Hackers Use Raspberry Pi Over 4G to Target ATM Networks, Deploy Rootkit
A financially driven hacking group, tracked as UNC2891, is deploying a sophisticated attack on ATM networks, using a Raspberry Pi connected via 4G to compromise systems and potentially install the CAKETAP rootkit for fraudulent purposes.
A financially motivated hacking group, known as UNC2891, has been spotted targeting ATMs with a pretty clever trick: they're using a Raspberry Pi equipped with 4G to launch covert attacks. It's like something out of a heist movie!
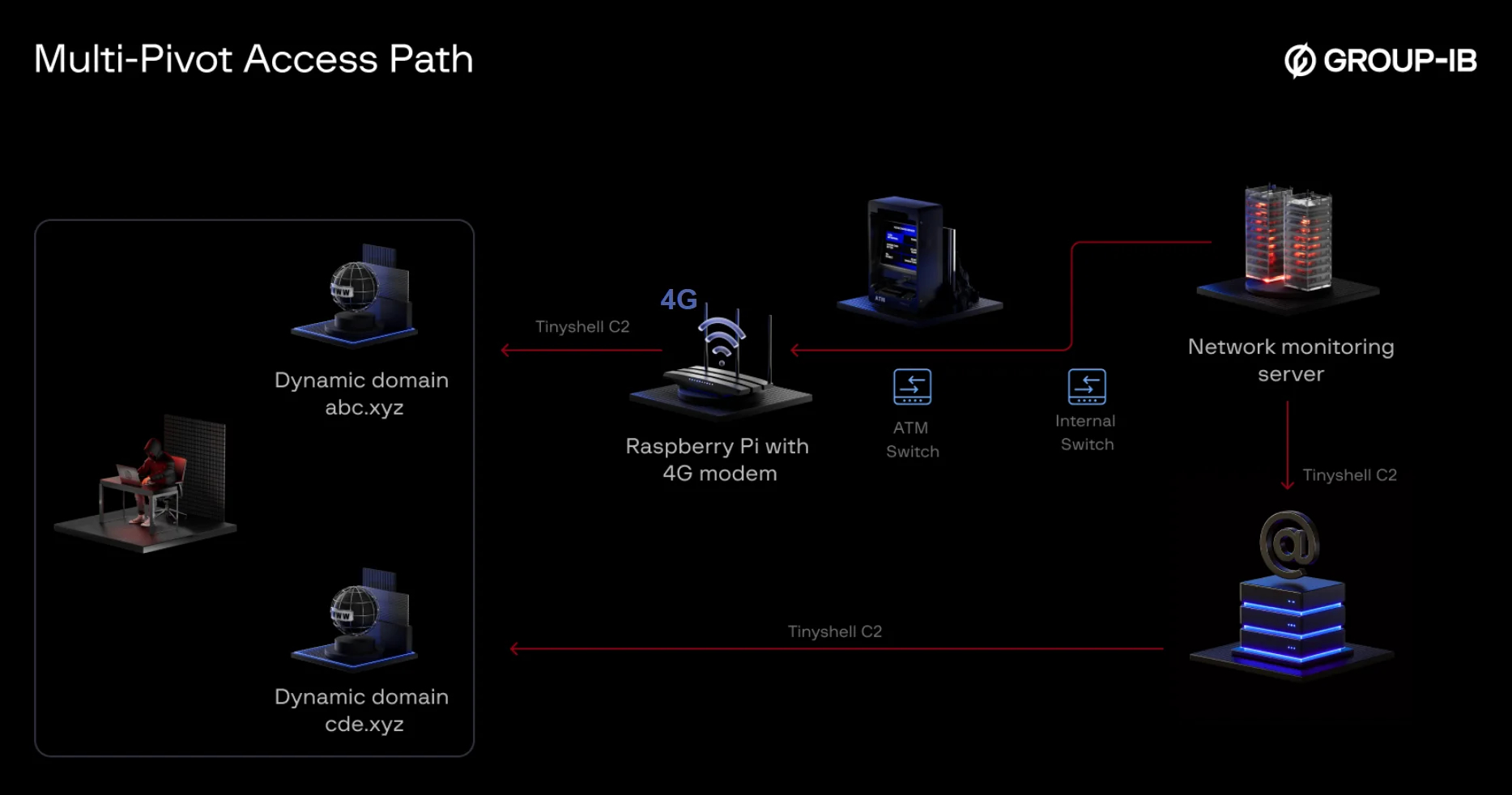
So, how did they pull it off? Apparently, the attackers gained physical access to the ATM's network switch (we don't know how yet, that's the mystery!). They then plugged in their Raspberry Pi, essentially giving themselves a backdoor into the bank's network, according to Group-IB.
"The Raspberry Pi was armed with a 4G modem, allowing them to remotely access the network using mobile data," said security researcher Nam Le Phuong in a recent report.
Think about it: "Using the TINYSHELL backdoor, the attacker set up a command-and-control (C2) channel through a Dynamic DNS domain. This let them get continuous external access to the ATM network, going right around firewalls and other security measures." Sneaky, right?
Remember UNC2891? They were first identified by Google's Mandiant back in March 2022. Turns out they've been hitting ATM switching networks to make illegal cash withdrawals with fake cards.
A key part of their operation involves a kernel module rootkit called CAKETAP. This rootkit is designed to hide network connections, processes, and files. It also intercepts and spoofs card and PIN verification messages from hardware security modules (HSMs) to enable the fraud. Pretty sophisticated stuff.
Interestingly, this hacking group seems to share some tactics with another group called UNC1945 (also known as LightBasin). LightBasin has previously targeted managed service providers and companies in the financial and consulting sectors.
Group-IB notes that the attackers have a deep understanding of Linux and Unix-based systems. Their analysis discovered backdoors named "lightdm" on the victim's network monitoring server. These backdoors were designed to connect to the Raspberry Pi and the internal Mail Server.
The attack also involved the sneaky use of bind mounts to hide the backdoor and avoid detection. Think of it as digital camouflage.
The ultimate goal, like in previous attacks, was to deploy the CAKETAP rootkit on the ATM switching server and steal cash. Luckily, Group-IB said they were able to disrupt the campaign before any major damage was done.
"Even after the Raspberry Pi was found and removed, the attacker kept access through a backdoor on the mail server," Group-IB explained. "They used a Dynamic DNS domain for their command-and-control."


