempts from groups linked to Chinese hackers almost immediately after the vulnerability was disclosed. Other security firms like Coalition, Fastly, GreyNoise, VulnCheck, and Wiz have also confirmed active exploitation.
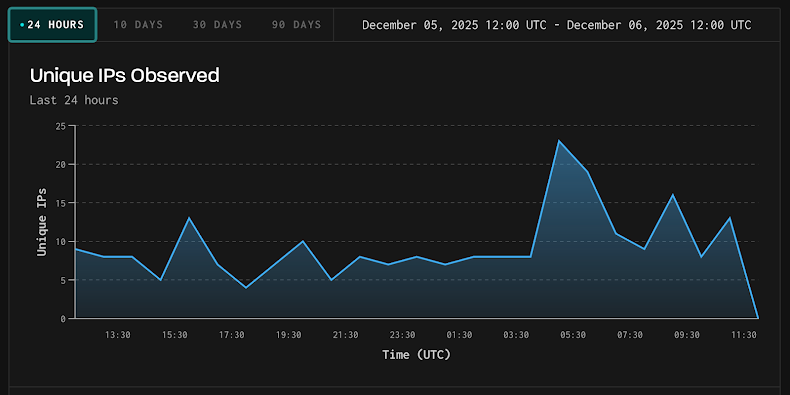
Image Source: GreyNoise
Some attackers are reportedly installing cryptocurrency miners. Others are using PowerShell commands to test for successful exploitation, followed by downloading additional malicious payloads.
How Widespread is the Risk?
According to Censys, around 2.15 million internet-facing services could be vulnerable. That's a lot of exposed React Server Components and related frameworks like Next.js, Waku, React Router, and RedwoodSDK.
Who's Behind the Attacks?
Palo Alto Networks Unit 42 says they've seen over 30 affected organizations, with some activity linked to a Chinese hacking group called UNC5174 (aka CL-STA-1015). They're using tools like SNOWLIGHT and VShell.
"We have observed scanning for vulnerable RCE, reconnaissance activity, attempted theft of AWS configuration and credential files, as well as installation of downloaders to retrieve payloads from attacker command and control infrastructure," said Justin Moore from Palo Alto Networks Unit 42.
Proof-of-Concept Exploits Available
Security researcher Lachlan Davidson, who discovered the vulnerability, has released proof-of-concept (PoC) exploits. Another working PoC is available here, published by a researcher on GitHub.
What You Need to Do
The bottom line? Update your React and related framework versions immediately. If you're a Federal Civilian Executive Branch (FCEB) agency, you have until December 26, 2025, to comply with Binding Operational Directive (BOD) 22-01.