Lazarus Group Unleashes Trio of New Malware Threats
A fresh social engineering campaign is spreading three previously unseen malware strains – dubbed PondRAT, ThemeForestRAT, and RemotePE – and cybersecurity experts are pointing the finger at the notorious North Korean hacking collective, Lazarus Group.

The notorious Lazarus Group, a threat actor linked to North Korea, is making headlines again. This time, they're being blamed for a social engineering campaign that's spreading three different types of malware across multiple platforms: PondRAT, ThemeForestRAT, and RemotePE.
According to researchers at NCC Group's Fox-IT, the attack was spotted in 2024 and zeroed in on an organization in the decentralized finance (DeFi) world. The bad guys managed to compromise an employee's computer, which, as you can imagine, opened up a whole can of worms.
Yun Zheng Hu and Mick Koomen from Fox-IT explained that the attackers used a combination of these RATs (Remote Access Trojans) and other tools to snoop around the network. They were hunting for credentials and setting up proxy connections. The researchers noted, "Afterwards, the actor moved to a stealthier RAT, likely signifying a next stage in the attack." It sounds like they were escalating their game.
How the Attack Unfolds
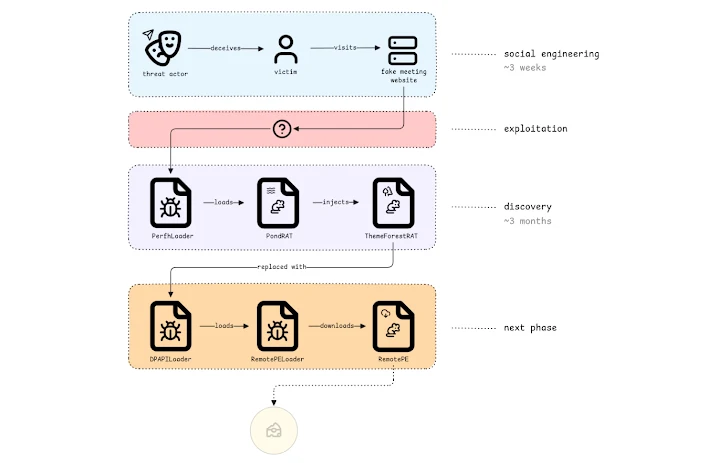
The attack kicks off with some classic social engineering. The Lazarus Group folks impersonated an existing employee of a trading company on Telegram. They then used fake websites that looked like Calendly and Picktime to trick the victim into scheduling a meeting.
While the initial point of entry isn't entirely clear, the attackers used it to deploy a loader called PerfhLoader. This loader then drops PondRAT, a malware variant related to POOLRAT (aka SIMPLESEA). There's even some evidence suggesting they might have used a then-zero-day exploit in the Chrome browser to get in.
But wait, there's more! Along with PondRAT, the attackers also delivered a bunch of other nasty tools, including a screenshot grabber, a keylogger, a Chrome credential and cookie stealer, Mimikatz, FRPC, and proxy programs like MidProxy and Proxy Mini.
According to Fox-IT, "PondRAT is a straightforward RAT that allows an operator to read and write files, start processes, and run shellcode." They also point out that it dates back to at least 2021. "The actor used PondRAT in combination with ThemeForestRAT for roughly three months, to afterwards clean up and install the more sophisticated RAT called RemotePE."
Diving Deeper into the Malware
PondRAT is designed to chat with a command-and-control (C2) server over HTTP(S) to get its marching orders. ThemeForestRAT, on the other hand, gets launched directly in memory, either by PondRAT or through a dedicated loader.
Like PondRAT, ThemeForestRAT keeps an eye out for new Remote Desktop (RDP) sessions and reaches out to a C2 server via HTTP(S). It can then receive up to twenty commands to do all sorts of things: list files and directories, mess with files, run commands, check TCP connections, change file timestamps, list processes, download files, inject shellcode, start new processes, and even hibernate for a while.
Interestingly, Fox-IT discovered that ThemeForestRAT has some things in common with a malware called RomeoGolf. This RomeoGolf was used by the Lazarus Group way back in November 2014 during the destructive wiper attack against Sony Pictures Entertainment (SPE). Novetta documented it as part of Operation Blockbuster.
RemotePE is the most advanced of the bunch. It's retrieved from a C2 server by RemotePELoader, which is itself loaded by DPAPILoader. Written in C++, RemotePE is likely reserved for those high-value targets.
So, what's the takeaway? "PondRAT is a primitive RAT that provides little flexibility, however, as an initial payload it achieves its purpose," Fox-IT explained. "For more complex tasks, the actor uses ThemeForestRAT, which has more functionality and stays under the radar as it is loaded into memory only."