Phishing Attacks Hide Inside SVG Images, Bypassing Detection
A sneaky new phishing campaign is using seemingly harmless Scalable Vector Graphics (SVG) files to bypass security defenses. Researchers at VirusTotal discovered 44 previously undetected SVG images hosting Base64-encoded phishing pages, with many impersonating the Colombian judicial system to trick victims.

Cybersecurity researchers have spotted a new malware campaign. This time, the bad guys are using Scalable Vector Graphics (SVG) files in phishing attacks that pretend to be from the Colombian judicial system.
According to VirusTotal, these SVG files are making their way into inboxes via email. Once opened, they execute a hidden JavaScript code that decodes and injects a Base64-encoded HTML phishing page. This page is designed to look like the official portal for the Fiscalía General de la Nación, which is the Attorney General's Office of Colombia.
The fake page puts on a show, simulating a government document download with a convincing progress bar. But behind the scenes, it's secretly downloading a ZIP archive. What exactly is in that ZIP file? That remains undisclosed.
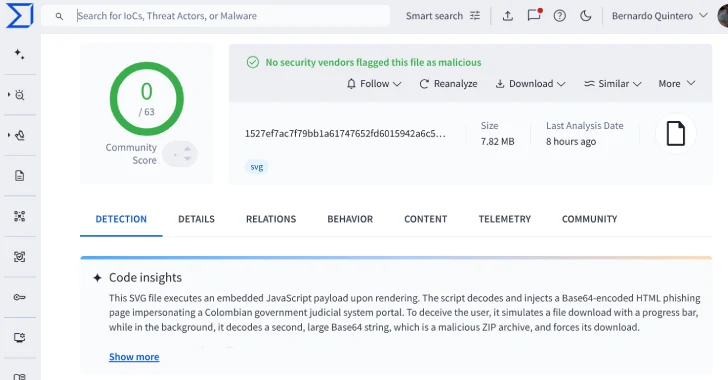
VirusTotal, the malware scanning service owned by Google, found 44 unique SVG files associated with this campaign. What's concerning is that antivirus software hasn't detected them. The attackers are using tricks like obfuscation, polymorphism (changing the code), and stuffing the files with junk code to avoid being flagged.
In total, researchers have found 523 of these SVG files "in the wild," with the earliest one showing up around August 14, 2025.
"Looking deeper, we saw that the earliest samples were larger, around 25 MB, and the size decreased over time, suggesting the attackers were evolving their payloads," VirusTotal said.
Another Threat: Atomic macOS Stealer (AMOS)
This news comes alongside reports of cracked software and "ClickFix" tactics being used to infect Apple macOS systems with a nasty piece of malware called Atomic macOS Stealer (AMOS). This malware can lead to credential stuffing, financial theft, and other serious attacks.
Trend Micro explains:
"AMOS is designed for broad data theft, capable of stealing credentials, browser data, cryptocurrency wallets, Telegram chats, VPN profiles, keychain items, Apple Notes, and files from common folders... As macOS devices gain ground in enterprise settings, they have become a more attractive and lucrative focus for attackers."
Essentially, users searching for cracked software on shady sites like haxmac[.]cc are being tricked into downloading malicious files. These files come with instructions that lead users to run commands in the Terminal app, which then installs AMOS.
It's important to remember that macOS has built-in protections (Gatekeeper) that prevent the installation of unsigned .dmg files. This means the attackers have to get creative to bypass these safeguards.

Apple has added even stronger protections in macOS Sequoia, which block the installation of malicious or unsigned .dmg files by default. This makes it harder for AMOS to infect systems, but it doesn't eliminate the risk entirely. Attackers are adapting.
That's where "ClickFix" comes in. It allows the stealer to be installed through the Terminal app using a curl command provided on the download page.
Trend Micro notes, "While macOS Sequoia's enhanced Gatekeeper protections successfully blocked traditional .dmg-based infections, threat actors quickly pivoted to terminal-based installation methods that proved more effective in bypassing security controls. This shift highlights the importance of defense-in-depth strategies that don't rely solely on built-in operating system protections."
Gamers Beware: StealC Malware on the Prowl
And there's more! A large-scale cyber campaign is targeting gamers looking for cheats. This campaign uses the StealC stealer, along with cryptocurrency theft malware, and has already netted the attackers over $135,000.
According to CyberArk, this campaign is using StealC's loader capabilities to download additional malicious software, including a cryptocurrency stealer that can steal digital assets from infected machines.