ToyMaker Broker Peddles Network Access to CACTUS Ransomware Group
A cybercrime middleman known as ToyMaker is selling access to compromised networks, reportedly funneling victims directly into the clutches of the CACTUS ransomware gang. Security experts are warning that this initial access broker (IAB) is facilitating double extortion attacks, where sensitive data is stolen before systems are encrypted, amplifying the pressure on victims to pay up.
Cybersecurity researchers have uncovered a new player in the ransomware game: an initial access broker (IAB) going by the name of ToyMaker. This actor has been spotted handing over access to notorious double extortion ransomware groups, including CACTUS.
So, what's ToyMaker all about? Experts believe, with medium confidence, that they're financially driven, constantly scanning the web for vulnerable systems. Their weapon of choice? A custom malware called LAGTOY, also known as HOLERUN.
"LAGTOY is pretty nasty," says Cisco Talos researchers Joey Chen, Asheer Malhotra, Ashley Shen, Vitor Ventura, and Brandon White. They explain that it "can be used to create reverse shells and execute commands on infected endpoints."
This malware first surfaced back in March 2023, thanks to Google's Mandiant, who attributed it to a group they track as UNC961. You might also know this group as Gold Melody or Prophet Spider – they have a few aliases.
Here's the playbook: ToyMaker exploits known security weaknesses in internet-facing applications to gain that initial foothold. Then, within a week, they're conducting reconnaissance, stealing credentials, and deploying LAGTOY.
But it doesn't stop there. The attackers also establish SSH connections to a remote host, downloading a forensics tool called Magnet RAM Capture. The goal? To grab a memory dump of the compromised machine, likely to scoop up even more victim credentials.
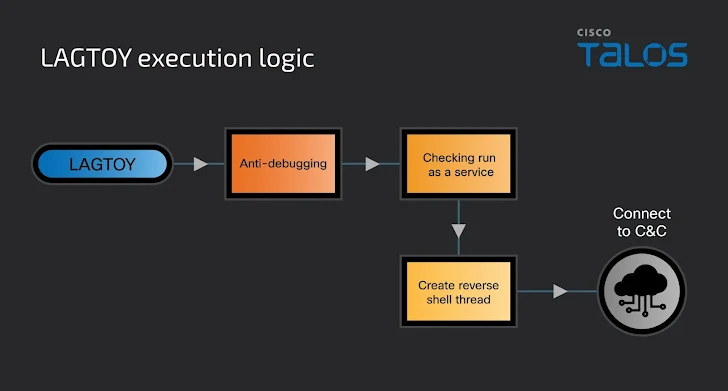
So, what does LAGTOY do? According to experts, it's designed to connect to a pre-programmed command-and-control (C2) server, waiting for instructions to execute on the compromised system. Mandiant notes that it can create processes and run commands under specific users, inheriting their privileges.
The malware can handle three commands from the C2 server, pausing for 11 seconds between each one.
"After a lull in activity of about three weeks, we saw the CACTUS ransomware gang enter the victim's network using credentials stolen by ToyMaker," Talos researchers said.
The good news? "Based on the quick turnaround, the lack of data theft (initially), and the subsequent handover to CACTUS, it seems unlikely that ToyMaker is interested in espionage."
In the specific case Talos investigated, the CACTUS affiliates did their own reconnaissance and established persistence before exfiltrating data and encrypting systems. They also used multiple methods to maintain long-term access, including OpenSSH, AnyDesk, and eHorus Agent.
The bottom line? "ToyMaker is a financially motivated IAB. They break into high-value organizations and then sell that access to other threat actors, who typically monetize it through double extortion and ransomware deployments," the company concludes.