North Korean Hackers Target Crypto Jobs with BeaverTail Malware
Cybersecurity researchers have uncovered a new campaign by North Korean threat actors using deceptive job postings to distribute the BeaverTail and InvisibleFerret malware. These attackers are employing a technique reminiscent of the 'ClickFix' method, enticing victims with fake cryptocurrency job opportunities.

Security researchers are sounding the alarm about North Korean hackers upping their game. These actors, linked to the Democratic People's Republic of Korea (DPRK), are now using sneaky "ClickFix" tricks to spread malware like BeaverTail and InvisibleFerret. Think of ClickFix as a way to lure unsuspecting victims into clicking on malicious links or downloading infected files.
Oliver Smith, a researcher at GitLab Threat Intelligence, explained that these hackers are targeting marketing and trading roles in the cryptocurrency and retail sectors. It's a shift from their usual focus on software developers.
The "Contagious Interview" Campaign
You might remember the "Contagious Interview" campaign (also known as Gwisin Gang). Discovered by Palo Alto Networks, it's been used by North Korean operatives for a while. The goal? To distribute malware to software developers under the guise of a job assessment. Experts believe this group is part of the larger Lazarus hacking collective, and they've been at it since at least December 2022. They often target software developers under the pretext of a job assessment.
Over the years, BeaverTail has also popped up in fake npm packages and phony Windows videoconferencing apps. Written in JavaScript, BeaverTail acts as a data thief and a downloader for a Python-based backdoor called InvisibleFerret.
ClickFix: A New Twist
Here's where things get interesting. The hackers are now using the ClickFix social engineering tactic to deliver malware like GolangGhost, PylangGhost, and FlexibleFerret. This sub-group is tracked as ClickFake Interview.
The most recent wave of attacks, spotted in late May 2025, is notable for a couple of reasons:
- They're using ClickFix to deliver BeaverTail (instead of GolangGhost or FlexibleFerret).
- They're delivering the stealer as a compiled binary using tools like pkg and PyInstaller for Windows, macOS, and Linux.
Essentially, they're using a fake hiring platform built with Vercel to spread their malware. They're advertising crypto trader, sales, and marketing jobs at various Web3 companies, even urging people to invest in a specific Web3 company.
Smith pointed out that the focus on marketing applicants and impersonating a retail organization is a departure from BeaverTail's usual targeting of software developers and the crypto sector.
How the Attack Works
If you land on the fake job site, your IP address is logged. You're then asked to complete a video assessment. But here's the trick: a fake error message about a microphone issue pops up, and you're told to run a command specific to your operating system to "fix" the problem. In reality, this command deploys a stripped-down version of BeaverTail using a shell script or Visual Basic Script.
GitLab researchers explain that this BeaverTail variant is simplified. "The BeaverTail variant associated with this campaign contains a simplified information stealer routine and targets fewer browser extensions," they said. "The variant targets only eight browser extensions rather than the 22 targeted in other contemporary BeaverTail variants."
Another change is that they've removed the ability to steal data from web browsers other than Google Chrome. The Windows version of BeaverTail now relies on a password-protected archive to load Python dependencies related to InvisibleFerret.
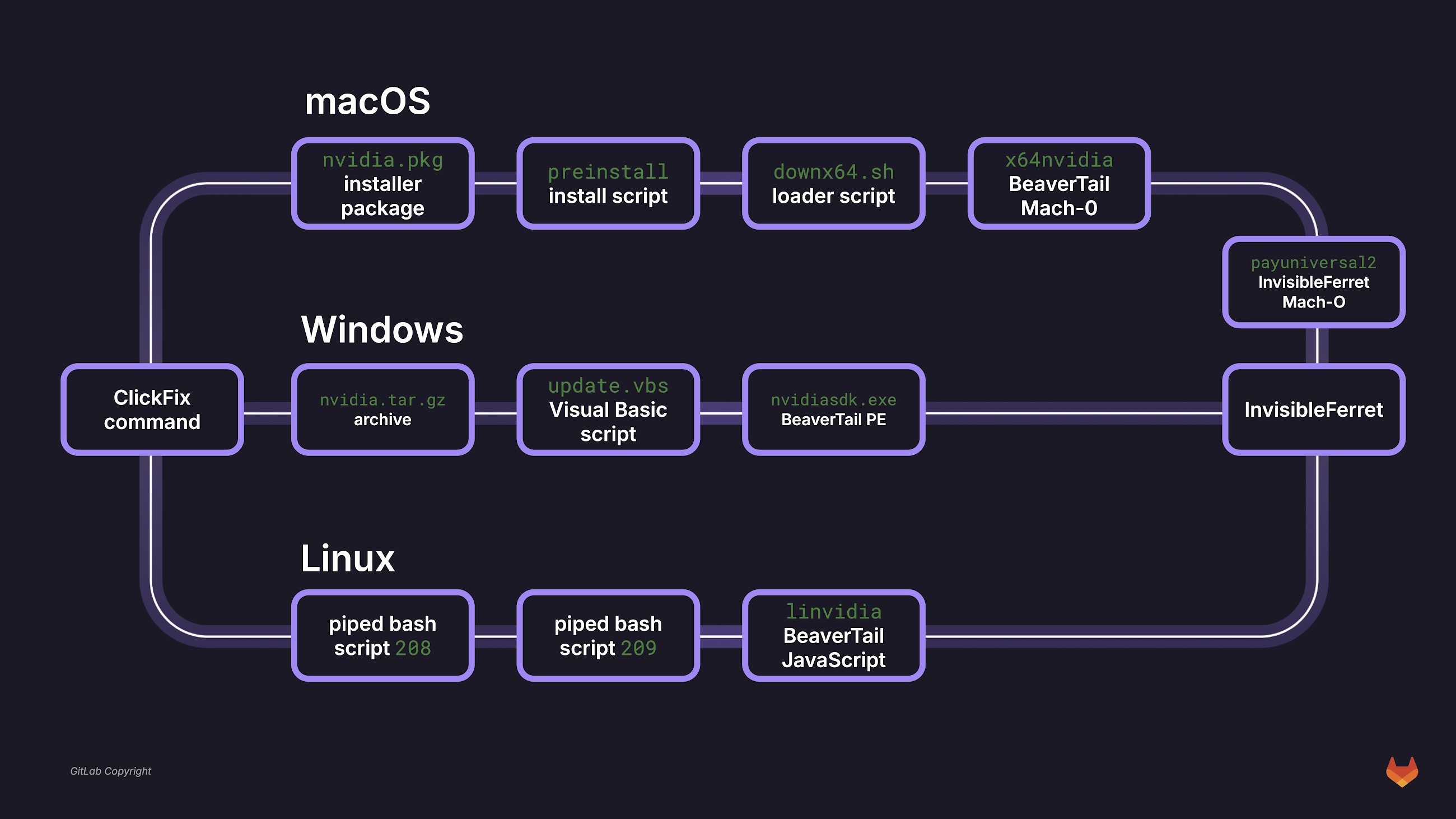
While password-protected archives aren't new, this is the first time they've been used for payload delivery with BeaverTail. This suggests the hackers are constantly tweaking their methods.
The limited number of secondary artifacts and the lack of sophisticated social engineering suggest this campaign might have been a small-scale test, unlikely to be deployed widely.
"The campaign suggests a slight tactical shift for a subgroup of North Korean BeaverTail operators, expanding beyond their traditional software developer targeting to pursue marketing and trading roles across cryptocurrency and retail sectors," GitLab noted. "The move to compiled malware variants and continued reliance on ClickFix techniques demonstrates operational adaptation to reach less technical targets and systems without standard software development tools installed."
The Bigger Picture
Around the same time, an investigation by SentinelOne, SentinelLabs, and Validin revealed that at least 230 people were targeted in fake crypto job interview attacks between January and March 2025 as part of the Contagious Interview campaign. The hackers impersonated companies like Archblock, Robinhood, and eToro.
This campaign involved using ClickFix to spread malicious Node.js applications called ContagiousDrop. These apps deploy malware disguised as updates or essential utilities. The payload is tailored to the victim's operating system and system architecture. It can also track victim activity and send an email alert when the victim starts the fake skill assessment.
The researchers found that the attackers were even monitoring cyber threat intelligence (CTI) related to their own infrastructure. They were also actively evaluating new infrastructure and looking for signs that their activity was being detected through Validin, VirusTotal, and Maltrail.
All this information helps them improve their campaigns, deploy new infrastructure quickly after takedowns, and generally sustain their operations.
The researchers believe it's more efficient for the hackers to simply replace compromised infrastructure than to try and secure their existing assets. "Given the continuous success of their campaigns in engaging targets, it may be more pragmatic and efficient for the threat actors to deploy new infrastructure rather than maintain existing assets," they explained.
In short, North Korean hackers are actively gathering intelligence and adapting their tactics to stay ahead of the game. Stay vigilant!