Iranian State TV Disrupted with Anti-Government Protest Imagery
Viewers of Iranian state television were met with an unexpected interruption Wednesday night as hackers hijacked the broadcast to display videos urging citizens to protest against the Iranian government, sources report. The intrusion comes amid heightened geopolitical instability and follows reports of a separate $90 million cryptocurrency theft.

Iran's State TV Hacked Amid Escalating Cyber War with Israel
Talk about a bold move! Iran's state-owned TV broadcaster was hit by hackers Wednesday night, disrupting normal programming. The hackers reportedly aired videos calling for street protests against the government. It's a pretty direct message, wouldn't you say?
So, who's responsible? Right now, that's the million-dollar question. Iran, according to Iran International, is pointing fingers at Israel.
The broadcaster itself acknowledged the disruption, stating, "If you experience disruptions or irrelevant messages while watching various TV channels, it is due to enemy interference with satellite signals." Subtle, right?
This TV hack is just the latest in a series of cyber attacks inside Iran, many of which have been linked to actors connected to Israel. It also happened around the same time as attacks on Bank Sepah and Nobitex, which is Iran's biggest cryptocurrency exchange.
$90 Million Crypto Heist: A Major Escalation
The Nobitex breach is a big deal. We're talking about the theft of over $90 million! This is a serious escalation in the ongoing cyber conflict between Israel and Iran, a conflict that's been simmering for over a decade.
TRM Labs said that Iranian entities have been playing around with virtual assets, seeing them as both a way around financial restrictions and a strategic tool. According to TRM Labs, this could support their "broader geopolitical ambitions — including the proliferation of advanced weapons technology." The crypto space is increasingly becoming a target.
And there's more! Israeli officials recently revealed that Iran is apparently hijacking private security cameras inside Israel. The goal? Gather real-time intelligence. It's a tactic Russia used after invading Ukraine in 2022, so it's not exactly a new playbook.
Refael Franco, formerly with the Israel National Cyber Directorate, said, "We know that in the past two or three days, the Iranians have been trying to connect to cameras to understand what happened and where their missiles hit to improve their precision."
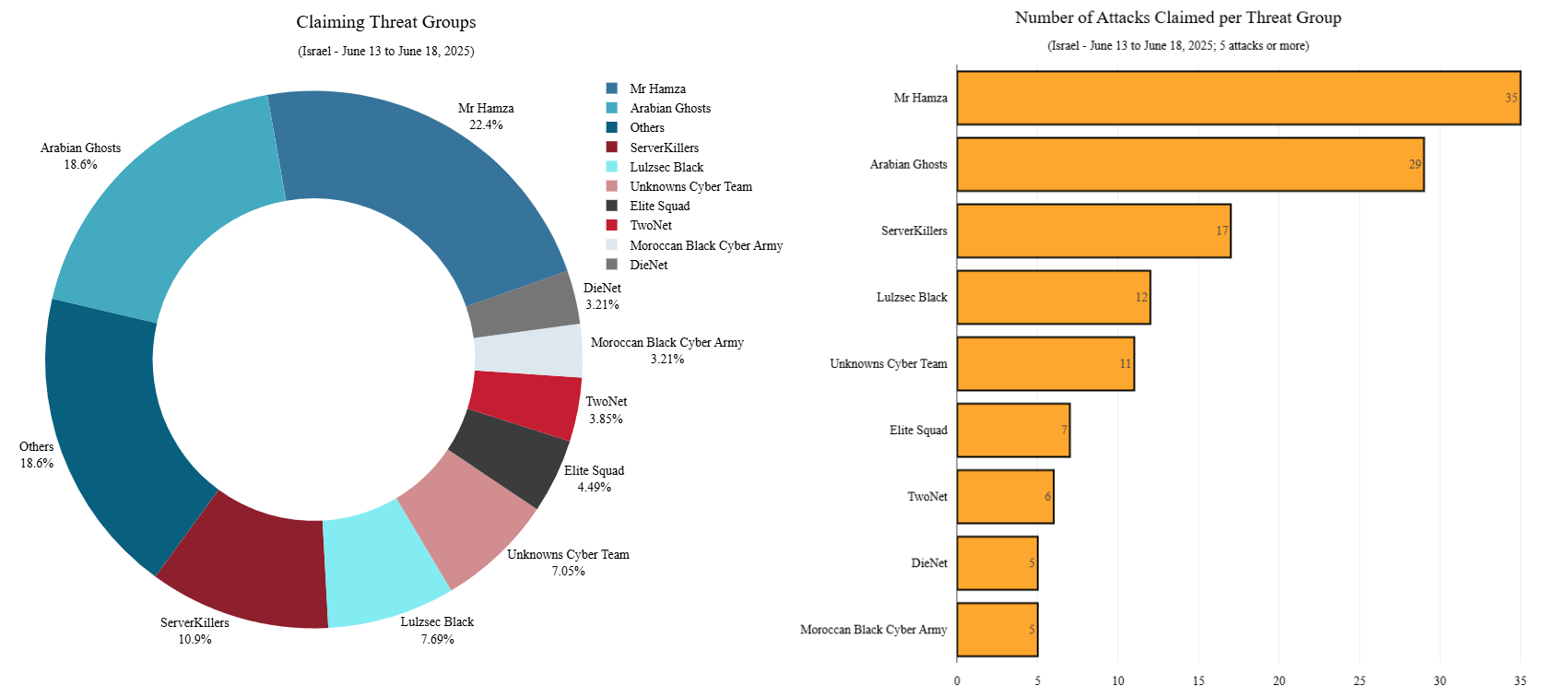
Groups claiming DDoS attacks targeting Israel between June 13 and June 18, 2025 | Source: Radware
Hacktivists Join the Fray
It's not just state actors involved. Cybersecurity firm Radware reports that almost 40% of all hacktivist DDoS attacks have been aimed at Israel since this latest conflict started heating up.
On June 17th, a hacktivist group called DieNet even warned they'd launch cyber-attacks against the United States if it jumped into the conflict on Israel's side.
Other groups, like Arabian Ghosts, Sylhet Gang, and Team Fearless, have echoed this message. Looks like we might be seeing some collaboration in the digital realm.
Pascal Geenens, director of threat intelligence at Radware, warns, "Companies are urged to take maximum vigilance. The warning signs are clear. Critical infrastructure, supply chains, and even global businesses could become collateral targets if the cyber crossfire intensifies."
He added, "The Israel-Iran conflict of 2025 is a stark illustration of modern hybrid warfare, where bytes and narratives are as much a part of the fight as bombs and missiles."
More Pro-Iranian Hacktivists?
A two-part analysis by CloudSEK suggests that there are more pro-Iranian groups launching cyberattacks against Israeli infrastructure than there are pro-Israeli groups doing the same. We're talking over 35 versus less than half a dozen.
According to security researcher Pagilla Manohar Reddy, "The attacks predominantly consisted of DDoS assaults, website defacements, and claimed data breaches targeting government sites, military systems, and critical infrastructure."
Reddy also notes that "Most significantly, these recent attacks maintain the same pattern of exaggeration and disinformation that has characterized the broader hacktivist ecosystem, with groups continuing to take credit for unrelated service outages, recycle old data leaks, and inflate damage claims for media attention rather than achieving substantial operational impact." So, take some of the claims with a grain of salt.
