Record-Breaking DDoS Attack Swamps Hosting Provider with 7.3 Tbps of Traffic
Cloudflare revealed Thursday it successfully mitigated the largest distributed denial-of-service (DDoS) attack in history, a massive assault that peaked at a staggering 7.3 terabits per second. The company's automated systems blocked the attack, preventing significant disruption to its services.

Massive DDoS Attack Topples Records, Cloudflare Steps In
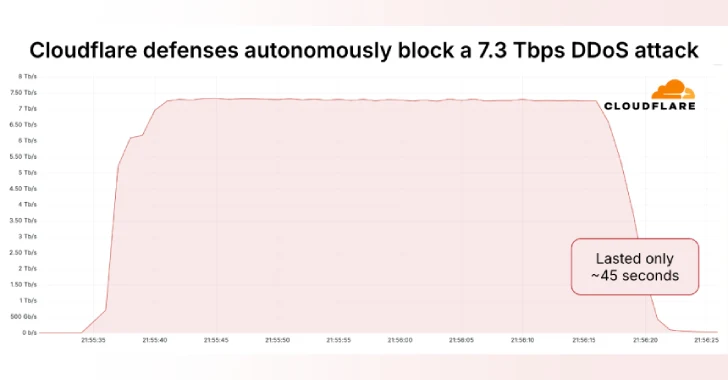
Hold on to your hats, folks! Cloudflare just announced they successfully blocked the largest Distributed Denial-of-Service (DDoS) attack ever seen. We're talking a whopping 7.3 terabits per second (Tbps)!
This monster attack, which happened back in mid-May 2025, was aimed at a hosting provider who, for now, shall remain nameless. Talk about a bad day at the office!
Omer Yoachimik from Cloudflare explained that these kinds of attacks are increasingly targeting hosting providers and critical internet infrastructure. And get this: this particular 7.3 Tbps assault dumped a staggering 37.4 terabytes of data in just 45 seconds!
DDoS Attacks on the Rise
This isn't the first rodeo for Cloudflare. Back in January, they reported stopping a 5.6 Tbps DDoS attack targeting an ISP in Eastern Asia. That one came from a Mirai botnet variant dating back to October 2024.
And in April 2025? They fended off a 6.5 Tbps flood, likely originating from Eleven11bot, a botnet of around 30,000 compromised webcams and video recorders. That hyper-attack lasted just under a minute.
Breaking Down the 7.3 Tbps Beast
So, what made this latest attack so huge? It targeted an average of 21,925 destination ports on a single IP address belonging to the hosting provider, peaking at a crazy 34,517 ports per second!
This wasn't just one type of attack either. It was a multi-vector assault, combining UDP floods, QOTD reflection attacks, echo and NTP reflection attacks, a Mirai UDP flood, portmap floods, and RIPv1 amplification. The UDP flood alone accounted for nearly all (99.996%) of the attack traffic.
The attack came from over 122,145 source IP addresses across 5,433 Autonomous Systems (AS) in 161 countries. Top sources included Brazil, Vietnam, Taiwan, China, Indonesia, Ukraine, Ecuador, Thailand, the US, and Saudi Arabia.
As Yoachimik pointed out, the average number of unique source IP addresses per second was 26,855, with a peak of 45,097. That's a lot of computers throwing junk traffic!
Specifically, Telefonica Brazil (AS27699) accounted for over 10% of the attack traffic, followed by Viettel Group (AS7552) with almost 10%. China Unicom (AS4837) and Chunghwa Telecom (AS3462) contributed smaller, but still significant, amounts.
RapperBot: The Extortionist Botnet
And speaking of DDoS attacks, the QiAnXin XLab team revealed that the RapperBot botnet was behind an attack on AI company DeepSeek in February 2025. The latest versions of RapperBot are even trying to extort victims, demanding "protection fees" to avoid future attacks!
RapperBot-infected devices are primarily located in China, the US, Israel, Mexico, the UK, Greece, Iran, Australia, Malaysia, and Thailand. This botnet has been active since 2022, so it's not exactly new to the game.
How RapperBot Works
RapperBot targets routers, NAS devices, and video recorders with weak default passwords or firmware vulnerabilities. Once in, it drops malware that connects to a remote server via DNS TXT records to receive attack commands.
The malware also uses custom encryption to protect the TXT records and the command-and-control (C2) domain names it uses. Sneaky!
The Chinese security vendor noted that RapperBot's attack activity has been significantly active since March, averaging over 100 attack targets per day with over 50,000 bots observed. That's a serious force to be reckoned with.
RapperBot's targets span various industries, including public management, social security, internet platforms, manufacturing, and financial services. Basically, no one is safe.