MongoDB Flaw Exploited Globally Thousands of Databases at Risk
Cybersecurity researchers are sounding the alarm over a critical MongoDB vulnerability now being actively exploited. The flaw, tracked as CVE-2025-14847, puts tens of thousands of database instances worldwide at risk of compromise, with initial scans identifying over 87,000 potentially vulnerable systems.
A serious security flaw in MongoDB is being actively exploited, and it's a big deal. Security researchers have spotted attackers taking advantage of this vulnerability, with over 87,000 MongoDB instances potentially at risk worldwide.
What is MongoBleed?
The vulnerability, tracked as CVE-2025-14847, carries a CVSS score of 8.7, marking it as highly critical. It's been dubbed MongoBleed, and it allows attackers who haven't even authenticated to potentially steal sensitive data right from the MongoDB server's memory.
OX Security explains the problem: "A flaw in zlib compression allows attackers to trigger information leakage," they noted. "By sending malformed network packets, an attacker can extract fragments of private data."
How Does It Work?
The issue lies within MongoDB Server's zlib message decompression, specifically in "message_compressor_zlib.cpp". If you're using zlib compression (which is the default!), you're potentially vulnerable. Attackers could snag user info, passwords, API keys – the whole shebang.
OX Security warns that while grabbing the entire database might take time and some data might be garbled, "the more time an attacker has, the more information could be gathered."
Wiz, a cloud security firm, highlights that CVE-2025-14847 stems from a flaw in the zlib-based network message decompression. An attacker can essentially send corrupted, compressed packets to trigger the vulnerability and access uninitialized memory without needing any credentials.
Merav Bar and Amitai Cohen from Wiz explained that "the affected logic returned the allocated buffer size (output.length()) instead of the actual decompressed data length, allowing undersized or malformed payloads to expose adjacent heap memory." Since no authentication is needed, internet-exposed MongoDB servers are sitting ducks.
Who's Affected?
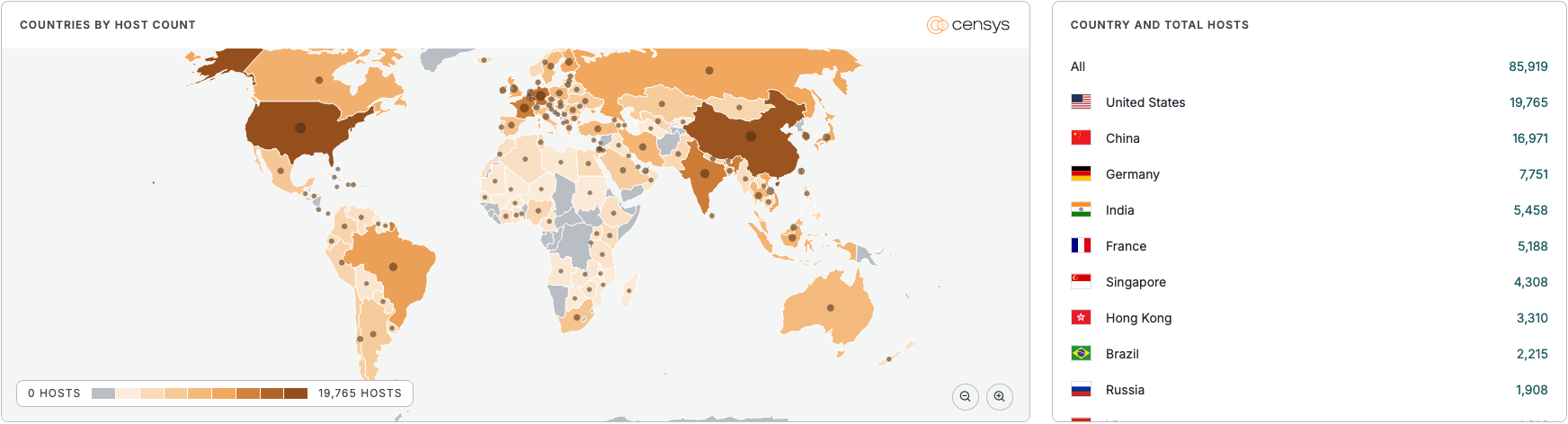
Censys, an attack surface management company, says over 87,000 instances are potentially vulnerable, mainly in the U.S., China, Germany, India, and France. Wiz adds that almost half of cloud environments have at least one vulnerable MongoDB instance, both internal and exposed to the internet.
What Can You Do?
The exact attack methods are still unclear, but here's what you should do immediately:
- Update! Upgrade to MongoDB versions 8.2.3, 8.0.17, 7.0.28, 6.0.27, 5.0.32, and 4.4.30 ASAP.
- MongoDB Atlas Users: Patches are already applied.
Even Ubuntu users should take note, as the Ubuntu rsync package, which also uses zlib, is affected.
Temporary Fixes:
Until you can update, consider these workarounds:
- Disable zlib compression: Start mongod or mongos without zlib.
- Restrict network access: Limit exposure of your MongoDB servers.
- Monitor logs: Watch for suspicious connections before authentication.
Stay safe out there!




