Russia and Ukraine Under Siege by Stealthy DarkWatchman Malware
A sophisticated phishing operation is targeting Russian organizations, deploying the DarkWatchman malware with tactics resembling those of nation-state actors. The campaign highlights the ongoing cyber threat landscape facing the region.

Russian companies are in the crosshairs of a large-scale phishing operation spreading a nasty piece of malware called DarkWatchman. Think of it as a digital burglar, sneaking into systems to steal information.
According to Russian cybersecurity firm F6, the targets are spread across various sectors, including media, tourism, finance, manufacturing, retail, energy, and even biotech. Read their report here.
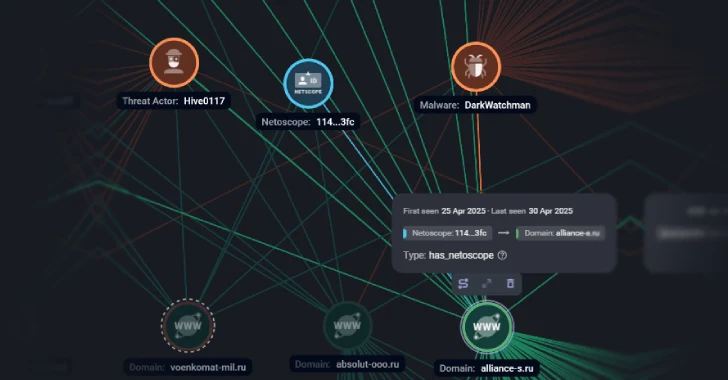
Experts believe the culprit is a financially motivated group known as Hive0117. IBM X-Force has linked this group to previous attacks targeting users in Lithuania, Estonia, and Russia.
This isn't the first time DarkWatchman has surfaced. Back in September 2023, it was used in another phishing campaign targeting energy, finance, and transport industries across Russia, Kazakhstan, Latvia, and Estonia.
Then, in November 2023, Russian banks, retailers, telecom operators, and energy companies were targeted again, this time with phishing lures disguised as courier delivery notifications.
So, what does DarkWatchman do? It's a JavaScript-based remote access trojan (RAT) that can log your keystrokes, steal system information, and even deploy other malicious software. It was first spotted in December 2021.
IBM described DarkWatchman as "somewhat sophisticated," noting its "fileless nature" and ability to cover its tracks.
The latest attacks involve phishing emails with password-protected archives. Once opened, these archives unleash an updated version of DarkWatchman, designed to be even harder to detect.
Ukraine Targeted by New Sheriff Backdoor
In other news, IBM X-Force revealed that an organization within Ukraine's defense sector was targeted in early 2024 with a brand-new Windows backdoor called Sheriff.
"The attackers used a popular Ukrainian news portal, ukr.net, to host the Sheriff backdoor," said security researcher Golo Mühr in a report. "This backdoor allows attackers to execute commands, grab screenshots, and steal data using Dropbox."
Essentially, Sheriff is designed to steal data and take screenshots while staying under the radar for as long as possible.
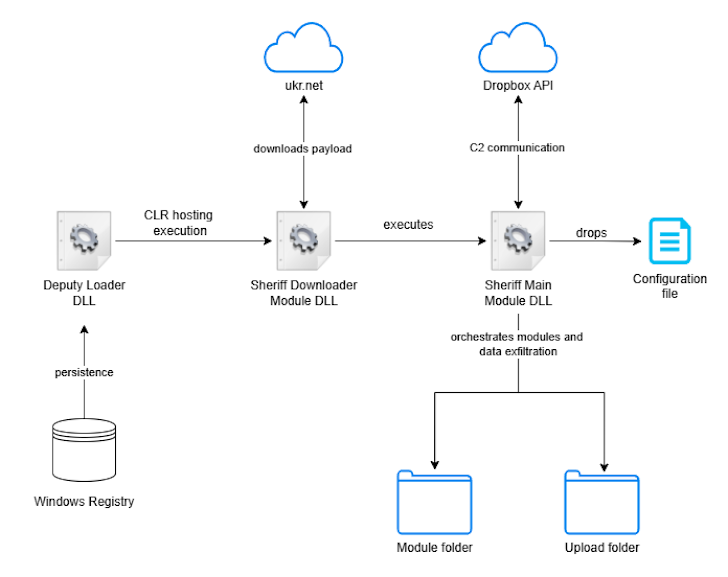
It's suspected that the attackers may have hacked ukr.net in early March 2024 to host the malware. Sheriff is modular, meaning it can download and manage different components, including a screenshot tool. It receives instructions and configuration data as ZIP file comments.
Mühr explained, "Access to Ukraine's largest news portal would allow attackers to launch a variety of attacks and operate with better camouflage. In this case, they may have used the trusted domain to host malware without raising suspicion."
Sheriff also has a "suicide" function that allows the attackers to remotely wipe the malware and its command-and-control infrastructure, making it even harder to trace.
Interestingly, IBM noted similarities between Sheriff and other malware families linked to the Turla group, such as Kazuar and Crutch, as well as Operation Groundbait's Prikormka and Bad Magic's CloudWizard.
According to IBM, "CloudWizard and Sheriff share a 'GetSettings' function, and CloudWizard, Prikormka, and Sheriff all take screenshots every 15 minutes. CloudWizard and Prikormka also have file listing modules called 'tree,' which is the same name Sheriff uses."
The discovery of Sheriff comes after Ukraine's State Service for Special Communications and Information Protection (SSSCIP) reported a 48% increase in cyber incidents in the second half of 2024.
SSSCIP stated that "Russian hackers are actively using automation, supply chain attacks, and combining espionage and sabotage. Their main goal is to gather intelligence that could impact the situation on the front lines, particularly targeting situational awareness systems and defense companies."