Iranian Hackers Target Diplomats Worldwide in Embassy Email Breach
A hacking group with suspected ties to Iran has launched a sophisticated spear-phishing attack, compromising email accounts at over a hundred embassies and consulates globally. The multi-stage campaign appears to be aimed at gathering sensitive information from diplomats stationed in Europe and other regions.

A hacking group with suspected ties to Iran is making headlines for a large-scale spear-phishing operation. They're targeting embassies and consulates across the globe in what appears to be a well-coordinated and persistent attack.
Israeli cybersecurity firm Dream has linked the activity to operators aligned with Iran, specifically pointing the finger at a group known as Homeland Justice. This group has a history of offensive cyber activities.
"These weren't your average spam emails," Dream explains. "They were carefully crafted to look like legitimate diplomatic communications, sent to government officials worldwide." The firm believes this is part of a broader espionage effort aimed at diplomatic and governmental entities, especially given the current tense geopolitical climate.
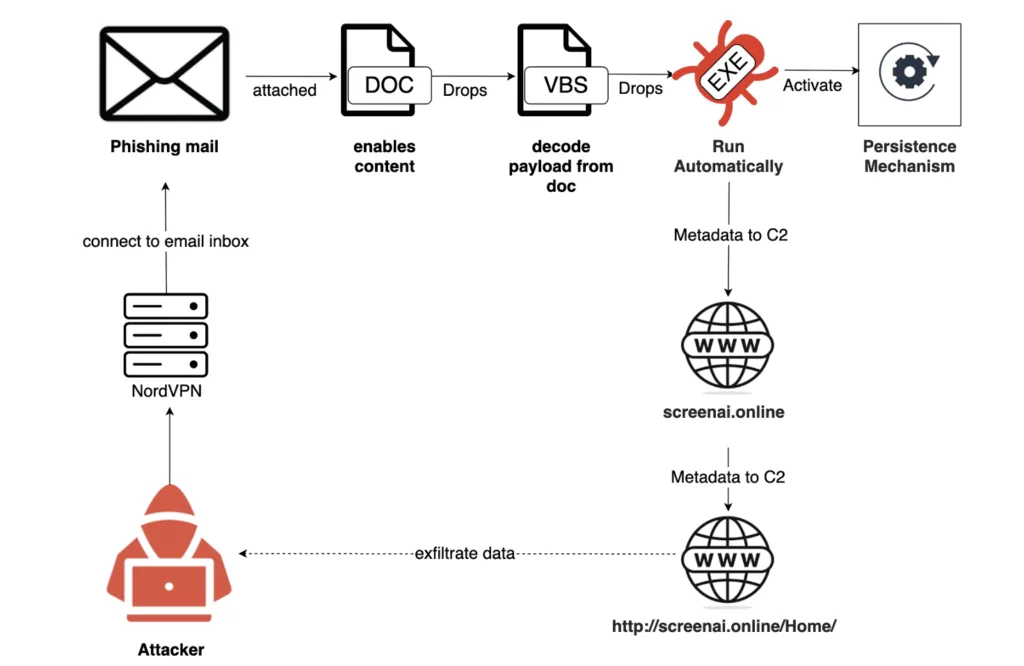
So, how did they pull it off? The attackers used spear-phishing emails, playing on the tensions between Iran and Israel. These emails contained malicious Microsoft Word documents. When opened, the documents urged recipients to "Enable Content." Doing so would execute a hidden Visual Basic for Applications (VBA) macro, which then deployed the malware.
Dream's investigation revealed that these emails were sent to embassies, consulates, and international organizations across a wide range of regions – the Middle East, Africa, Europe, Asia, and the Americas. It seems European embassies and African organizations were particularly hard hit.
To make the emails appear more authentic, the attackers used over 100 compromised email addresses belonging to real officials and pseudo-government entities. Shockingly, some emails even originated from a hacked mailbox belonging to the Oman Ministry of Foreign Affairs in Paris (*@fm.gov.om).
According to Dream, the emails consistently referenced urgent MFA communications, conveyed authority, and exploited the common practice of enabling macros. This points to a well-planned espionage operation designed to mask its origins.
Ultimately, the goal of these attacks was to use the VBA macro to install an executable file. This file would then establish persistence on the system, contact a command-and-control (C2) server, and begin harvesting sensitive system information.
Cybersecurity company ClearSky also investigated the campaign, noting that the phishing emails were sent to multiple ministries of foreign affairs.
"Similar tactics were used by Iranian threat actors in 2023 when they targeted Mojahedin-e-Khalq in Albania," ClearSky stated on X. They added that they have "moderate confidence" that this activity is linked to the same Iranian threat actors.