Iranian Hackers Target Telecoms with LinkedIn Job Scams and MINIBIKE Malware
A cyber espionage group with suspected ties to Iran, tracked as UNC1549, is running a sophisticated campaign against European telecommunications providers. The hackers are using fake job opportunities on LinkedIn to deliver the MINIBIKE malware, successfully compromising 34 devices at 11 different companies.
A cyber espionage group with ties to Iran, known as UNC1549, is making headlines for a new campaign. They're targeting European telecommunications companies, and they're using a clever trick: fake job opportunities on LinkedIn.
The hackers successfully infiltrated 34 devices across 11 organizations. The recruitment ruse seems to be working.
Swiss cybersecurity firm PRODAFT is calling this group Subtle Snail. They believe it's connected to Iran's Islamic Revolutionary Guard Corps (IRGC). The targeted companies are spread across Canada, France, the United Arab Emirates, the United Kingdom, and the United States.
"This group pretends to be HR representatives from legitimate companies," PRODAFT explained in a report. "They engage employees and then compromise their systems with a MINIBIKE backdoor. This backdoor uses Azure cloud services to hide its communications." Think of it as digital camouflage.
UNC1549 (also known as TA455) has been around since at least June 2022. It shares similarities with other Iranian hacking groups, like Smoke Sandstorm and Crimson Sandstorm. Google's Mandiant first documented the group in February 2024.
The use of job-related lures isn't new for UNC1549. ClearSky, an Israeli cybersecurity company, detailed how they targeted the aerospace industry as far back as September 2023, delivering malware like SnailResin and SlugResin.
PRODAFT notes that the group's main goal is to infiltrate telecom companies. But they're also interested in aerospace and defense, seeking long-term access to steal sensitive data for espionage.
Their attacks start with reconnaissance on LinkedIn. They identify key personnel—researchers, developers, IT admins—who have access to critical systems.
Next, they send spear-phishing emails to verify email addresses and gather more information before launching the fake recruitment drive.
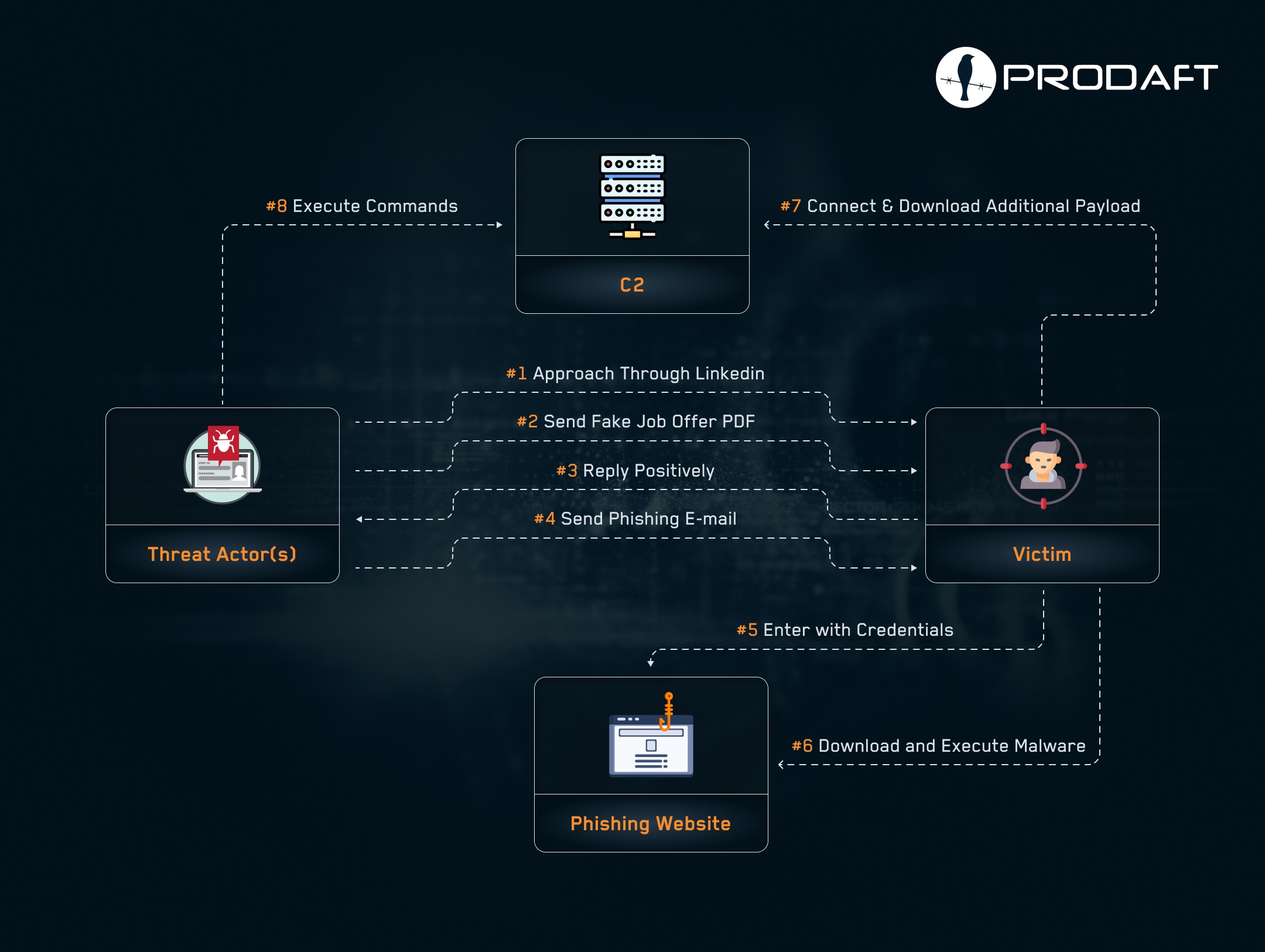
The attackers create convincing HR profiles on LinkedIn and reach out to potential targets with fake job openings. They build trust to increase the chances of success. It's all about looking legitimate.
If a victim shows interest, they're contacted via email to schedule an interview. Clicking a link to a fraudulent domain (mimicking companies like Telespazio or Safran Group) triggers a ZIP archive download.
Inside the ZIP file is an executable. Once launched, it uses DLL side-loading to deploy a malicious DLL called MINIBIKE. This backdoor gathers system information and waits for further instructions. It can then steal credentials, collect browser data, and take screenshots.
The browser stealer even uses a publicly available tool called Chrome-App-Bound-Encryption-Decryption to bypass app-bound encryption in Chrome, allowing them to decrypt and steal stored passwords.
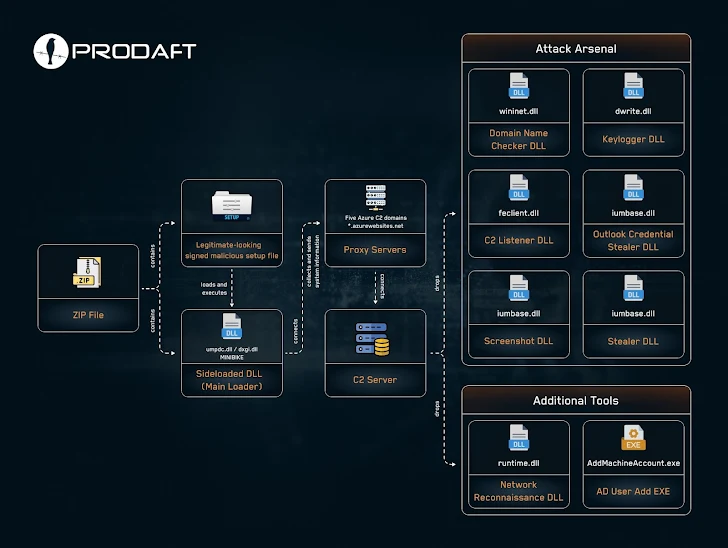
"The Subtle Snail team creates a unique DLL for each victim," PRODAFT said. "Even for something as simple as collecting network configuration information."
They modify legitimate DLL files to make the side-loading attack seamless. Function names are replaced with direct string variables, making it harder to detect.
MINIBIKE is a modular backdoor with 12 different commands. It can enumerate files, list processes, upload files, and run various payloads.
The malware also blends its traffic with legitimate cloud communications using Azure and VPSes. It modifies the Windows Registry to ensure it loads automatically on startup.
It uses anti-debugging and anti-sandbox techniques to avoid analysis. It also employs methods like Control Flow Flattening and custom hashing algorithms to make reverse engineering difficult.
"Subtle Snail's operations cause serious damage by combining intelligence gathering with long-term access to critical telecommunications networks," PRODAFT warns. "They don't just infect devices; they actively search for sensitive data and ways to maintain their access."
They target emails, VPN configurations, and other information that helps them stay in control. They also look for confidential files in shared folders, which can expose business secrets and personal data.
MuddyWater's Diversified Toolkit Exposed
Meanwhile, Group-IB revealed details about the infrastructure and malware used by another Iranian hacking group, MuddyWater. MuddyWater has "significantly" reduced its reliance on Remote Monitoring and Management (RMM) tools, opting for custom backdoors instead.




