Phishing Attack Leverages 27 Malicious npm Packages to Snare Credentials
A sophisticated spear-phishing campaign has infiltrated the npm registry, using over two dozen malicious packages as infrastructure to steal login credentials. Cybersecurity experts are calling the operation "sustained and targeted," highlighting the growing threat of supply chain attacks in the open-source ecosystem.

Cybersecurity researchers have uncovered a "sustained and targeted" spear-phishing campaign leveraging the npm registry to steal credentials. Think of it as a digital con, specifically designed to trick the right people.
According to Socket, the attackers uploaded 27 malicious npm packages using six different aliases. Their primary targets? Sales and commercial staff working at organizations tied to critical infrastructure in the U.S. and allied countries.
"Over five months, this operation turned 27 npm packages into a platform for hosting browser-based lures," explained researchers Nicholas Anderson and Kirill Boychenko in their report. "These lures mimic document-sharing portals and Microsoft sign-in pages, aiming to steal credentials from 25 organizations in manufacturing, industrial automation, plastics, and healthcare."
Here's a list of the dodgy packages to watch out for:
- adril7123
- ardril712
- arrdril712
- androidvoues
- assetslush
- axerification
- erification
- erificatsion
- errification
- eruification
- hgfiuythdjfhgff
- homiersla
- houimlogs22
- iuythdjfghgff
- iuythdjfhgff
- iuythdjfhgffdf
- iuythdjfhgffs
- iuythdjfhgffyg
- jwoiesk11
- modules9382
- onedrive-verification
- sarrdril712
- scriptstierium11
- secure-docs-app
- sync365
- ttetrification
- vampuleerl
The goal isn't to get users to install these packages. Instead, the attackers are using npm and its content delivery networks (CDNs) as a convenient, resilient hosting service. They use it to deliver phishing pages – client-side HTML and JavaScript – disguised as secure document-sharing portals. Once a victim lands on one of these fake pages, they are redirected to a Microsoft sign-in page that conveniently has their email address pre-filled.
Why use package CDNs? Simple. It turns a legitimate service into infrastructure that's tough to take down. Plus, if one account gets flagged, attackers can easily switch to new aliases and package names.
These packages also employ several techniques to make analysis difficult. They filter out bots, evade sandboxes, and require mouse or touch input before redirecting victims to the credential harvesting infrastructure. The JavaScript code is often obfuscated or minified, making automated inspection a real headache.
Another trick: honeypot form fields. These fields are hidden from real users but are likely to be filled by automated crawlers. If a crawler fills them, the attack is aborted, adding another layer of defense for the attackers.
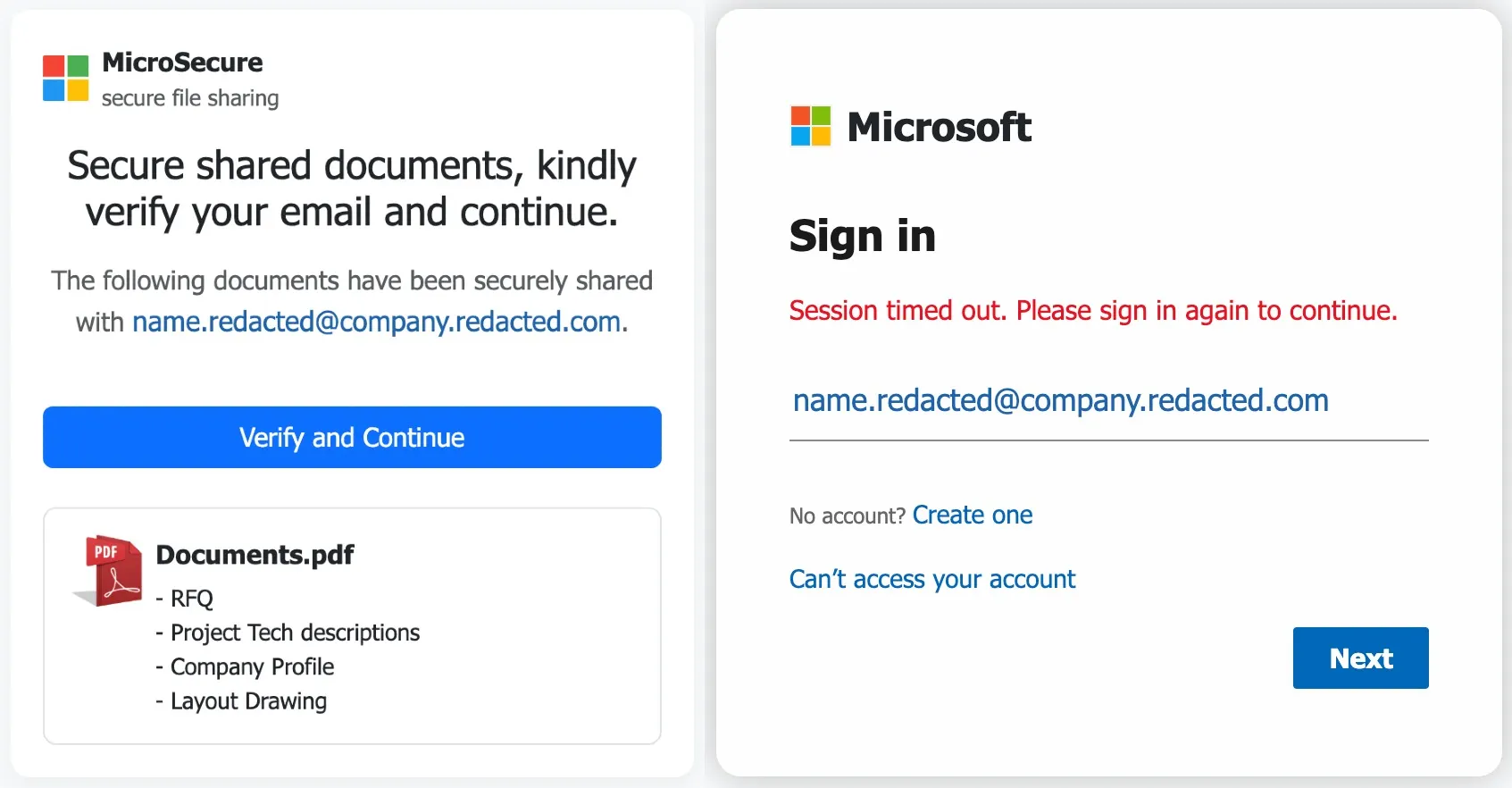
Socket noted that the domains used in these packages are linked to adversary-in-the-middle (AitM) phishing infrastructure associated with Evilginx, a popular open-source phishing kit.
This isn't the first time npm has been abused for phishing. Back in October 2025, we reported on a campaign called Beamglea, where attackers uploaded 175 malicious packages for credential harvesting. This latest attack appears to be separate from Beamglea.
"This campaign follows a similar playbook but uses different delivery methods," Socket stated. "Instead of simple redirect scripts, these packages deliver a complete, browser-executed phishing flow within an embedded HTML and JavaScript bundle that runs when loaded."
What's particularly concerning is that the phishing packages hard-code 25 email addresses belonging to specific individuals. These people work in account management, sales, and business development within manufacturing, industrial automation, plastics, polymer supply chains, and healthcare across several countries, including Austria, Belgium, Canada, France, Germany, Italy, Portugal, Spain, Sweden, Taiwan, Turkey, the U.K., and the U.S.
It's unclear how the attackers obtained these email addresses. However, many of the targeted companies attend major international trade shows like Interpack and K-Fair. It's suspected the attackers may have gathered the information from these events, combining it with general online reconnaissance.
"In several instances, target locations differed from corporate headquarters," the company added, "suggesting a focus on regional sales staff, country managers, and local commercial teams, rather than just corporate IT."
So, what can you do? Enforce strong dependency verification, monitor for unusual CDN requests from outside development environments, implement phishing-resistant multi-factor authentication (MFA), and keep an eye out for suspicious post-authentication activity.
This news comes as Socket reports a growing trend of destructive malware across npm, PyPI, NuGet Gallery, and Go module indexes. Attackers are using techniques like delayed execution and remotely controlled kill switches to avoid early detection, fetching executable code at runtime with tools like wget and curl.
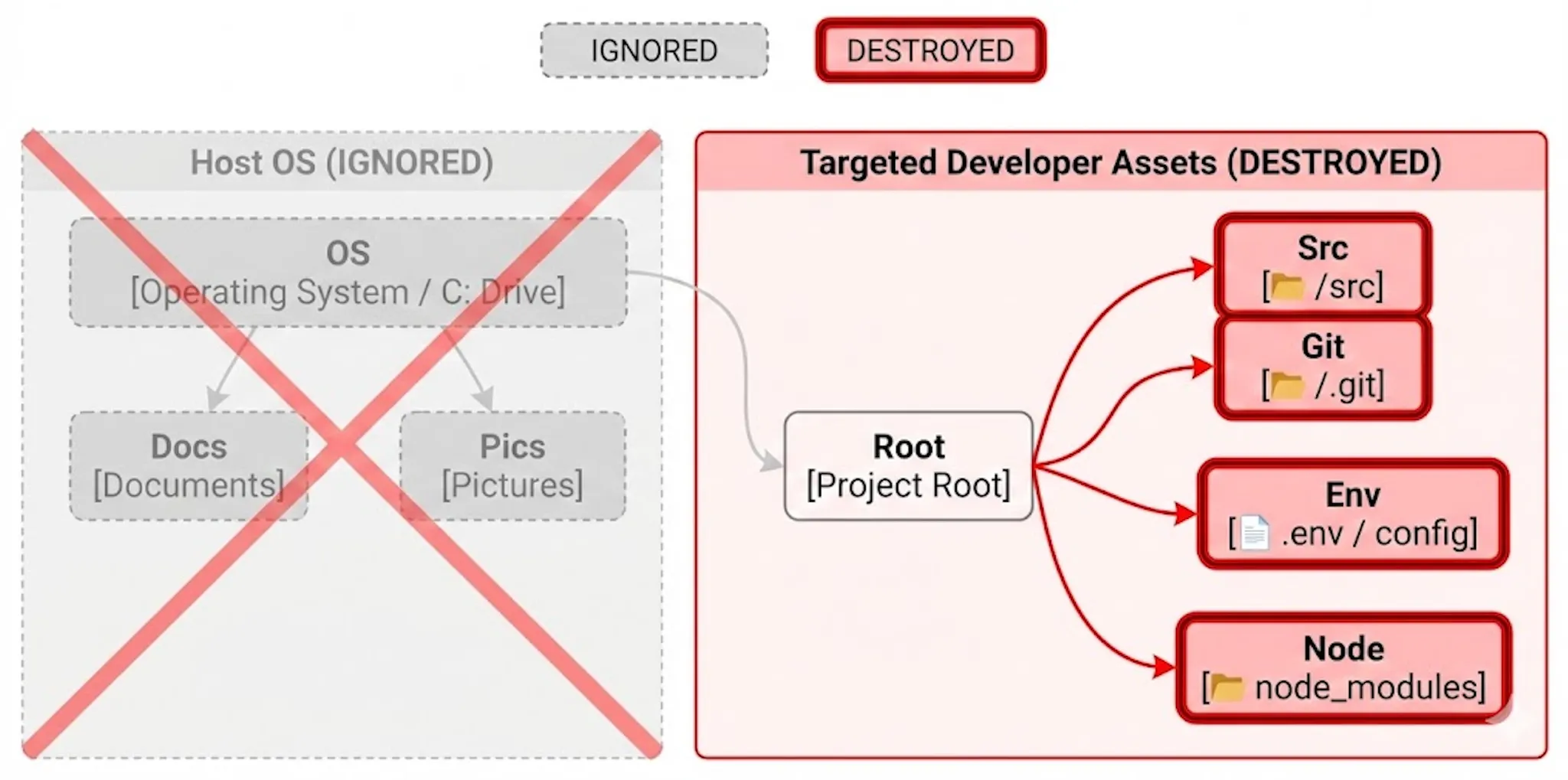
"These packages don't just wipe everything," explained researcher Kush Pandya in a report. "They target what matters most to developers: Git repositories, source directories, configuration files, and CI build outputs."
He added, "They often integrate this destructive logic into otherwise functional code paths and use standard lifecycle hooks for execution. This means the malware might never need explicit importing or invocation by the application itself."