XorDDoS Malware Campaign Widens Net to Docker, Linux, and IoT Devices
A notorious DDoS malware, XorDDoS, is escalating its attacks, security experts report. The threat, already a significant concern, now targets Docker containers, Linux systems, and IoT devices. Data reveals the United States remains a primary target, accounting for a staggering 71.3% of XorDDoS attacks between November 2023 and February 2024.
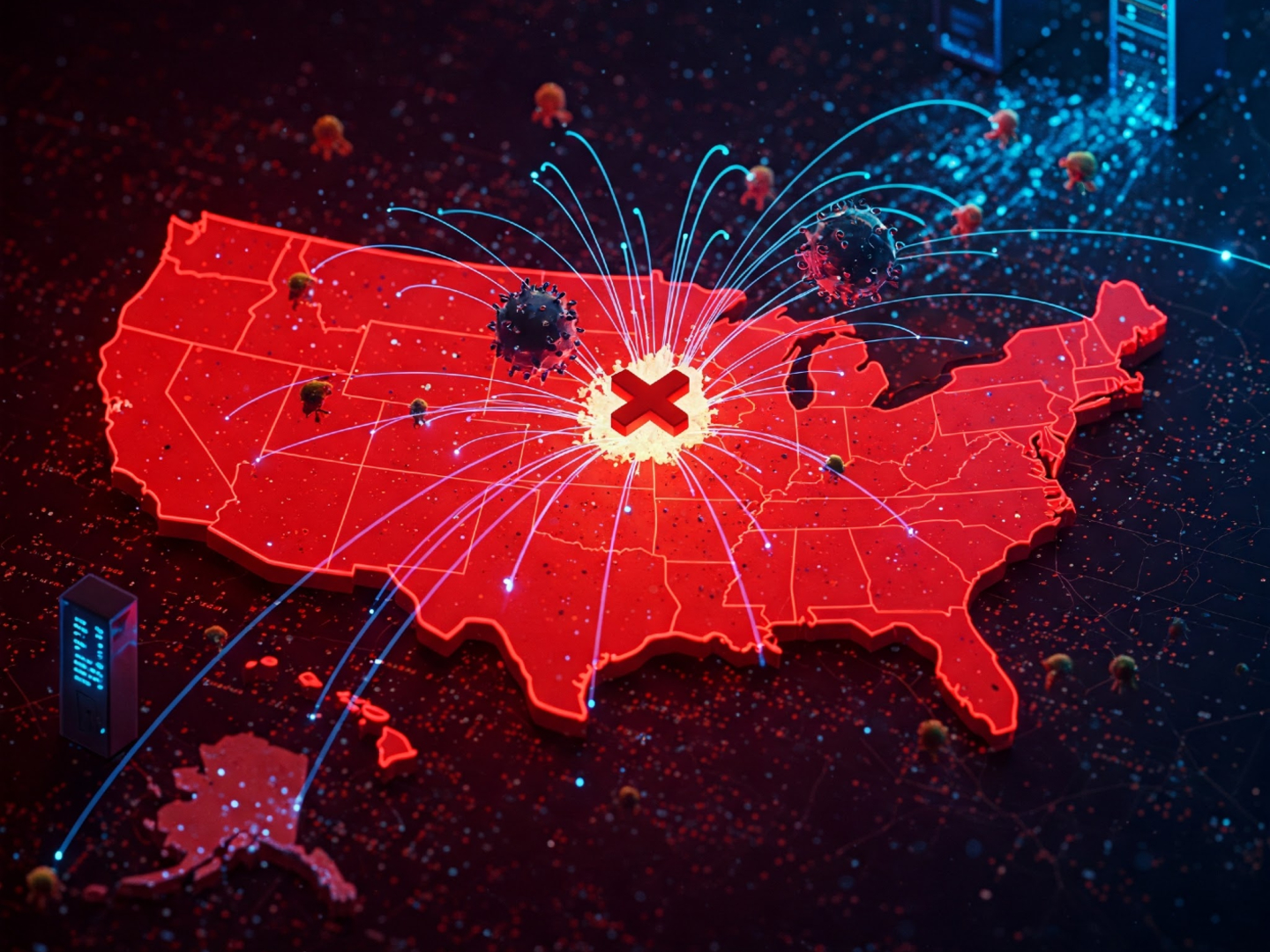
Cybersecurity experts are sounding the alarm about the persistent dangers of XorDDoS, a type of malware used in distributed denial-of-service (DDoS) attacks. Get this: a whopping 71.3% of attacks between November 2023 and February 2025 were aimed at targets in the United States.
As Cisco Talos researcher Joey Chen put it in a recent analysis: "From 2020 to 2023, the XorDDoS trojan has increased significantly in prevalence." You can read his full analysis here.
What's driving this trend? Chen explains it's not just the wide global spread of XorDDoS, but also a spike in malicious DNS requests related to its command-and-control (C2) infrastructure. And it's not just going after the usual Linux machines. This trojan is now targeting Docker servers, turning infected hosts into bots.
The U.S. is bearing the brunt, with nearly 42% of compromised devices located there. Other countries feeling the heat include Japan, Canada, Denmark, Italy, Morocco, and China.
XorDDoS isn't new to the scene. It's been targeting Linux systems for over a decade. Back in May 2022, Microsoft reported a major jump in XorDDoS activity, with these infections often leading to the installation of cryptocurrency mining malware like Tsunami.
So, how does it get in? The most common entry point is through brute-force attacks on Secure Shell (SSH) services. Once they crack the SSH credentials, they can download and install the malware on vulnerable IoT devices and other gadgets connected to the internet.
Once inside, the malware makes sure it sticks around by using an embedded initialization script and a cron job, ensuring it launches every time the system starts up. It also uses the XOR key "BB2FA36AAA9541F0" to decrypt a configuration file, pulling out the IP addresses it needs to communicate with its command-and-control servers.
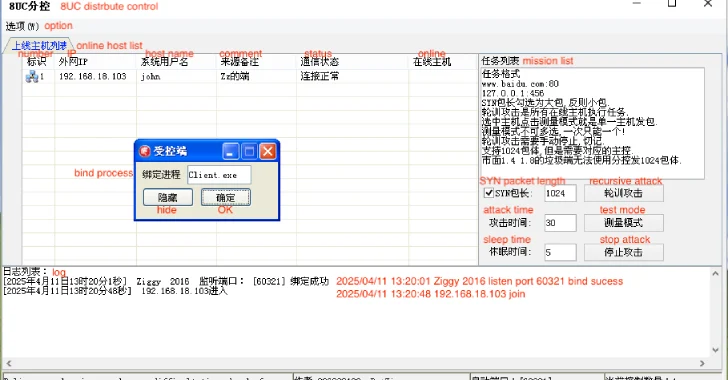
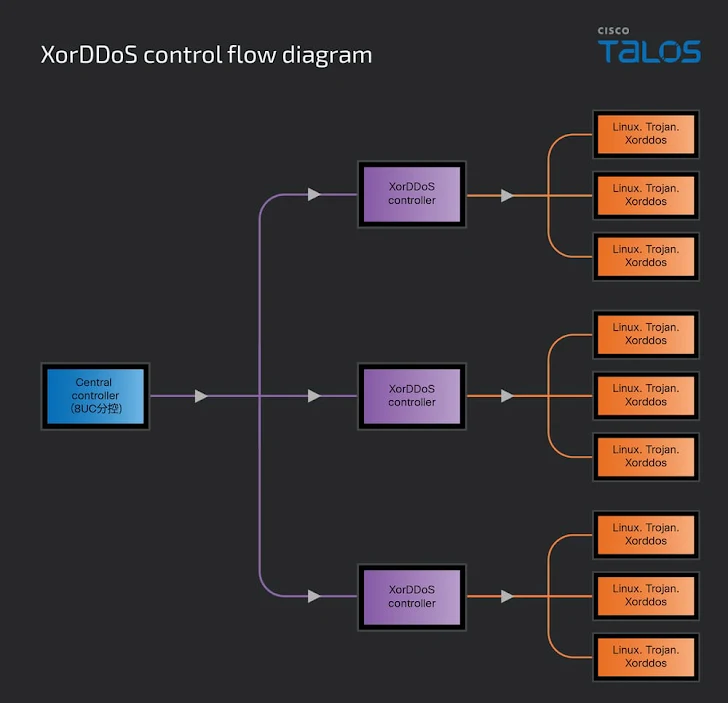
Talos also spotted a fresh version of the XorDDoS sub-controller in 2024, dubbed the VIP version, along with its main controller and a builder tool. This suggests the malware is likely being sold as a service.
The central controller is like the boss, managing multiple XorDDoS sub-controllers and sending out DDoS commands. Each of these sub-controllers then directs a botnet of infected devices.
According to Chen, "The language settings of the multi-layer controller, XorDDoS builder, and controller binding tool strongly suggest that the operators are Chinese-speaking individuals."




