Ukraine and Vietnam Under Fire From SVG-Based Phishing Delivering PureRAT
A sophisticated phishing campaign is targeting Ukraine and Vietnam, leveraging malicious SVG files and the PureRAT remote access trojan. Attackers are masquerading as Ukrainian government entities to trick victims into downloading CountLoader, a malware loader that subsequently deploys the Amatera Stealer and PureMiner cryptominer.

A new wave of phishing attacks is impersonating Ukrainian government agencies to sneak in CountLoader malware. Once that's in, it drops even more nasty stuff – Amatera Stealer and PureMiner.
According to Yurren Wan, a researcher at Fortinet FortiGuard Labs, "The phishing emails use tricky Scalable Vector Graphics (SVG) files. These are designed to fool people into opening what looks like harmless attachments, but they're anything but." Wan shared this info in a report with The Hacker News.
So, how does this attack unfold? The booby-trapped SVG files kick off a download of a ZIP archive, which is even password-protected! Inside? A Compiled HTML Help (CHM) file. Opening that CHM file sets off a chain reaction that ultimately installs CountLoader. The emails themselves? They try to look like official notices from the National Police of Ukraine.
CountLoader, which has been analyzed recently by Silent Push, is known for dropping payloads like Cobalt Strike and PureHVNC RAT. But in this case, it's being used to spread Amatera Stealer (a variant of ACRStealer) and PureMiner, which is a sneaky cryptocurrency miner written in .NET.
Here's something interesting: PureHVNC RAT and PureMiner are part of a bigger malware family from a threat actor called PureCoder. They've got other tools in their arsenal, including:
- PureCrypter: Used to hide Native and .NET malware
- PureRAT (aka ResolverRAT): The next-gen version of PureHVNC RAT
- PureLogs: Steals information and logs keystrokes
- BlueLoader: Acts like a botnet, downloading and running payloads from afar
- PureClipper: Swaps cryptocurrency addresses in your clipboard with the attacker's, stealing your funds.
Fortinet says that Amatera Stealer and PureMiner are deployed as fileless threats. This means the malware is "executed via .NET Ahead-of-Time (AOT) compilation with process hollowing or loaded directly into memory using PythonMemoryModule."
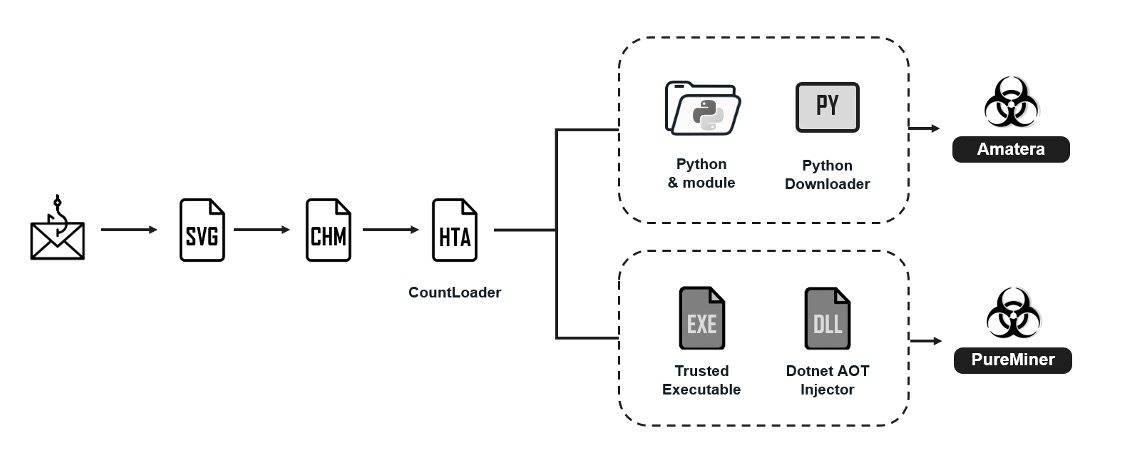
Once Amatera Stealer is running, it grabs system info, snatches files with specific extensions, and steals data from browsers (Chrome, Firefox, etc.) and apps like Steam, Telegram, FileZilla, and crypto wallets.
Fortinet warns, "This phishing campaign shows how a malicious SVG file can be used to start an infection chain. Attackers targeted Ukrainian government entities with emails containing SVG attachments. The HTML code embedded in the SVG redirects victims to a download site."
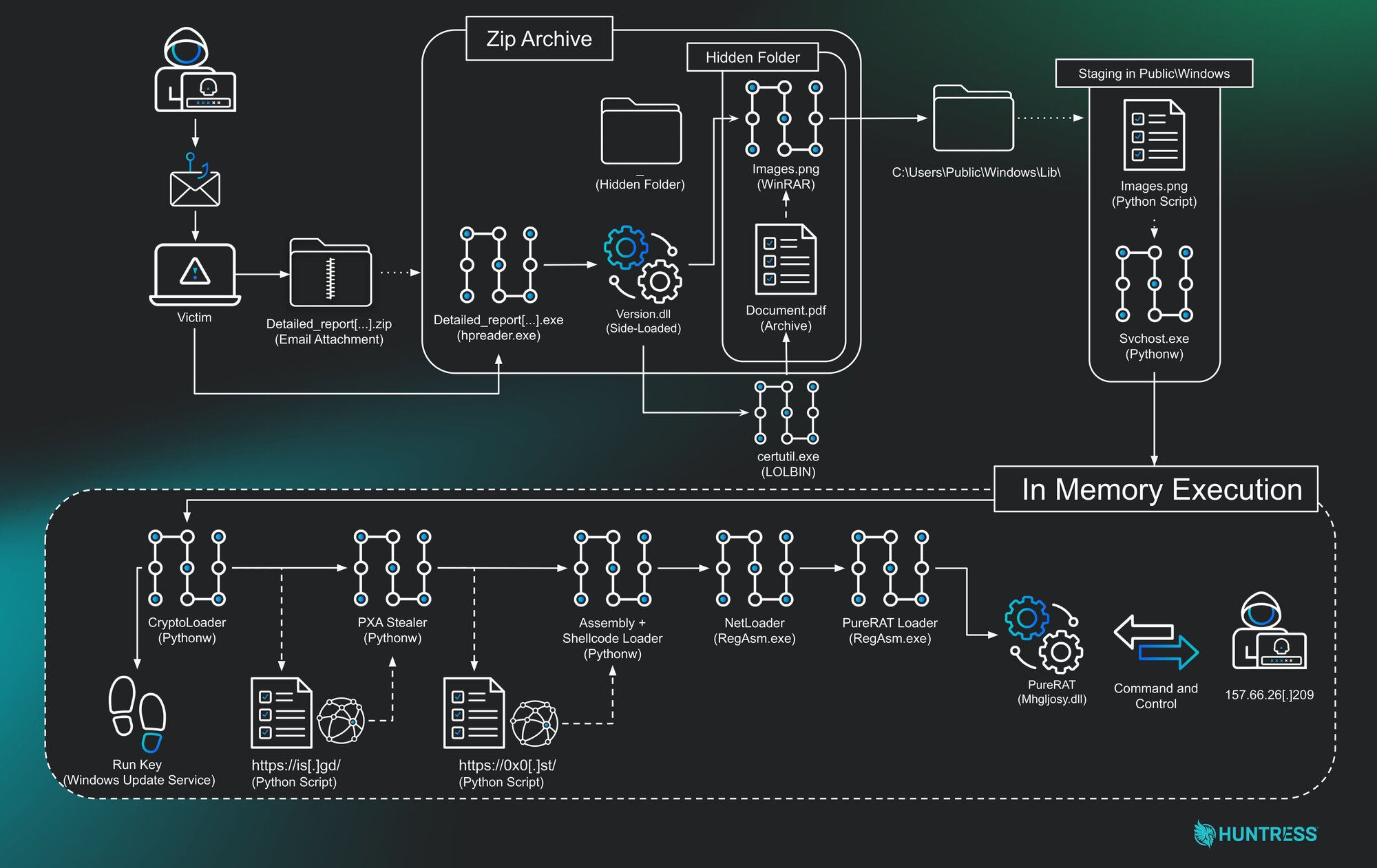
And there's more! Huntress discovered a group, likely Vietnamese-speaking, using phishing emails disguised as copyright infringement notices. These emails trick people into opening ZIP archives that lead to PXA Stealer, which then morphs into a multi-layered infection that also drops PureRAT.
Security researcher James Northey from Huntress explains, "This campaign shows a clear progression, starting with a simple phishing email and escalating through layers of loaders, evasion techniques, and credential theft. The final payload, PureRAT, gives the attacker complete control over the compromised computer."
He adds, "Their move from amateurish Python code to using commodity malware like PureRAT demonstrates not just persistence, but also a serious and maturing threat actor."