Phishers Hide Behind Proofpoint, Intermedia to Snag Microsoft 365 Credentials
A sophisticated phishing campaign is using legitimate link wrapping services from Proofpoint and Intermedia to cloak malicious URLs and steal Microsoft 365 login credentials, cybersecurity researchers have revealed. The tactic cleverly bypasses common security defenses, making it harder for users to spot the danger.
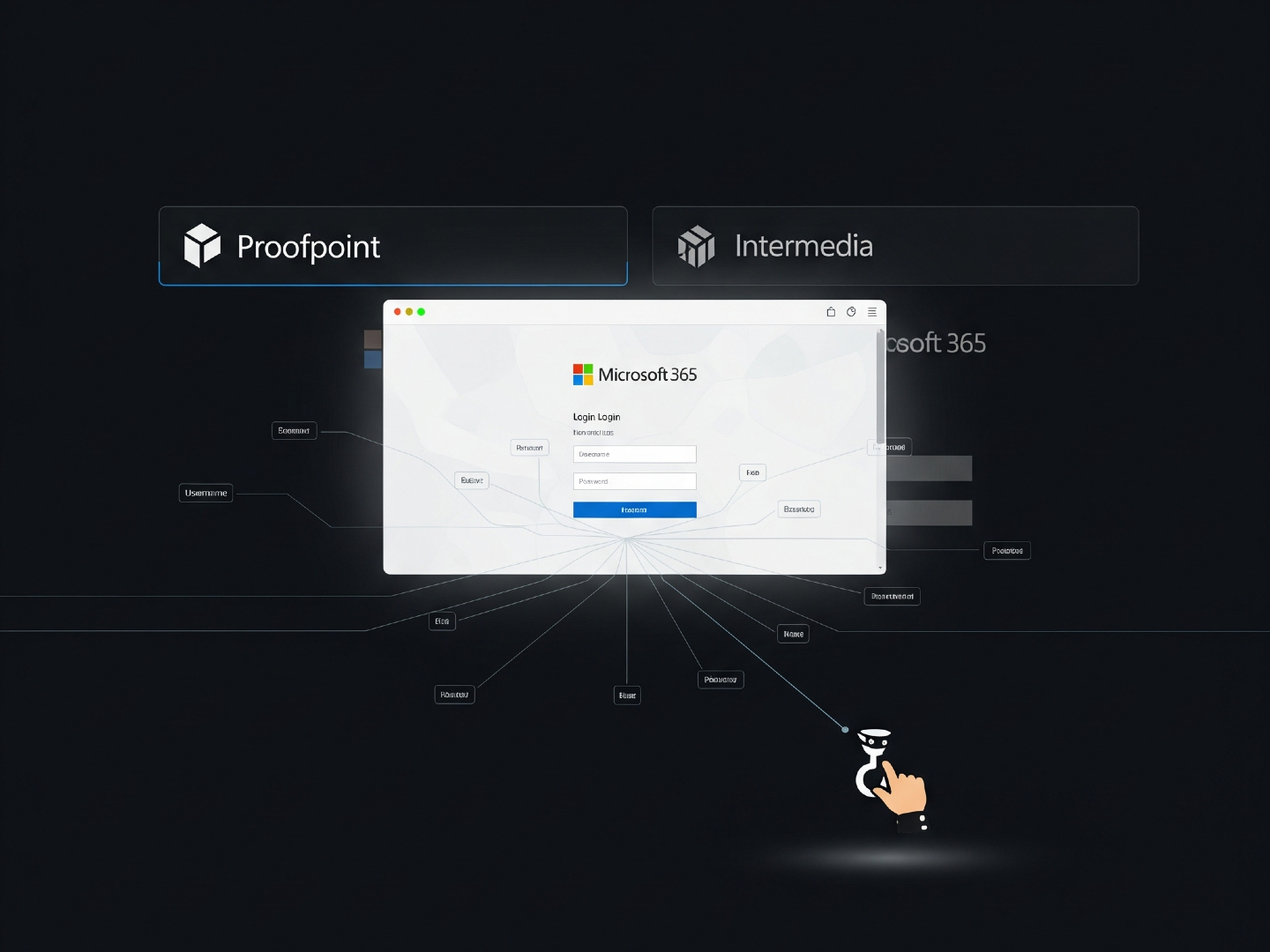
Cybersecurity researchers have uncovered a sneaky new phishing campaign. The bad guys are cleverly hiding their malicious attacks by exploiting link wrapping services from companies like Proofpoint and Intermedia. This lets them slip past security defenses.
Think of link wrapping like this: it's designed to protect you! When you click a link, services like Proofpoint scan it to make sure it's safe before you actually go to the website. They can block known bad destinations right when you click. That's according to the Cloudflare Email Security team, who reported on the issue.
But here's the catch: "While this is effective against known threats, attacks can still succeed if the wrapped link hasn't been flagged by the scanner at click time," Cloudflare explained.
This campaign, which has been active for the past couple of months, shows how criminals are always finding new ways to use legitimate tools for evil. In this case, they're redirecting victims to fake Microsoft 365 login pages to steal their credentials.
What's particularly alarming is that these attackers are gaining access to email accounts that already use link wrapping. So, any malicious link sent from one of those compromised accounts gets automatically rewritten with a wrapped link. It might look something like this: urldefense.proofpoint[.]com/v2/url?u=<malicious_website>.
Another key tactic involves what Cloudflare calls "multi-tiered redirect abuse." The attackers first hide their malicious links using a URL shortening service like Bitly. Then, they send that shortened link in an email from a Proofpoint-protected account, which wraps the link a second time!
This creates a chain of redirects. The URL goes through two layers of hiding – Bitly and Proofpoint's URL Defense – before the victim lands on the phishing page.
In the attacks Cloudflare observed, the phishing emails often pretend to be voicemail notifications. They urge you to click a link to listen to the message, but it really takes you to a fake Microsoft 365 login page designed to steal your username and password.
Other versions of this scam use similar tricks, but in emails that look like notifications about documents received on Microsoft Teams. These emails try to trick you into clicking on malicious links.
And yet another variation imitates Teams, claiming you have unread messages and inviting you to click a "Reply in Teams" button, which leads to a fake login page.
"By cloaking malicious destinations with legitimate urldefense[.]proofpoint[.]com and url[.]emailprotection URLs, these phishing campaigns' abuse of trusted link wrapping services significantly increases the likelihood of a successful attack," Cloudflare warned.
This news comes alongside a recent increase in phishing attacks that use Scalable Vector Graphics (SVG) files to bypass spam filters and deliver malware.
"Unlike JPEG or PNG files, SVG files are written in XML and support JavaScript and HTML code," the New Jersey Cybersecurity and Communications Integration Cell (NJCCIC) explained last month. "They can contain scripts, hyperlinks, and interactive elements, which can be exploited by embedding malicious code within harmless SVG files."
We've also seen phishing campaigns that embed fake Zoom video call links in emails. Clicking these links starts a chain of redirects that leads to a realistic-looking fake Zoom page. After a "meeting connection timed out" message, you're taken to a phishing page that asks you to enter your credentials to rejoin the meeting.
"Unfortunately, instead of 'rejoining,' the victim's credentials along with their IP address, country, and region are exfiltrated via Telegram, a messaging app notorious for 'secure, encrypted communications,' and inevitably sent to the threat actor," Cofense reported.