Moscow Embassies Targeted in Sophisticated ISP-Level Attack Linked to Secret Blizzard
A Russian hacking group, identified as Secret Blizzard, is suspected of launching a complex cyber espionage operation targeting foreign embassies in Moscow. The attack, conducted at the Internet Service Provider (ISP) level, allowed the hackers to intercept and manipulate network traffic in a man-in-the-middle style, ultimately deploying a custom malware strain called ApolloShadow.

a Russian hacking group called Secret Blizzard is running a cyber espionage campaign, and it's pretty sophisticated. They're using a man-in-the-middle (AitM) attack right at the Internet Service Provider (ISP) level. Think of it as intercepting your internet traffic before it even reaches you.
And the payload? A nasty piece of custom malware called ApolloShadow. According to Microsoft Threat Intelligence, "ApolloShadow can install a trusted root certificate, which tricks your devices into trusting malicious sites controlled by the hackers. This lets Secret Blizzard stick around on diplomatic devices, probably to gather intel." You can read their full report here.
This campaign has been going on since at least 2024, putting diplomatic staff who rely on local Russian ISPs at risk.
Who is Secret Blizzard?
Secret Blizzard (also known as Krypton, Blue Python, and about a dozen other names) is linked to the Russian Federal Security Service. So, yeah, they're serious.
Back in December 2024, Microsoft and Lumen Technologies Black Lotus Labs revealed that the group was hijacking command-and-control infrastructure from a Pakistani hacking group to hide their tracks. Clever, but not clever enough.
They've also been caught using malware from *other* hackers to deliver their own Kazuar backdoor onto devices in Ukraine. Basically, they're not afraid to get their hands dirty.
Microsoft says the AitM attack likely involves lawful intercepts and installing root certificates disguised as Kaspersky antivirus. This gives them serious access to your system.

How the Attack Works
It starts by redirecting your device to a fake login page, a captive portal. This leads to the ApolloShadow malware being downloaded and run.
Microsoft explains that once you're on this fake portal, Windows tries to check your internet connection. Instead of going to the real Microsoft site, you're redirected to a hacker-controlled domain. You'll probably see a certificate error, which will prompt you to download and run ApolloShadow. Tricky, right?
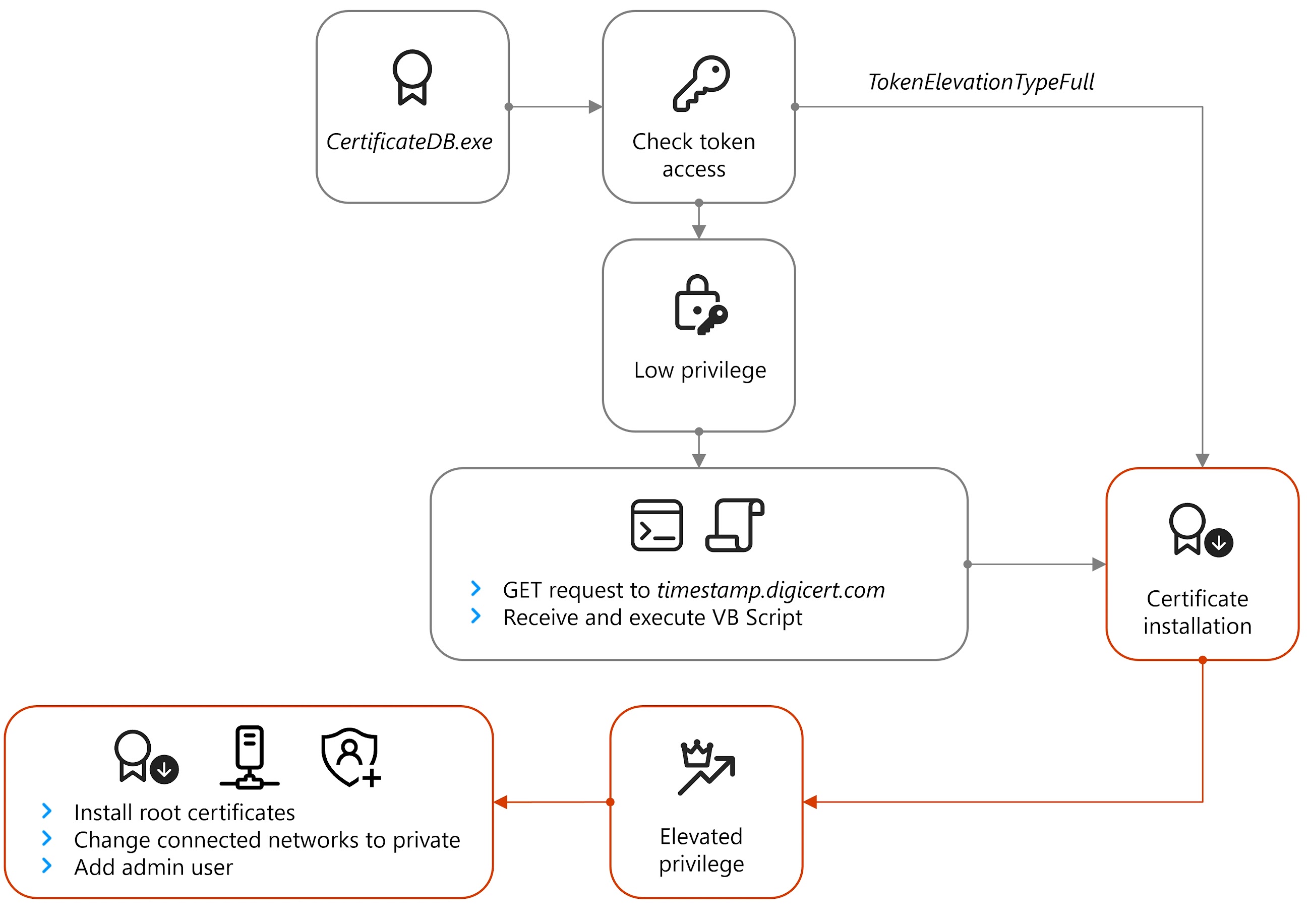
The malware then sends info about your computer to the hacker's server. If you don't have default admin settings, it runs another program called CertificateDB.exe and grabs another piece of code written in Visual Basic Script.
Finally, ApolloShadow restarts itself and asks you for admin privileges. If you give it those privileges, it's game over.
What ApolloShadow Does
If ApolloShadow gets those admin rights, it changes your network settings to "Private," making your computer discoverable and relaxing firewall rules. It even creates a new admin user called "UpdatusUser" with a password the hackers know.
As Microsoft puts it, "While we did not see any direct attempts for lateral movement, the main reason for these modifications is likely to reduce the difficulty of lateral movement on the network."
The malware then pretends to install digital certificates, adding two fake root certificates to your machine using a tool called certutil. It also drops a file called "wincert.js" so Firefox will trust those fake certificates.
How to Protect Yourself
If you're working at a foreign embassy in Moscow, here's what you should do:
- Use the principle of least privilege (PoLP). Only give users the access they absolutely need.
- Regularly check privileged groups. Make sure no unauthorized accounts have admin rights.
- Use a VPN. Route all your internet traffic through an encrypted tunnel to a trusted network or use a VPN service.
Stay safe out there!