North Korean Hackers Target Crypto Firms With Elaborate Job Scams
A North Korean hacking group, tracked as UNC4899, reportedly stole millions in cryptocurrency by infiltrating two organizations. Their method? Targeting employees on LinkedIn and Telegram with convincing job offers, then leveraging compromised cloud accounts and custom malware to access sensitive systems.

A North Korea-linked hacking group, known as UNC4899, is making headlines for its sophisticated attacks on cryptocurrency organizations. Their approach? Targeting employees through professional platforms like LinkedIn and Telegram.
According to Google's Cloud Threat Horizons Report, these hackers pose as recruiters offering freelance software development gigs. They then use social engineering to trick employees into running malicious Docker containers on their computers. You can check out the full Google report here.
UNC4899, also tracked as Jade Sleet, PUKCHONG, Slow Pisces, and TraderTraitor, has been active since at least 2020. They're notorious for targeting the cryptocurrency and blockchain industries. They overlap with other known threat actors, making attribution even more complex.
This group isn't just about small-time scams; they've been linked to some seriously big cryptocurrency heists. Think the Axie Infinity hack in March 2022 ($625 million), the DMM Bitcoin theft in May 2024 ($308 million), and the Bybit breach in February 2025, which resulted in a staggering $1.4 billion loss. You can read more about the crypto heists here.
And the sophistication doesn't stop there. They're even suspected of exploiting JumpCloud's infrastructure to target downstream customers in the crypto world.
DTEX reports that TraderTraitor is connected to the Third Bureau of North Korea's Reconnaissance General Bureau and is considered the most prolific of Pyongyang's hacking groups when it comes to stealing cryptocurrency.
How do they pull it off? By using job-themed lures or uploading malicious npm packages. They approach employees with enticing opportunities or ask them to collaborate on GitHub projects, which then leads to the execution of those malicious npm libraries.
Wiz, a cloud security firm, notes that TraderTraitor has a keen interest in cloud-based attack surfaces. Their goal is often to compromise companies that are customers of cloud platforms, rather than the platforms themselves. You can delve deeper into Wiz's report here.
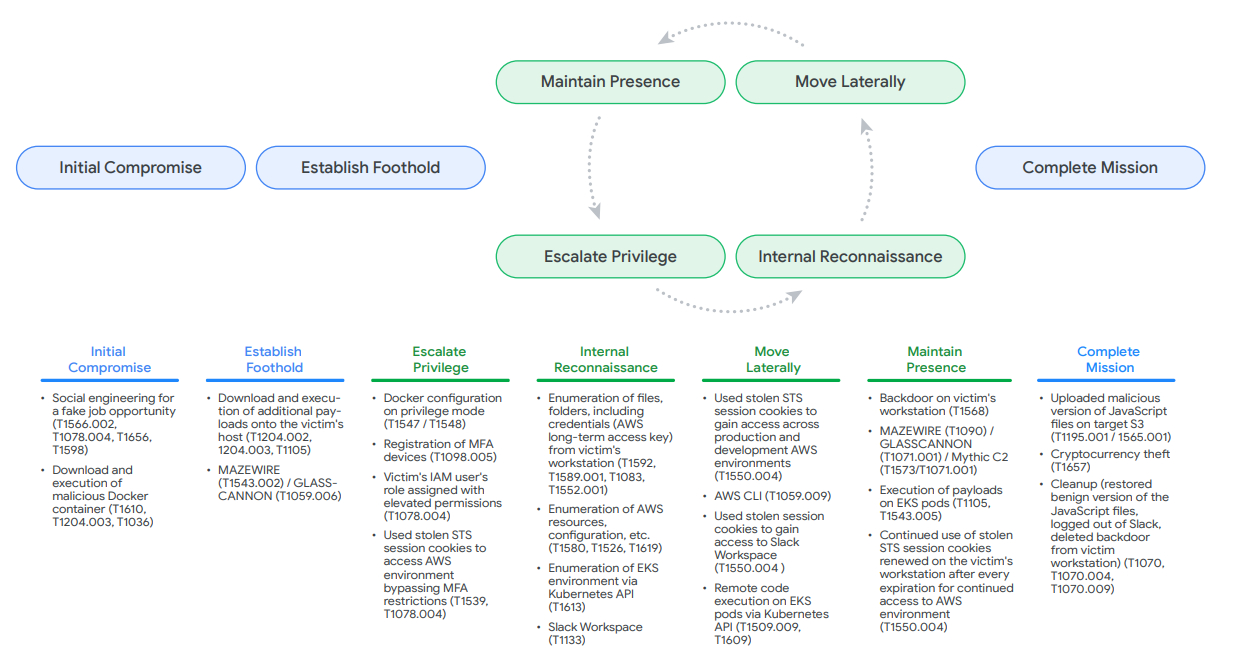
Google Cloud observed attacks targeting Google Cloud and Amazon Web Services (AWS) environments. This paved the way for a downloader called GLASSCANNON, which then deployed backdoors like PLOTTWIST and MAZEWIRE. These backdoors could then connect to a server controlled by the attackers.
In one Google Cloud incident, the hackers used stolen credentials to remotely interact with the system using Google Cloud CLI over an anonymous VPN. They carried out extensive reconnaissance and credential theft. Luckily, multi-factor authentication (MFA) initially stopped them.
But here's the kicker: "UNC4899 eventually figured out that the victim's account had administrative privileges and disabled the MFA requirements," Google explained. "After gaining access, they immediately re-enabled MFA to avoid detection." Sneaky, right?
The attack on the AWS environment followed a similar pattern. This time, the attackers used long-term access keys obtained from an AWS credential file to interact remotely via AWS CLI.
While access control measures prevented them from performing sensitive actions, Google found evidence suggesting they stole the user's session cookies. These cookies were then used to identify relevant CloudFront configurations and S3 buckets.
UNC4899 then "leveraged the inherent administrative permissions applied to their access to upload and replace existing JavaScript files with those containing malicious code," according to Google. This malicious code was designed to manipulate cryptocurrency functions and trigger transactions with the target organization's cryptocurrency wallet.
The result? In both cases, the attackers successfully withdrew several million dollars worth of cryptocurrency.
Adding to the concern, Sonatype reported flagging and blocking 234 unique malware npm and PyPI packages attributed to North Korea's Lazarus Group between January and July 2025. Some of these packages are designed to drop a credential stealer known as BeaverTail, linked to the Contagious Interview campaign.
"These packages mimic popular developer tools but function as espionage implants, designed to steal secrets, profile hosts, and open persistent backdoors into critical infrastructure," Sonatype said. "The surge of activity in H1 2025 demonstrates a strategic pivot: Lazarus is now embedding malware directly into open source package registries, namely npm and PyPI, at an alarming rate."