Ukrainian Network Suspected in Wave of VPN and RDP Hacking Attempts
A Ukrainian-based IP network is under scrutiny after researchers detected a significant surge in brute-force and password-spraying attacks aimed at SSL VPNs and Remote Desktop Protocol (RDP) devices. The malicious activity, observed between June and July 2025, raises concerns about potential widespread compromise of vulnerable systems.

Cybersecurity researchers are sounding the alarm about a Ukrainian IP network. They've spotted it engaging in massive brute-force and password spraying campaigns. The targets? SSL VPN and RDP devices, and this activity was happening between June and July of 2025.
According to Intrinsec, a French cybersecurity firm, the activity seems to be coming from FDN3 (AS211736), an autonomous system based in Ukraine.
"We're pretty sure that FDN3 is part of a larger, problematic infrastructure," Intrinsec said in a report released last week. This infrastructure supposedly includes two other Ukrainian networks, VAIZ-AS (AS61432) and ERISHENNYA-ASN (AS210950), plus a Seychelles-based autonomous system called TK-NET (AS210848).
Here's the kicker: "These networks were all allocated in August 2021. They often swap IPv4 prefixes to avoid getting blacklisted, allowing them to keep hosting these abusive activities."
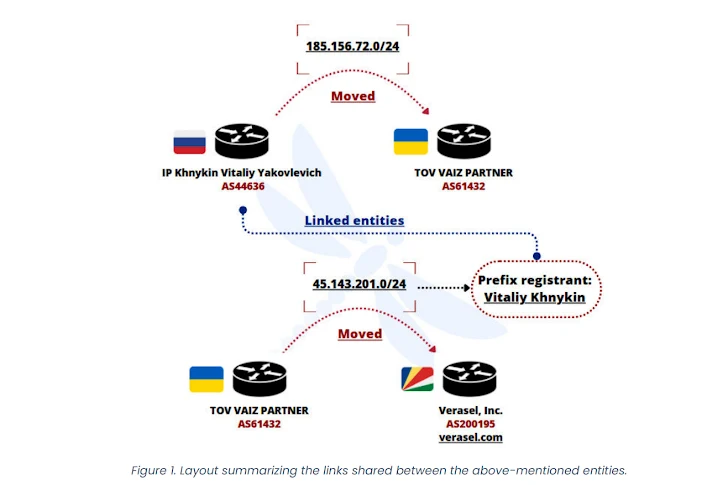
Currently, AS61432 announces a single prefix: 185.156.72[.]0/24. AS210950 has two: 45.143.201[.]0/24 and 185.193.89[.]0/24. These autonomous systems were created in May and August 2021, respectively. A significant portion of their prefixes is announced on AS210848, another autonomous system that also popped up in August 2021.
Intrinsec points out: "This network shares all its peering agreements with IP Volume Inc. – AS202425. This company, based in Seychelles, was created by the owners of Ecatel. Ecatel has a notorious reputation for running a bulletproof hosting service in the Netherlands since 2005."
Apparently, all the prefixes that moved from AS61432 and AS210950 are now announced by bulletproof networks and abusive networks fronted by shell companies like Global Internet Solutions LLC (gir.network), Global Connectivity Solutions LLP, Verasel, IP Volume Inc., and Telkom Internet LTD.
These findings build upon earlier reports about how multiple networks – AS61432, AS210848, and AS210950 – allocated in August 2021 and based in Ukraine and Seychelles, were being used for spam, network attacks, and hosting malware command-and-control servers. Back in June 2025, some of the IPv4 prefixes announced by these networks were shifted to FDN3, which, interestingly, was also created in August 2021.
But wait, there's more. Three of the prefixes announced by AS210848, and one by AS61432, were previously announced by a Russian network called SibirInvest OOO (AS44446). And one of the four IPv4 prefixes announced by FDN3 (88.210.63[.]0/24) is believed to have been previously announced by Virtualine (AS214940 and AS214943), a U.S.-based bulletproof hosting solution.
This particular IPv4 prefix range is what's being linked to the large-scale brute-force and password spraying attempts. The activity peaked between July 6 and 8, 2025.
Intrinsec says that these brute-force and password spraying attacks, aimed at SSL VPN and RDP assets, can last up to three days. It's important to remember that ransomware-as-a-service (RaaS) groups, like Black Basta, GLOBAL GROUP, and RansomHub, often use these techniques as a way to initially break into corporate networks.
The other two prefixes FDN3 announced in June, 92.63.197[.]0/24 and 185.156.73[.]0/24, were previously announced by AS210848, suggesting a strong operational connection. And 92.63.197[.]0/24 has ties to Bulgarian spam networks like ROZA-AS (AS212283).
"All the similarities – configuration, hosted content, and creation date – lead us to believe that these autonomous systems are operated by the same bulletproof hosting administrator," Intrinsec stated.
Further investigation into FDN3 has revealed connections to a Russian company called Alex Host LLC. In the past, Alex Host LLC has been linked to bulletproof hosting providers like TNSECURITY, which has been used to host Doppelganger infrastructure.
Intrinsec concludes: "This investigation highlights the ongoing issue of offshore ISPs, like IP Volume Inc., enabling smaller bulletproof networks through peering agreements and prefix hosting. Their offshore locations, like Seychelles, allow the owners of these companies to remain anonymous, making it difficult to directly link them to the malicious activities happening on their networks."
In related news, Censys has uncovered a connect-back proxy management system associated with the PolarEdge botnet. This botnet is currently running on over 2,400 hosts. The system is an RPX server that functions as a reverse-connect proxy gateway, managing proxy nodes and providing proxy services.
Mark Ellzey, a senior security researcher at Censys, explained: "This system appears to be a well-designed server, and it might be one of the many tools used to manage the PolarEdge botnet. It's also possible that this service is completely separate from PolarEdge and is simply a service the botnet uses to hop between different relays."




