ClickFix Malware Bypasses CAPTCHAs for Widespread Attacks
A clever social engineering scheme called ClickFix has been spreading rapidly for the past year, thanks to its ability to trick users and evade detection. Research from Guardio Labs reveals how ClickFix leverages sophisticated tactics, including bypassing CAPTCHAs, to infect a wide range of platforms.
A new social engineering tactic called ClickFix has exploded onto the scene over the last year, thanks to its clever methods of spreading, sophisticated narratives, and sneaky evasion techniques. That's according to recent research from Guardio Labs.
"This new 'ClickFix' strain is like a real-world virus that rapidly outpaced and wiped out the fake browser update scams we saw last year," explained security researcher Shaked Chen in a report.
What makes ClickFix so effective? Chen says it "removed the need for file downloads, used smarter social engineering tactics, and spread through trusted infrastructure. The result - a wave of infections ranging from mass drive-by attacks to hyper-targeted spear-phishing lures."
So, what exactly is ClickFix? It's a social engineering trick where users are tricked into infecting their own computers, often under the pretense of fixing a problem or completing a CAPTCHA. It first popped up in early 2024.
These attacks start with a variety of methods: phishing emails, drive-by downloads, malicious ads, and even search engine optimization (SEO) poisoning. They all lead users to fake pages displaying error messages.
The goal? To get you to follow a series of steps that secretly copies a malicious command to your clipboard. When you paste it into the Windows Run dialog box or the Terminal app (on Apple macOS), the trouble begins.
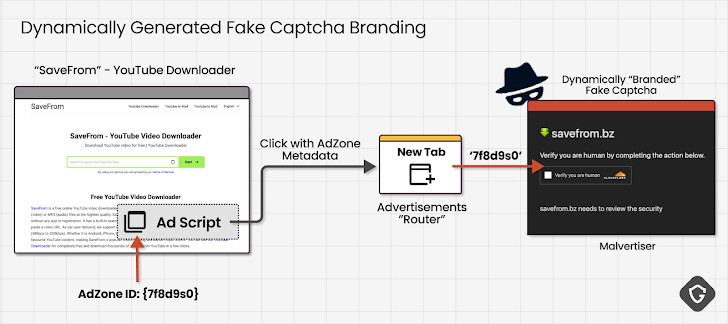
That seemingly innocent command kicks off a chain reaction, deploying various types of malware: stealers, remote access trojans, and loaders. It's a versatile and dangerous threat.
This tactic has become so effective that Guardio calls it a "CAPTCHAgeddon." Both cybercriminals and even nation-state actors are using it in many campaigns.
ClickFix is basically a stealthier, more evolved version of ClearFake. ClearFake used compromised WordPress sites to show fake browser update pop-ups that delivered stealer malware. Later, ClearFake added tricks like EtherHiding to hide its payload using Binance's Smart Chain (BSC) contracts.
Guardio believes ClickFix's success comes from constant improvements in how it spreads, the variety of lures it uses, and its ability to avoid being detected. It's gotten so good that it's replaced ClearFake.
"Early prompts were pretty basic, but they quickly became more convincing, adding a sense of urgency or suspicion," Chen explained. "These small changes increased the chances of people falling for it by playing on basic psychological pressures."
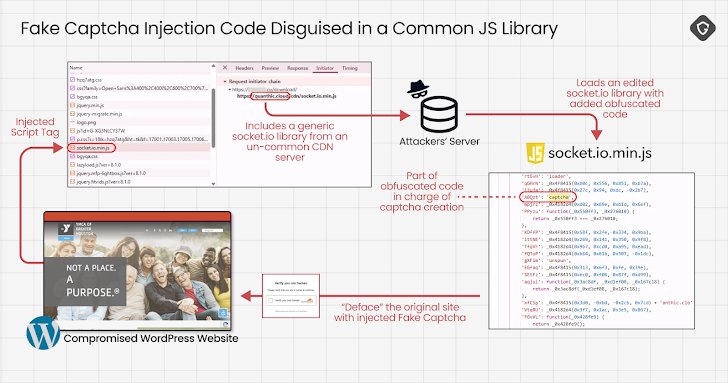
One key adaptation is the use of Google Scripts to host the fake CAPTCHA flows. This leverages the trust people have in Google's domain. They're also hiding the malicious code within legitimate-looking files like socket.io.min.js.
"This list of techniques – obfuscation, dynamic loading, legitimate-looking files, cross-platform handling, third-party payload delivery, and abuse of trusted hosts like Google – shows how attackers are constantly adapting to stay hidden," Chen warned.
The bottom line? "Attackers aren't just improving their phishing lures or social engineering skills. They're investing heavily in technical methods to make sure their attacks remain effective and difficult to stop."




