Silver Fox Gang Weaponizes Legitimate Driver to Spread ValleyRAT
A sophisticated hacking group dubbed Silver Fox is using a clever trick to bypass security defenses: they're exploiting a vulnerable, but legitimately signed, driver from WatchDog Anti-malware. This "Bring Your Own Vulnerable Driver" (BYOVD) attack allows them to disable security software and deploy the ValleyRAT malware on targeted systems.
The hacking group known as Silver Fox is at it again, and this time they're using a sneaky trick: exploiting a previously unknown vulnerability in a driver associated with WatchDog Anti-malware. It's all part of a "Bring Your Own Vulnerable Driver" (BYOVD) attack designed to cripple security software on infected computers.
So, what's the vulnerable driver? It's "amsdk.sys" (version 1.0.600), a 64-bit Windows kernel device driver that's been legitimately signed. Experts believe it's built using the Zemana Anti-Malware SDK.
Check Point researchers explained, "This driver, built on the Zemana Anti-Malware SDK, was Microsoft-signed, not listed in the Microsoft Vulnerable Driver Blocklist, and not detected by community projects like LOLDrivers."
Here's the breakdown of the attack: Silver Fox uses a two-pronged approach. For older Windows 7 systems, they use a known vulnerable Zemana driver ("zam.exe"). But for computers running Windows 10 or 11, they deploy the undetected WatchDog driver.
The WatchDog Anti-malware driver has some serious flaws. It can terminate any process, regardless of whether it's protected. It's also vulnerable to local privilege escalation, giving attackers free rein over the driver's device.
Check Point first noticed this campaign in late May 2025. The ultimate goal? To disable endpoint protection, paving the way for malware deployment and persistence without raising any red flags.
As seen in previous attacks, the final payload is ValleyRAT (aka Winos 4.0), giving the attackers remote access and control. Check Point says the attacks use a single, all-in-one loader that includes anti-analysis features, both drivers, antivirus killer logic, and the ValleyRAT DLL downloader.
"Upon execution, the sample performs a few common anti-analysis checks, such as Anti-VM (detection of virtual environments), Anti-Sandbox (detection of execution within a sandbox), hypervisor detection, and others," Check Point noted. "If any of these checks fail, the execution is aborted, and a fake system error message is displayed."
The downloader then reaches out to a command-and-control (C2) server to grab the modular ValleyRAT backdoor and install it on the victim's machine.
After being notified, Watchdog released a patch (version 1.1.100) to fix the privilege escalation issue. However, the arbitrary process termination bug remains. The attackers quickly adapted, modifying the driver with a simple one-byte change to bypass hash-based blocklists without invalidating the Microsoft signature.
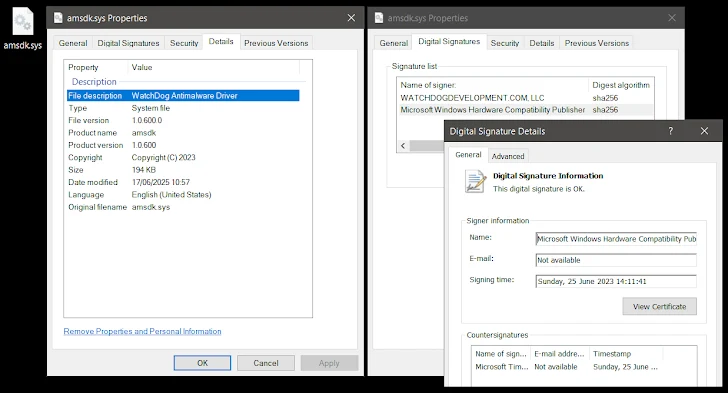
"By flipping a single byte in the unauthenticated timestamp field, they preserved the driver's valid Microsoft signature while generating a new file hash, effectively bypassing hash-based blocklists," Check Point explained. "This subtle yet efficient evasion technique mirrors patterns seen in earlier campaigns."
In essence, "This campaign demonstrates how threat actors are moving beyond known weaknesses to weaponize unknown, signed drivers—a blind spot for many defense mechanisms. The exploitation of a Microsoft-signed, previously unclassified vulnerable driver, combined with evasive techniques such as signature manipulation, represents a sophisticated and evolving threat."
Silver Fox, also known as SwimSnake, The Great Thief of Valley (or Valley Thief), UTG-Q-1000, and Void Arachne, has been highly active since early last year. They primarily target Chinese-speaking individuals using fake websites that look like Google Chrome, Telegram, and AI tools like DeepSeek to spread ValleyRAT.
According to Chinese cybersecurity firm Antiy, this group has been around since the second half of 2022, targeting domestic users and companies in an attempt to steal secrets and commit fraud.
"The cybercriminal group mainly spreads malicious files through instant messaging software (WeChat, Enterprise WeChat, etc. ), search engine SEO promotion, phishing emails, etc.," Antiy said. "The 'SwimSnake' cybercriminal group is still frequently updating malware and AV evasion methods."
They use trojanized open-source software, malicious programs built with the Qt framework, or MSI installers disguised as Youdao, Sogou AI, WPS Office, and DeepSeek to deliver Valley RAT, including its online module for capturing screenshots of WeChat and online banking activity.
QiAnXin also reported a separate campaign by Silver Fox's "Finance Group," targeting financial personnel and managers to steal sensitive financial information or commit fraud.
These attacks use phishing lures disguised as tax audits, electronic invoices, subsidy announcements, and personnel transfers to trick users into running remote access trojans. They also use legitimate cloud services like Alibaba Cloud OSS and Youdao Cloud Notes to host malicious payloads, making them harder to detect.
The Finance Group is just one of four sub-groups within Silver Fox, the others being the News and Romance Group, the Design and Manufacturing Group, and the Black Watering Hole Group.
What's truly alarming is how the Finance Group operates after gaining control of a victim's computer. They hijack social media accounts and send phishing QR codes to WeChat groups, attempting to steal bank account numbers and passwords to drain funds.
"UTG-Q-1000 is one of the most active and aggressive cybercrime groups in China in recent years. Their operations are highly organized, technically sophisticated, and financially motivated," QiAnXin said. "They've established a complete black-market profit chain involving: espionage (data theft), remote control via malware, and financial fraud and phishing."




