North Korean Hackers Upgrade OtterCookie Malware to Target Crypto Wallets
A North Korean hacking group known for its "Contagious Interview" campaign is now wielding a more sophisticated version of its OtterCookie malware. This updated threat boasts enhanced capabilities, including the ability to detect virtual machines and steal sensitive information like browser credentials and, crucially, data from Chrome and MetaMask crypto wallets.

Remember the "Contagious Interview" campaign? Well, the North Korean hackers behind it are at it again. This time, they're using upgraded versions of a nasty piece of cross-platform malware called OtterCookie. And what does OtterCookie do? It steals your credentials from web browsers and other files. Not good.
NTT Security Holdings spilled the beans, detailing how the attackers have been "actively and continuously" updating the malware. They rolled out versions v3 and v4 in February and April of this year alone!
The cybersecurity folks at NTT are keeping tabs on this group, calling them WaterPlum. You might also know them by other names like CL-STA-0240, DeceptiveDevelopment, or even Famous Chollima.
OtterCookie first popped up on NTT's radar last year, after being spotted in attacks since September 2024. It gets delivered through various shady methods, like malicious npm packages, fake GitHub/Bitbucket repositories, or even bogus videoconferencing apps. Once it's in, it phones home to an external server, ready to execute commands on the compromised system.
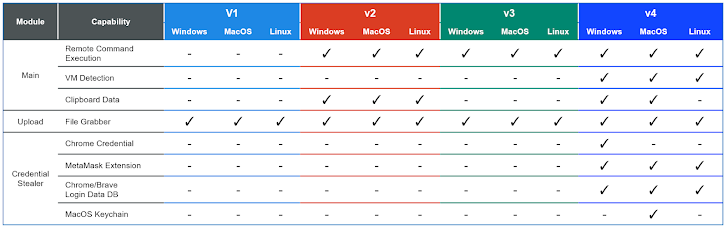
So, what's new with these updated versions? OtterCookie v3 now has a module that uploads files with specific extensions to that external server. Think environment variables, images, documents, spreadsheets, and even those all-important mnemonic and recovery phrases for your cryptocurrency wallets.
Interestingly, that file upload module was previously executed as a shell command received from the server in OtterCookie v2. Looks like they streamlined things a bit.
OtterCookie v4 takes things a step further. It adds modules to steal credentials from Google Chrome and grabs data from the MetaMask extension (for Chrome), Brave browser, and even your iCloud Keychain.
And if that wasn't enough, OtterCookie v4 can also sniff out if it's running in a virtual machine environment, specifically looking for Broadcom VMware, Oracle VirtualBox, Microsoft, and QEMU.
Here's a weird detail: one module steals Google Chrome credentials after decrypting them, while another grabs encrypted login data from Chrome and Brave. According to researchers Masaya Motoda and Rintaro Koike, "This difference in data processing or coding style implies that these modules were developed by different developers." Interesting, right?
All this comes as we're seeing more and more malicious payloads linked to the Contagious Interview campaign. It's clear these hackers are constantly tweaking their methods.
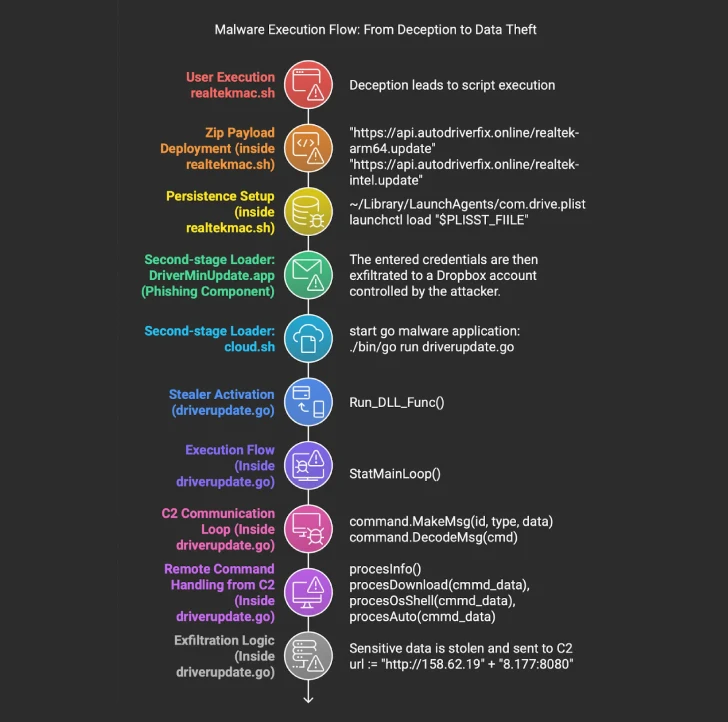
For instance, there's a Go-based information stealer disguised as a Realtek driver update ("WebCam.zip"). Open it, and it runs a script that downloads the stealer and launches a fake macOS app ("DriverMinUpdate.app") designed to steal your macOS system password.
It's thought that this malware is part of an updated version of the "ClickFake Interview" campaign from last month, which used those annoying "ClickFix" lures to fix non-existent audio and video problems during fake job interviews.
Moonlock, MacPaw's cybersecurity division, says the stealer's main job is to set up a persistent command-and-control channel, profile the infected system, and steal sensitive data. It does this by snooping around, stealing credentials, and executing remote commands.
The DriverMinUpdate app is likely part of a larger collection of similar malicious apps that have been found by various security researchers, including ChromeUpdateAlert, CameraAccess, and DriverEasy.
There's also a new malware family called Tsunami-Framework, delivered after a known Python backdoor called InvisibleFerret. This .NET-based modular malware is designed to steal all sorts of data from web browsers and crypto wallets.
HiSolutions, a German security company, reports that Tsunami-Framework can log keystrokes, collect files, and even has a botnet component that's still in early development.
ESET believes Contagious Interview is a new campaign from the infamous Lazarus Group, a North Korean hacking group known for espionage and financially motivated attacks. They do this to further the nation's strategic goals and get around international sanctions.
Earlier this year, Lazarus Group was linked to the massive billion-dollar heist from the cryptocurrency platform Bybit.
The North Korean IT Worker Threat Endures
Sophos revealed that the hackers behind the fraudulent IT worker scheme – also known as Famous Chollima, Nickel Tapestry, and Wagemole – are increasingly targeting organizations in Europe and Asia, and industries beyond just the tech sector. Their goal? To get jobs and funnel the money back to Pyongyang.
Sophos' SecureWorks Counter Threat Unit (CTU) says these threat actors often digitally manipulate photos for their fake resumes and LinkedIn profiles. "They commonly use stock photos over..."