Qilin Ransomware Gang Offers Legal Help to Extort Bigger Payouts
The Qilin ransomware group is upping the ante, now providing legal assistance to its affiliates. This aggressive tactic aims to squeeze even larger ransoms from victims as Qilin seeks to dominate the ransomware landscape amid disruption among its competitors.

Ransomware Gang Qilin Offers Legal Muscle to Pressure Victims
The Qilin ransomware group is upping the ante. They're now offering legal counsel to their affiliates, aiming to put even more pressure on victims to cough up the ransom. It seems they're stepping up their game as other ransomware groups falter.
According to Cybereason, the new "Call Lawyer" feature is directly integrated into the affiliate panel. Pretty slick, right?
This move signals a resurgence for Qilin. Big names like LockBit and Black Cat have been stumbling lately, leaving a gap that Qilin is eager to fill. This group, also known as Gold Feather and Water Galura, has been around since October 2022.
Dark web data shows Qilin leading the pack in April 2025 with 72 victims. While May saw them slip slightly behind Safepay and Luna Moth, they're still a major player. Overall, they're the third most active group this year, claiming 304 victims.
Qualys noted that Qilin's rise is due to its mature ecosystem, extensive support, and highly targeted attacks designed for big payouts. You can read their full analysis here.
It looks like some affiliates from the RansomHub group have jumped ship to Qilin, contributing to their recent surge in activity.
Researchers at Cybereason explain that Qilin boasts a technically advanced infrastructure with payloads built in Rust and C, loaders with advanced evasion, and an affiliate panel loaded with features. Read more on Cybereason's blog.
They're not just about the ransomware itself. Qilin offers spam services, massive data storage, legal advice, and a whole suite of operational features. They're positioning themselves as a full-service cybercrime platform.
More Than Just Ransomware
Qilin is expanding its services with new features on its affiliate panel. This includes the aforementioned legal assistance, a team of in-house journalists (yikes!), and the ability to launch DDoS attacks. They've even added a tool for spamming corporate emails and phone numbers.
These expansions suggest Qilin is aiming to be a one-stop shop for cybercrime, moving beyond just ransomware.
A translated forum post announcing the new legal capabilities reads: "If you need legal consultation regarding your target, simply click the 'Call lawyer' button located within the target interface, and our legal team will contact you privately to provide qualified legal support."
The idea is that "the mere appearance of a lawyer in the chat can exert indirect pressure on the company and increase the ransom amount, as companies want to avoid legal proceedings." Sneaky.
Meanwhile, Intrinsec found that a Rhysida affiliate is using Eye Pyramid C2, an open-source utility, to maintain access and deliver additional payloads. More info can be found here.
It's worth noting that Eye Pyramid C2 is the same Python-based backdoor used by RansomHub in Q4 2024. You can read more on evading EDRs here.
Also, a recent analysis of leaked Black Basta chat logs revealed information about a threat actor known as "tinker."
Intel 471 says tinker was a trusted aide to the group's leader and joined as a "creative director" after working in call centers and as a negotiator for BlackSuit. More details on tinker's role.
Tinker was responsible for gaining initial access to organizations, analyzing financial data, and writing phishing emails. Essentially, they were a key part of the extortion process.
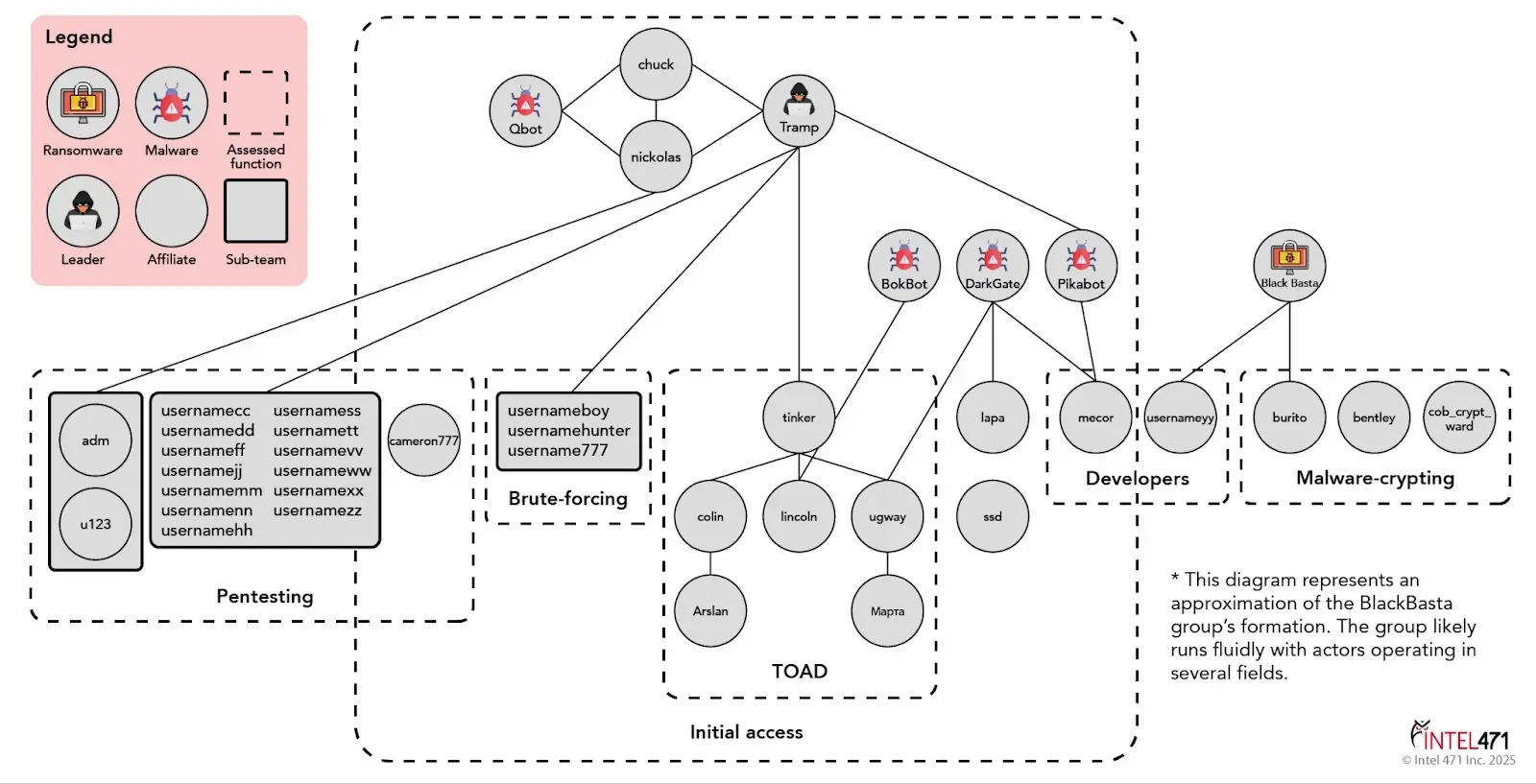
Notably, tinker also came up with the Microsoft Teams phishing scenario, where attackers posed as IT and tricked victims into installing remote desktop tools.
Intel 471 explains that after the software was installed, Black Basta's penetration testers would secure persistent access to the system.
Tinker received at least $105,000 in cryptocurrency for their efforts. It's unclear which group they're currently working for.
Finally, news broke of the extradition of a member of the Ryuk ransomware group to the U.S. This individual is accused of being an initial access broker. The suspect was arrested in Kyiv at the request of U.S. law enforcement. More on the extradition.