CastleLoader Group Adds Python-Based RAT to Arsenal
The cybercriminals operating the CastleLoader malware-as-a-service platform have expanded their capabilities with a new remote access trojan (RAT) dubbed CastleRAT. This addition, written in Python and C, provides another weapon for threat actors leveraging the CastleLoader framework.

The people behind CastleLoader, a malware-as-a-service (MaaS) framework, have apparently been busy. They've now unleashed a remote access trojan (RAT) called CastleRAT.
Recorded Future Insikt Group dropped the news, saying, "CastleRAT comes in both Python and C flavors. Its main job is to grab system info, download and run more malicious stuff, and execute commands via CMD and PowerShell." You can read their full report here.
This threat actor, tracked as TAG-150, has been on the radar since at least March 2025. CastleLoader and its buddies are often the initial point of entry for all sorts of nasty things, including RATs, info stealers, and even other loaders.
Remember CastleLoader? It was first spotted back in July 2025 by PRODAFT. It was spreading around DeerStealer, RedLine, and a bunch of other malicious tools.
IBM X-Force chimed in last month, finding that CastleLoader was also pushing MonsterV2 and WARMCOOKIE through SEO poisoning and fake GitHub repositories.
"How do they get in?" you ask? "Usually through Cloudflare-themed 'ClickFix' phishing scams or bogus GitHub repos that look like real software," says Recorded Future.
They're using domains that mimic software development libraries, online meeting platforms, browser updates, and even document verification systems to trick people.
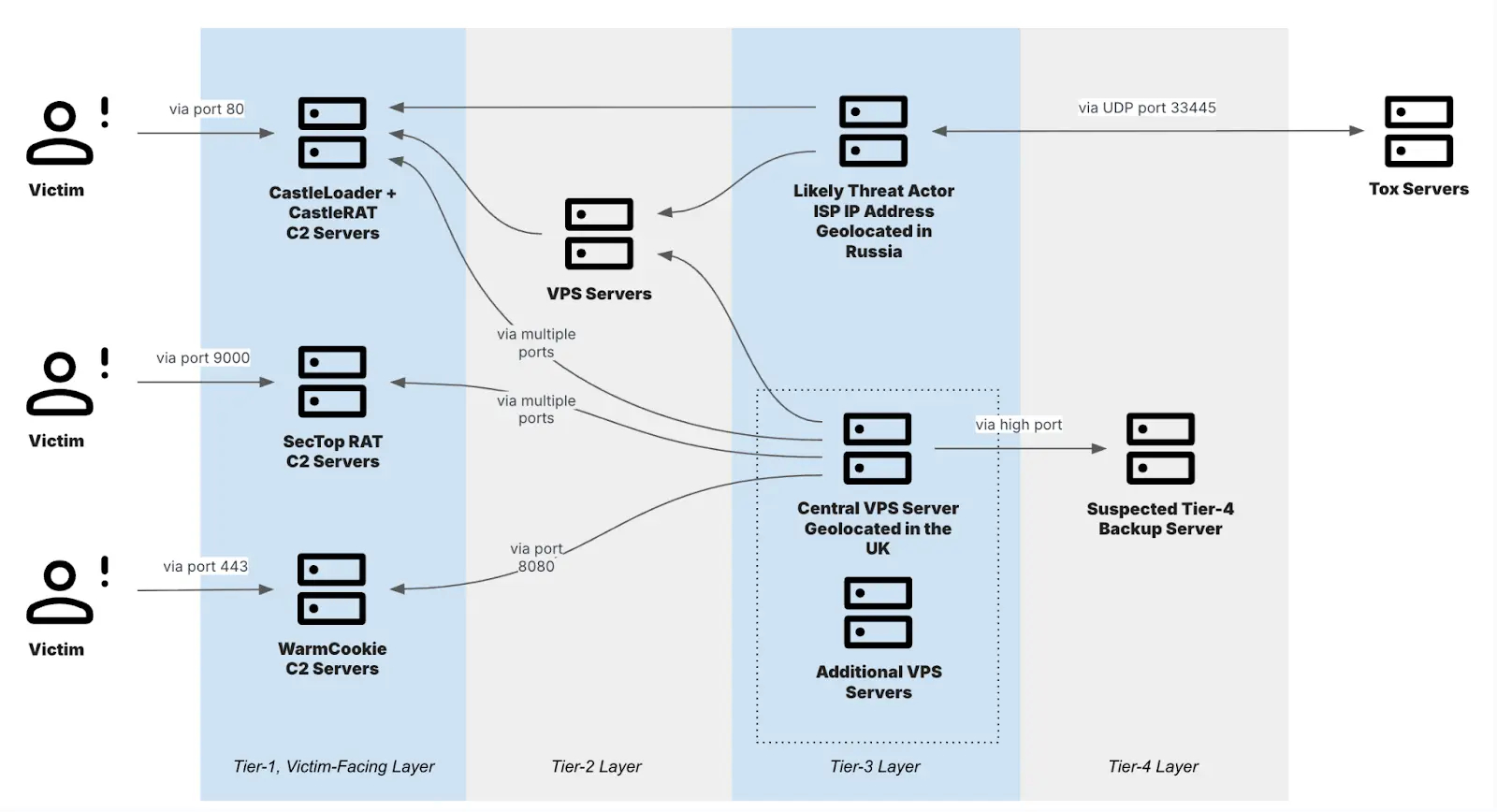
Apparently, TAG-150 has been tinkering with CastleRAT since March 2025. They're using a multi-layered setup with different tiers of servers for command and control (C2), including virtual private servers (VPSes) and backup servers.
So, what can CastleRAT do? It can download more malware, enable remote control, and even wipe itself clean. It also uses Steam Community profiles to hide its C2 servers ("programsbookss[.]com").
Here's the interesting part: there are two versions of CastleRAT. One's written in C, and the other's in Python (also known as PyNightshade). eSentire is tracking the same Python malware as NightshadeC2.
The C version of CastleRAT is the beefier one. It can log keystrokes, take screenshots, upload/download files, and even swap out cryptocurrency wallet addresses in your clipboard to steal your coins.
"Like the Python version, the C version uses the ip-api[.]com service to grab info based on your public IP address," Recorded Future notes. "But it now also includes your city, ZIP code, and whether you're using a VPN, proxy, or TOR."
However, the latest versions of the C variant have stopped grabbing city and ZIP code info, which suggests they're actively developing it. We'll have to wait and see if the Python version catches up.
eSentire's analysis of NightshadeC2 describes it as a botnet that uses a .NET loader. This loader uses tricks like UAC Prompt Bombing to get past security measures. They also found versions that can steal passwords and cookies from Chrome and Firefox-based browsers.
Basically, it runs a PowerShell command repeatedly to add an exclusion in Windows Defender for the final malware. If it works (exit code 0), it delivers the payload. If it fails, it keeps prompting you to approve the User Account Control (UAC) prompt until you give in.
"If Windows Defender is disabled, it gets stuck in a loop, which bypasses many sandbox solutions," eSentire explains.
And there's more! Hunt.io recently uncovered another malware loader called TinyLoader, which is spreading Redline Stealer and DCRat.
Besides sticking around by changing Windows Registry settings, TinyLoader watches your clipboard and swaps out crypto wallet addresses. Its C2 panels are hosted in Latvia, the U.K., and the Netherlands.
"TinyLoader installs both Redline Stealer and cryptocurrency stealers to steal credentials and hijack transactions," Hunt.io says. "It spreads through USB drives, network shares, and fake shortcuts."
To top it off, two new malware families have surfaced: TinkyWinkey (a Windows keylogger) and Inf0s3c Stealer (a Python info stealer). They're designed to steal keyboard input and gather system information.
Inf0s3c Stealer shares similarities with Blank Grabber and Umbral-Stealer, suggesting the same author might be behind all three.
"TinkyWinkey is a stealthy and capable keylogger that uses persistent service execution, low-level keyboard hooks, and system profiling to steal your data," CYFIRMA warns.
Inf0s3c Stealer "collects system details, including host identifiers, CPU information, and network configuration, and captures screenshots. It also lists running processes and user directories."