Yemeni Hacker Indicted for Black Kingdom Ransomware Attacks
A Yemeni national is facing U.S. federal charges for allegedly unleashing the Black Kingdom ransomware, impacting an estimated 1,500 systems worldwide. The Department of Justice announced the indictment, alleging the 36-year-old targeted a diverse range of victims, including American businesses, educational institutions, and even hospitals.

The U.S. Department of Justice (DoJ) has just announced charges against a 36-year-old Yemeni man. Rami Khaled Ahmed is accused of unleashing the Black Kingdom ransomware on targets worldwide, including businesses, schools, and even hospitals right here in the U.S.
Ahmed, who reportedly lives in Sana'a, Yemen, is facing serious charges: conspiracy, intentionally damaging protected computers, and threatening to damage them.
The DoJ alleges that "From March 2021 to June 2023, Ahmed and others infected computer networks of several U.S.-based victims, including a medical billing services company in Encino, a ski resort in Oregon, a school district in Pennsylvania, and a health clinic in Wisconsin," according to a statement.
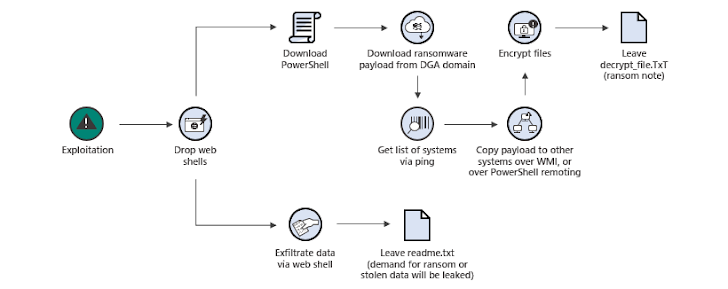
So, how did he allegedly do it? Authorities say Ahmed exploited a vulnerability called ProxyLogon in Microsoft Exchange Server to develop and spread the ransomware.
The Black Kingdom ransomware would either encrypt a victim's data or claim to have stolen it. After encryption, a ransom note would appear, demanding $10,000 in Bitcoin to be sent to a specific cryptocurrency address controlled by an accomplice.
Victims were also reportedly instructed to send proof of payment to a Black Kingdom email address. It's estimated that this ransomware hit around 1,500 computer systems in the U.S. and globally.
This particular ransomware family, also known as Pydomer, has been linked to earlier attacks that took advantage of vulnerabilities in Pulse Secure VPN (CVE-2019-11510). Microsoft revealed that it was the first known ransomware to exploit the ProxyLogon flaws back in March 2021.
Cybersecurity firm Sophos described Black Kingdom as "somewhat rudimentary and amateurish," suggesting the attackers were essentially using the ProxyLogon vulnerability to install web shells. These shells then allowed them to run PowerShell commands to download the ransomware.
Sophos even called the activity the work of a "motivated script-kiddie." Interestingly, in August 2021, there was an attempt to recruit insiders at companies, offering them $1 million in Bitcoin to deploy Black Kingdom ransomware as part of an insider threat scheme.
If convicted, Ahmed could face up to five years in federal prison for each charge. The FBI is investigating the case, with help from the New Zealand Police.
This announcement comes alongside a series of actions by U.S. authorities against various cybercriminal activities:
- The DoJ unsealed an indictment against Artem Stryzhak, a Ukrainian citizen, for using Nefilim ransomware. He's facing up to five years in prison.
- Tyler Robert Buchanan, a British national and suspected member of the Scattered Spider group, was extradited to the U.S. on wire fraud and identity theft charges. Other members were also charged.
- Leonidas Varagiannis and Prasan Nepal, leaders of a child extortion group, were arrested and charged with distributing child sexual abuse material.
- Richard Anthony Reyna Densmore, another member of the same group, was sentenced to 30 years for sexually exploiting a child. This group is linked to The Com, a collection of cybercrime groups.
- FinCEN designated Cambodia-based HuiOne Group as a "primary money laundering concern" for Southeast Asian cybercrime, facilitating romance scams and laundering money for North Korean cyber heists. Their banking license was revoked.
Ransomware Attacks: Still a Threat, But Payoffs Are Down
All this is happening as ransomware remains a significant problem. However, it's becoming more fragmented, and law enforcement actions are changing how these attacks are carried out. More and more attacks are happening without encryption, and cybercriminals are increasingly working alone rather than in large groups.
According to Halcyon, "Ransomware operations are becoming increasingly decentralized, with a growing number of former affiliates choosing to operate independently rather than remain tied to established groups."