Silk Typhoon's Cyber Arsenal Revealed Through Patent Filings
Companies tied to Silk Typhoon, the Chinese state-sponsored hacking group also known as Hafnium, appear to be patenting tools designed for cyber espionage. The discovery of more than fifteen such patents offers a rare glimpse into China's opaque cyber contracting industry and the offensive technologies it develops.

It turns out that Chinese companies with ties to the state-sponsored hacking group Silk Typhoon (also known as Hafnium) have been quietly securing patents for some pretty potent cyber tools. These patents offer a rare glimpse into the murky world of cyber contractors and their offensive capabilities.
According to a new report from SentinelOne, these patents cover a range of tools, including those designed for encrypted data collection from endpoints, forensic analysis of Apple devices, and even remote access to routers and smart home gadgets. Think about that for a second!
Dakota Cary, a China expert at SentinelLabs, puts it this way: "This new insight into the Hafnium-affiliated firms' capabilities highlights an important deficiency... threat actor tracking typically links campaigns to a named actor." She added, "Our research demonstrates the strength in identifying not only the individuals behind attacks, but the companies they work for, the capabilities those companies have..."
These findings dovetail with the U.S. Department of Justice's (DoJ) indictment of Xu Zewei and Zhang Yu back in July 2025. These two individuals, allegedly working for China's Ministry of State Security (MSS), were accused of masterminding the 2021 Microsoft Exchange Server exploitation campaign that leveraged the ProxyLogon zero-days.
Court documents suggest Xu Zewei was employed by Shanghai Powerock Network Co. Ltd., while Zhang Yu worked at Shanghai Firetech Information Science and Technology Company, Ltd. Both were said to be operating under the direction of the Shanghai State Security Bureau (SSSB).
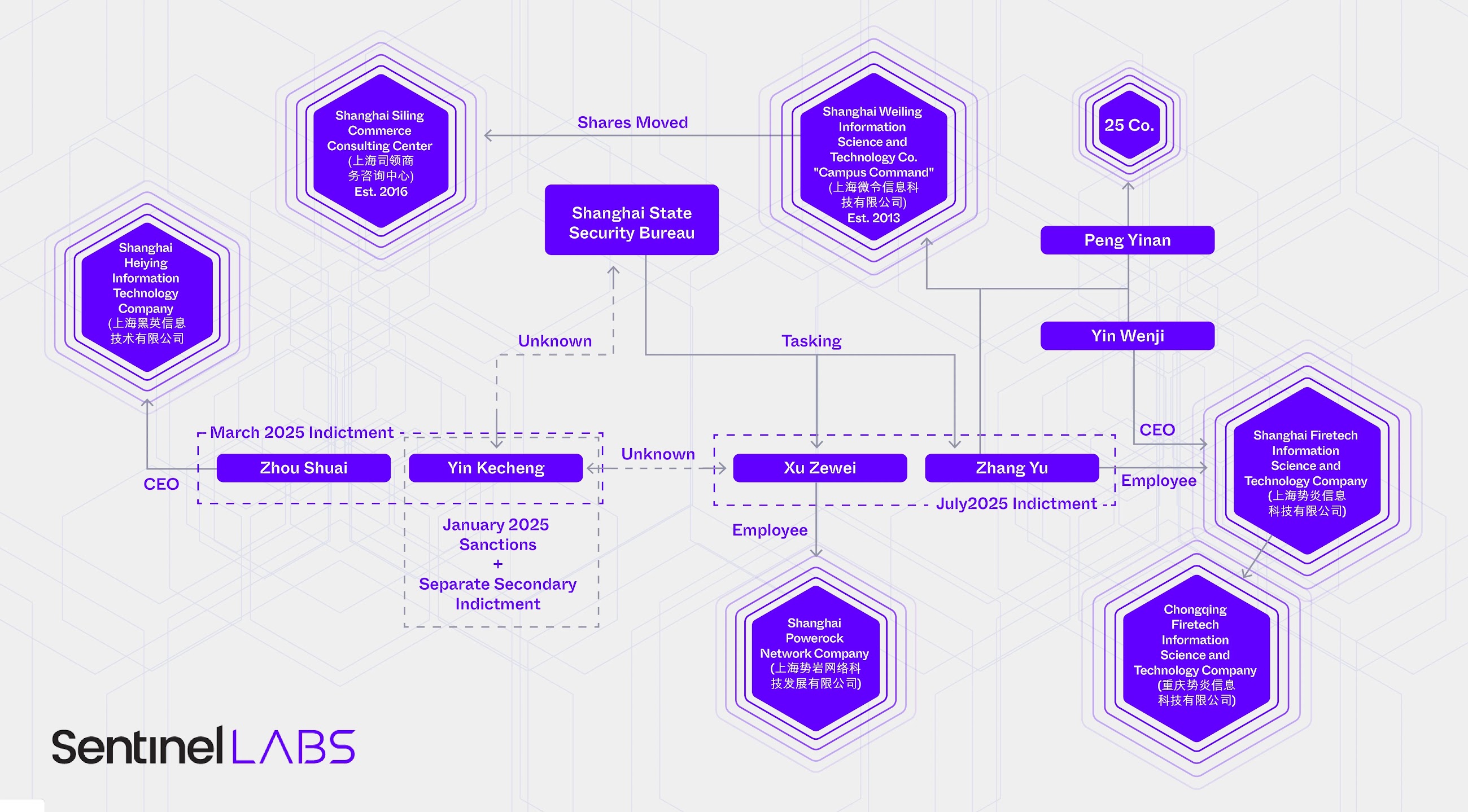
Here's a twist: Natto Thoughts reported that Powerock shut down its business on April 7, 2021, not long after Microsoft publicly blamed China for the Exchange Server attacks. Xu Zewei then landed at Chaitin Tech, another cybersecurity firm, before moving on to Shanghai GTA Semiconductor Ltd. as an IT manager.
And there's more! Yin Kecheng, another hacker linked to Silk Typhoon, apparently worked for Shanghai Heiying Information Technology Company, Limited, founded by Zhou Shuai, a Chinese "patriotic hacker" and alleged data broker.
According to Cary, "Shanghai Firetech worked on specific tasking handed down from MSS officers... Shanghai Firetech and co-conspirators earned an on-going, trusting relationship with the MSS's premier regional office, the SSSB."
She concludes that the relationship between the SSSB and these companies "contours the tiered system of offensive hacking outfits in China."
Further digging into the tangled web of connections has revealed patents filed by Shanghai Firetech and Shanghai Siling Commerce Consulting Center (co-founded by Yu and Yin Wenji, CEO of Shanghai Firetech). These patents focus on tools designed to collect "evidence" from Apple devices, routers, and security equipment.
There's even evidence suggesting Shanghai Firetech is developing solutions for close-access operations against specific individuals.
"The variety of tools under the control of Shanghai Firetech exceeds those attributed to Hafnium and Silk Typhoon publicly," Cary noted. "The capabilities may have been sold to other regional MSS offices, and thus not attributed to Hafnium, despite being owned by the same corporate structure." In other words, this could just be the tip of the iceberg.